To send up to five million emails a day through scams and malvertising,” SubdoMailing,” a massive ad-fraud campaign, uses over 8, 000 legitimate internet domains and 13, 000 subdomains.
The threat actors use abandoned subdomains and domains owned by well-known companies to send their obtrusive emails under the name” SubdoMailing.”
Because these domains belong to reliable individuals, they can decipher spam filters and, in some cases, take advantage of configured SPF and DKIM email policies, which alert secure email gateways to the emails as legitimate and not spam.
MSN, VMware, McAfee, The Economist, Cornell University, CBS, NYC, and other well-known brands have all been victims of this domain-hacking scam. gov, PWC, Pearson, Better Business Bureau, Unicef, ACLU, Symantec, Java, and PWC. Marvel, eBay, and.  ,
These well-known companies unintentionally give the phony emails legitimacy and pass through security checks.
Users are directed through a number of redirections when they click the embedded buttons in the emails, which the threat actors do because of erroneous ad views. In the end, the user is presented with affiliate scams, scams, surveys, security checks, or fake giveaways.
The ad-fraud campaign was discovered by Guardio Labs , and researchers Nati Tal and Oleg Zaytsev have reported that the operation has been running ever since 2022.
Source: Guardio Labs,  
spamming domains by stealing them
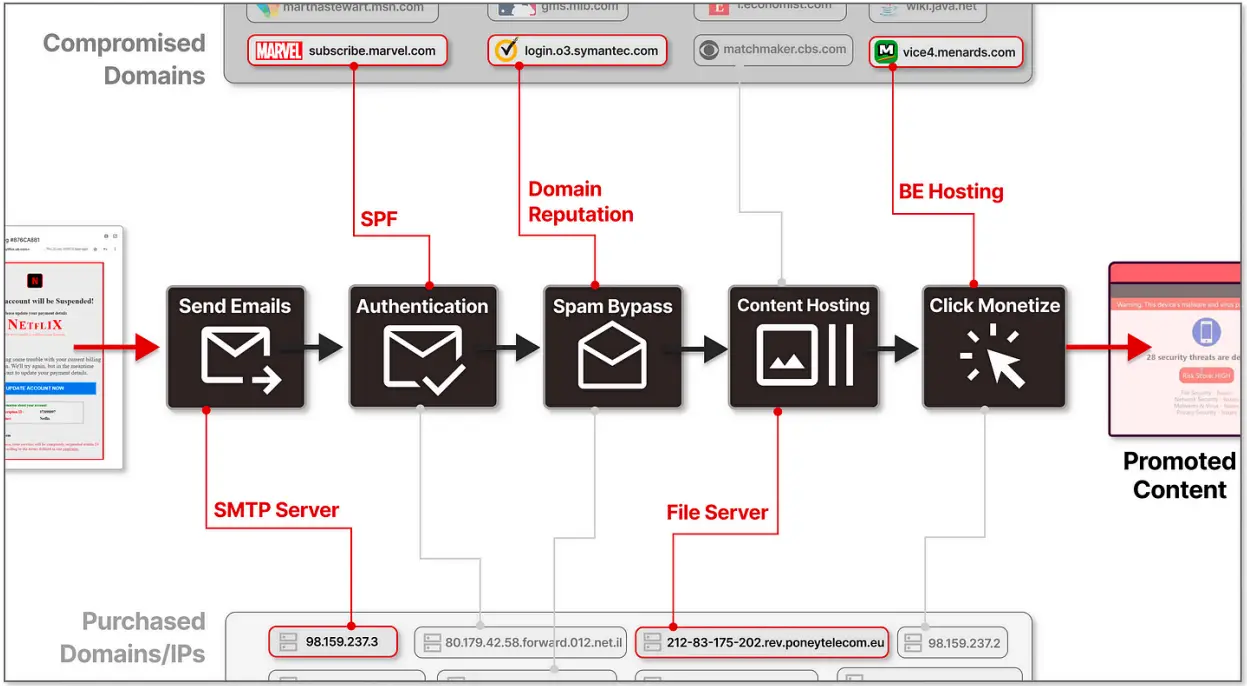
A vast subdomain hijacking operation was the focus of Guardio Labs ‘ investigation, which began with discovering unusual patterns in email metadata.
The attackers can use a variety of methods to make their emails appear legitimate and avoid blocking blocks, including using DKIM, DKIM, and DMARC ( Domain-based Message Authentication, Reporting, and Conformance ) protocols.
These email policies are intended to demonstrate to secure email gateways that an email sender is legitimate and not spam.
Source: Guardio Labs,  
The SubdoMailing campaign targets reputable organizations ‘ domains and subdomains, attempting to steal them primarily through CNAMEhijacking and SPF record exploitation.
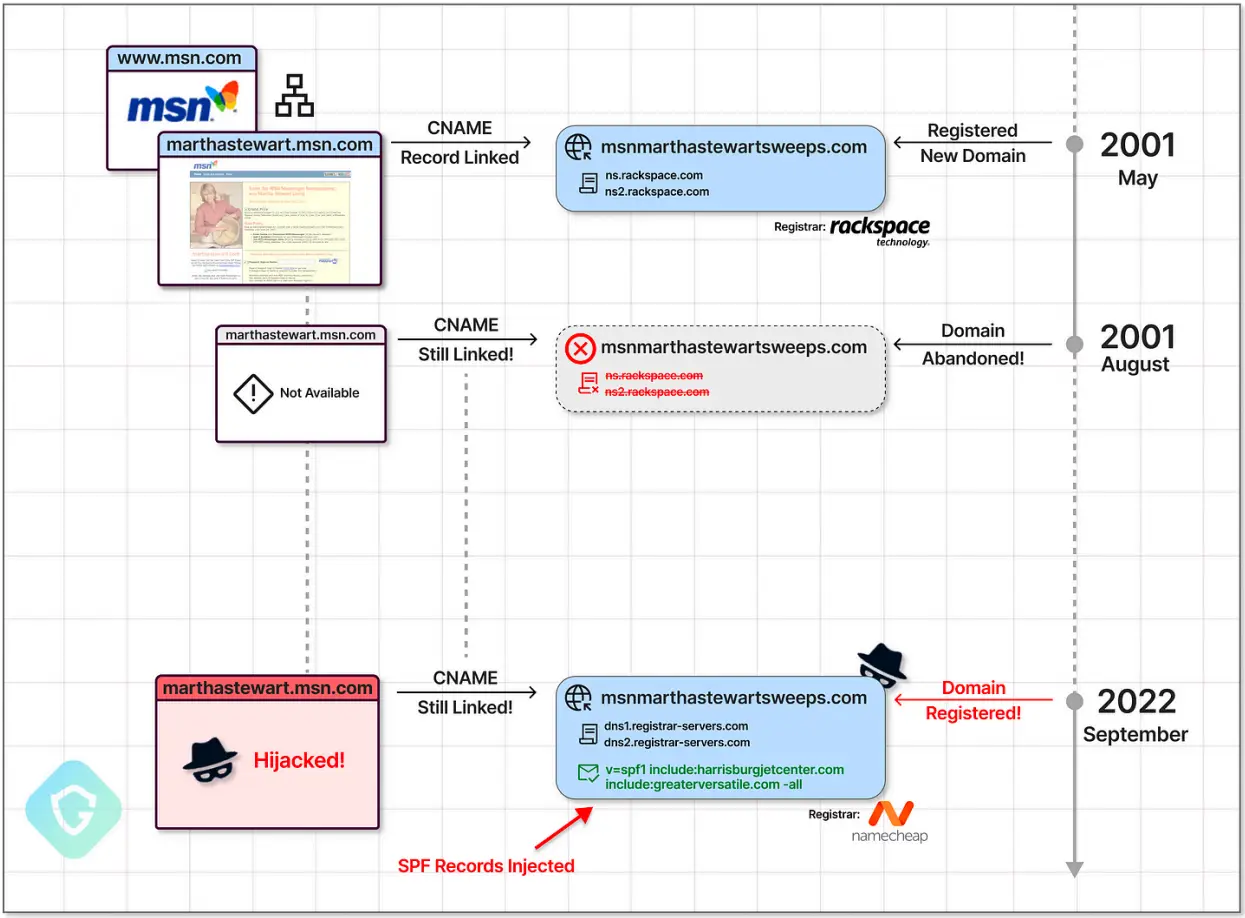
The threat actors use CNAME records to search for subdomains of reputable brands when they perform CNAME searches for unregistered external domains. The NameCheap service then allows them to register these domains for themselves.
Source: Guardio Labs,  
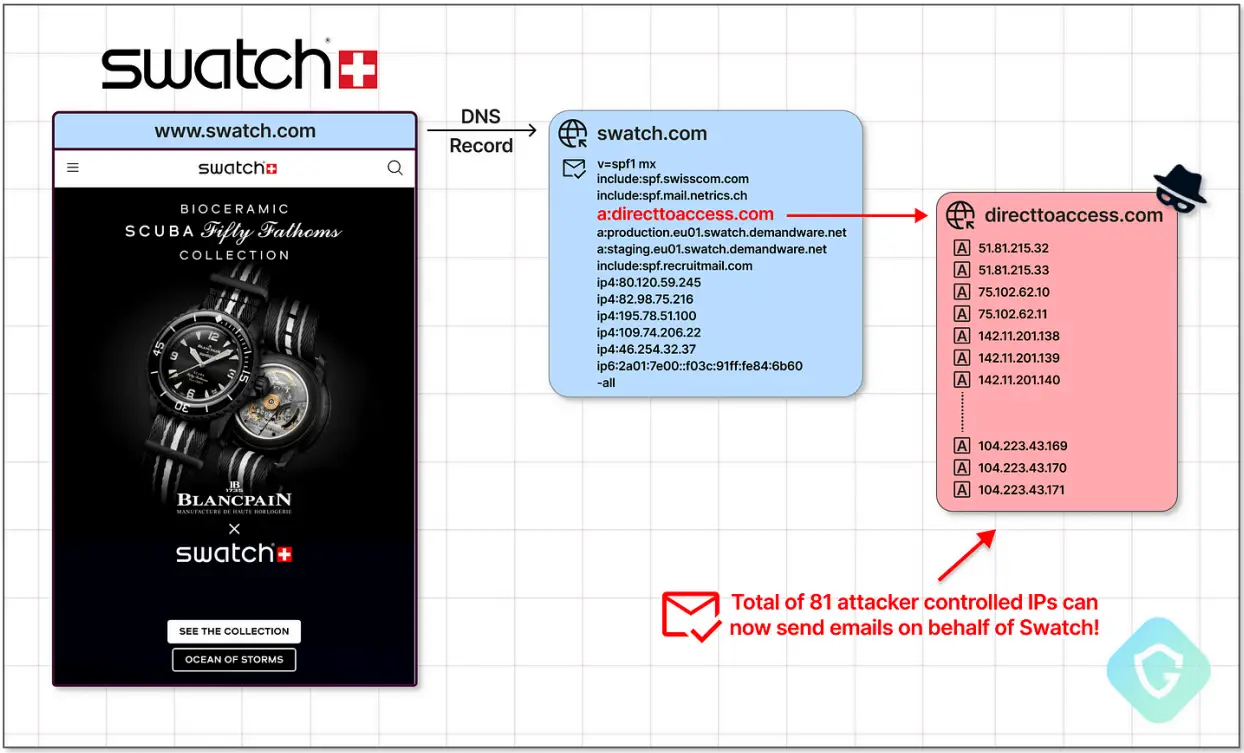
The second approach involves looking at target domains ‘ SPF records for the” configuration option pointing to external domains that are no longer registered.
The threat actor is now in charge of the external domain, which is where the SPF include option is used to import the permitted email senders.
The attackers then change these SPF records to authorize their own malicious email servers after registering these domains. The threat actor’s emails now appear to be coming from reputable sources, like MSN.
Source: Guardio Labs,  
The hijacked domains are typically used to host phishing websites, send spam and phishing emails, or host deceptive advertising content.
a massive campaign
ResurrecAds, a threat actor that Guardio Labs calls” the campaign,” says he routinely searches the web for domains that can be hijacked, secures new hosts and IP addresses, and purchases targeted domains.
To maintain the scale and complexity of the operation, the threat actor constantly updates a sizable network of SMTP servers and IP addresses.
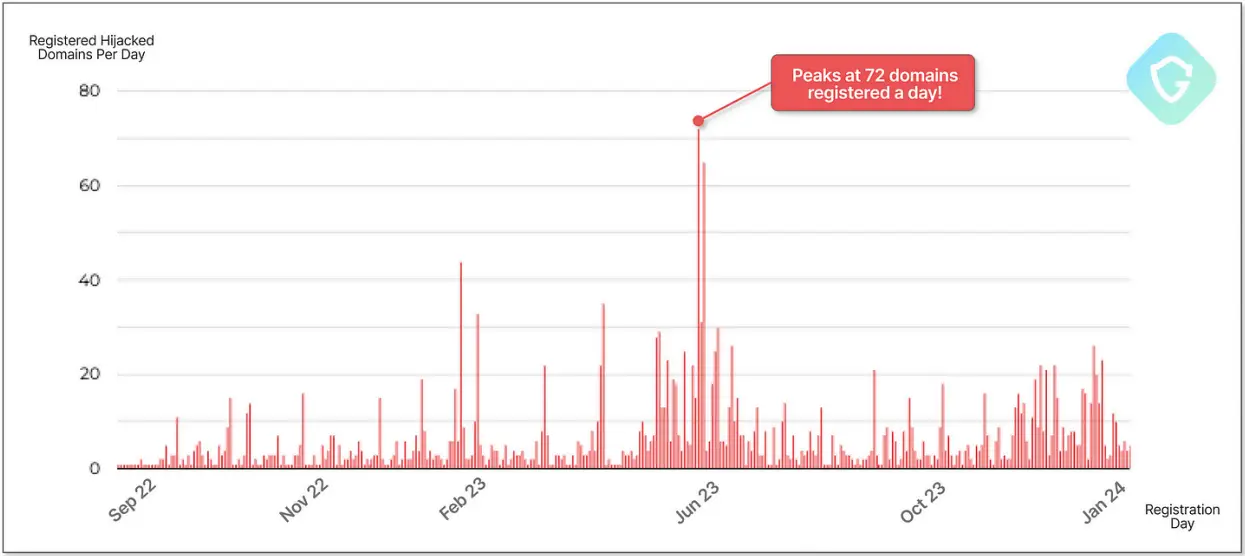
Source: Guardio Labs,  
Nearly 22, 000 unique IPs, according to Guardio Labs, are used by SubdoMailing, which appear to be residential proxies, among them.
The campaign currently uses SMTP servers that are distributed globally and have a network of 8, 000 domains and 13, 000 subdomains that are configured to filter out phony emails.
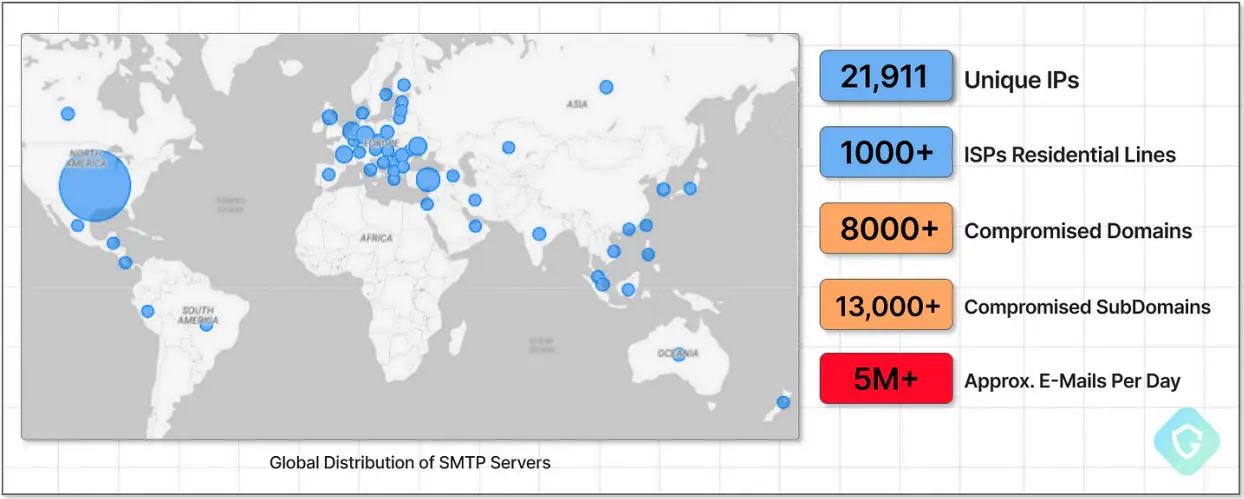
Source: Guardio Labs,  
More than 5,000 emails are sent to targets each day. Although it is impossible to determine the attacker’s financial gain from this, the fraudulent emails ‘ scale and volume are unquestionably significant.
Domain owners can be notified via a , SubdoMailing , checker site that allows them to determine whether their brand is being abused and take steps to stop or stop it.











