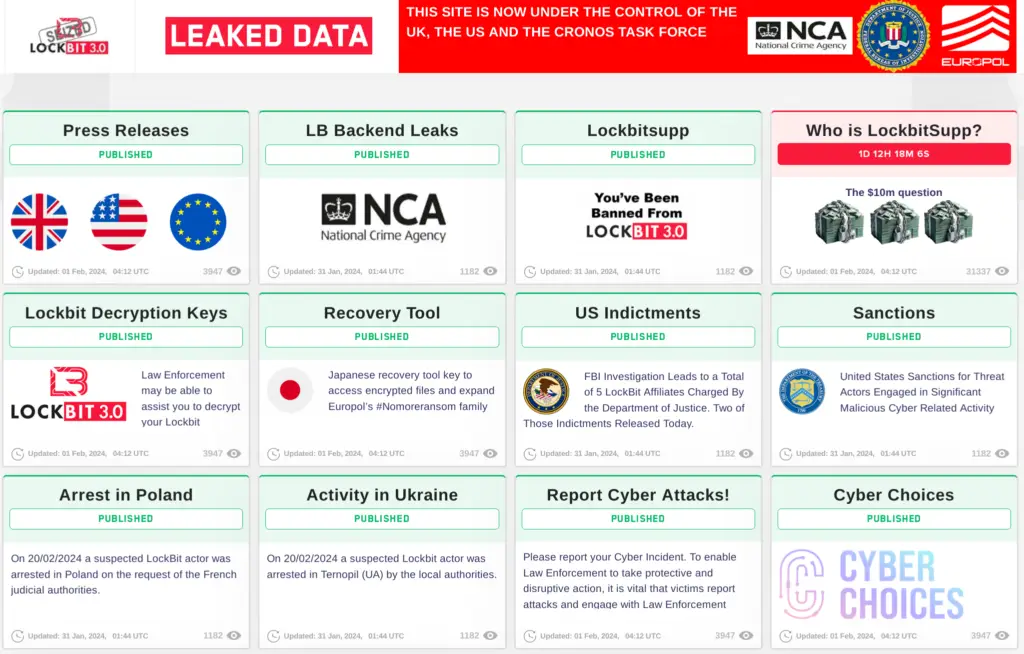
The National Crime Agency (NCA ) of the United Kingdom took control of LockBit’s main website late on February 19, 2024, making it the most active ransomware organization in recent memory. The NCA has taken control of the physical servers that run the main site and has detained two men—one in Poland and the other in Ukraine—along with their international law enforcement partners at the US FBI, the French Gendarmerie National, Europol, and other organizations. The US also announced sanctions against two Russian nationals for their involvement in the criminal syndicate on the same day.
We learn new things about how these organized crime groups function as a result of this kind of coordinated, global law enforcement action, and we are also made aware of some of the restrictions we can put in place.
Let’s start with the fundamentals: What constitutes a “ransomware syndicate” exactly? They frequently seem to resemble an anarcho-syndicalist commune. Typically, that entails a core team of software developers who create the websites, malware, and payment sites, someone who can defraud people of money, as well as an English-speaking translator to negotiate settlements with the victims. The so-called “affiliates” carry out the actual attacks themselves. These affiliates register to extort money from victims using the platform and brand name.
In the criminal underworld, identity is a fluid concept.
The structure of these “groups,” which are primarily loosely affiliated and operate under a brand name, is our first issue. The core group members themselves may not be affected if the brand is shut down. The brand” LockBit” is effectively dead as a result of the US enforcing sanctions against some of its members. No US-based organization will be willing to pay LockBit a ransom; however, if they reappear tomorrow under the name CryptoMegaUnicornBbit or another similar name, the cycle will begin again.
It is very challenging to deny these people their income while using a new name. LockBit has been destroyed by the sanctions imposed today on Ivan Kondratyev and Artur Sungatov ( the sanctioned Russian nationals ), but how will victims be able to recognize them when they reappear as DatasLaYeR001 and Crypt0Keeper69?  , the sanctions are merely temporary fixes for the ransomware issue.
The US Department of Justice’s ( DOJ) five indictments are probably just the start. The only indictments of this kind in the past were made public for people living in nations where the US is unlikely to cooperate with law enforcement; if not, it will be added to the list of sanctioned entities. If other identified participants make the error of traveling abroad on a holiday, it is hoped that there are still more sealed indictments lurking, unknown to their subjects at the moment. In Poland ( for money laundering ) and in Ukraine (unspecified ), members of the LockBit crime family who were in law enforcement-friendly nations were detained. They will likely face charges in France.
Security is challenging.
How were these thugs captured by law enforcement? If you believe the criminals themselves, all signs point to an unresolved security vulnerability, CVE 2023–3824. Observers had commented on LockBit’s struggle to manage their IT infrastructure andnbsp in the middle of 2023, ironically just before CVE-2023-3824 was publicly reported. Being a professional criminal hacker does not make you magically great at securing your own infrastructure.
They were probably able to physically seize the servers running the operation and start dismantling more and more of the supporting infrastructure once the web server hosting the leak site was exploited. This was a multiyear operation, according to the press. ( Remember, LockBit has been around for a while; the company first appeared in 2019; and as of February 19, 2024, according to their own file leak page, the website had been operational for 4 years and 169 days. )
This is n’t a brand-new concept or strategy. In earlier instances, we have also witnessed law enforcement “hack” criminal infrastructure, sometimes by using zero-day browser and tool vulnerabilities and other times by catching the criminals in error by failing to use a VPN or Tor Browser, resulting in their identification and capture. Even the most skilled criminals ultimately fail due to these operation security ( OpSec) mistakes.
We must improve law enforcement’s capacity to carry out these operations if we want to keep applying pressure to these groups. They are crucial to undermine the co-conspirators ‘ faith in the security of their participation as well as to destroy the infrastructure used in these attacks. To approve these operations, we need more qualified, well-paid cyber-cops as well as a more knowledgeable judiciary.
Sadly, despite their success, the NCA and their partners have n’t completely turned off the Lockbit network. The group still uses a number of dark websites, the most damaging of which hosts stolen content from victims to expose them as retaliation for their lack of payment. Before the takedown, the damage had already been done, but their agreement was still incomplete.
attitude, boasting, and bluster
The NCA’s “epic trolling” in seizing and reviving the LockBit leak site has been the subject of comments on social media. Was this merely a show of bravado, or did the police and decision-makers have other reasons as well? I’m not sure the answer, but I have a sneaking suspicion that this is intentional.
Figure 1: The takedown page is educational and indicates that more excitement will follow.
According to experience, many of the criminal puppeteers behind these crimes—though not all—are located in nations that are unable or unwilling to enact laws against organizations that target Western victims. Many of their affiliates are also well aware that they are not as well-protected as the group leaders.
The supporting actors might be discouraged from taking part by creating a scene and instilling fear, uncertainty, and doubt about whether their communications, identities, or tools are being watched or have already been compromised. Criminal gangs have long harbored the well-founded fear that researchers and law enforcement have compromised them. They’re correct. We are observing them from among them. The NCA’s orchestrated trolling and exposure emphasizes that we are in you.
We have faith in criminals?
Numerous victims have claimed that they paid the ransom in order to prevent the disclosure of their customers’, staff’s, and shareholders ‘ data. Since the beginning of the crime itself, experts have criticized the notion that paying extortionists to delete stolen data is a workable strategy. The NCA confirmed our suspicions that the perpetrators may have wanted to use or monetize the stolen data by keeping copies of it. No honor among thieves,nbsp.
Not our belief that the criminals are trustworthy, but rather how can we instill this mistrust in their own operatives, is probably more crucial in this situation. Can we create a climate where the criminals themselves are unsure of who to trust? Our own skepticism and the US sanctions should be enough to make almost any of us pause.
This might serve as our best deterrent, in my opinion. In order to demonstrate that what appears to be happening in the dark is likely on many people’s radar, researchers and others should continuously expose chats, forums, and other access they have gained on public forums. This should go beyond the strut and expose that the NCA, FBI, Europol, etc. do after a takedown.
finalizing ideas
When the world is heading toward an increasingly balkanized state, we wo n’t arrest or imprison our way out of this. With the maturity of our strategy, I believe we are approaching a turning point. We are applying pressure where it matters and, in the end, using the leverage we have at our disposal to apply disciplinary approaches on all fronts.
Ransomware will continue to exist, and many members of the LockBit cartel may even resume their active participation as a result of this event. It advances our strategy for dismantling these groups, raises their operating costs, and fosters mistrust among the criminals themselves.
We may be on the verge of the turning point where the defenders have their own script after the criminals successfully developed patterns and scripts for how to systemically exploit victims. In this battle, we must take a firm stance, stand by our law enforcement partners, and work to strike them where it hurts the most. If they ca n’t form cohesive teams, they will either vanish into the sunset or turn against one another, according to the proverb. Win — win.