N. Hanacek/NIST for credit
Since its debut almost ten years ago, the top cybersecurity advice in the world is receiving its first thorough overhaul.  ,
The National Institute of Standards and Technology ( NIST ) has released a new version of the Cybersecurity Framework ( CSF ) 2.0 tool to assist organizations in understanding, reducing, and communicating about cybersecurity risk after consulting with community feedback for more than one year. For all organizations, the draft update, which NIST has made available for public comment, simplifies putting the CSF into practice by reflecting changes in the cybersecurity landscape.  ,
According to Cherilyn Pascoe, the lead developer of the Cybersecurity Framework at NIST,” With this update, we’re trying to reflect current usage and anticipate future usage as well.” The CSF was created to support vital infrastructure, such as the banking and energy sectors, but it has proven to be helpful to local and international governments as well as schools and small businesses. We want to ensure that it is a tool that can be used in all industries, not just those that are deemed essential.
Until November 4, 2023, NIST will accept public feedback on the draft framework. There wo n’t be another draft released by NIST. The public will have another chance to offer suggestions and comments on the draft at a workshop scheduled for the fall that will be announced soon. Early in 2024, the developers intend to release the finished CSF 2.0 version.  ,
For managing cybersecurity risk across sectors and facilitating communication between technical and nontechnical staff, the CSF offers high-level guidance, such as a common language and systematic methodology. It includes activities that can be customized to fit the unique needs of an organization and integrated into cybersecurity programs. The CSF has been translated into at least nine languages and downloaded more than two million times in the ten years since it was first released.
Many respondents suggested that an update could help users adapt to technological innovation as well as a rapidly changing threat landscape, despite the fact that NIST’s February 2022 request for information about the CSF indicated that the framework continues to be an effective tool for reducing cybersecurity risk.  ,
According to Pascoe, “many commenters said that we should uphold and expand on the CSF’s key characteristics, such as its adaptable and voluntary nature.” Many of them also asked for more advice on how to implement the CSF and ensure that it could deal with new cybersecurity risks like supply chain vulnerabilities and the pervasive threat of ransomware. We realized we needed to step up our game because these problems affect many organizations, including small businesses.
Numerous significant changes are reflected in the CSF 2.0 draft, including:  ,
- The framework’s scope has been explicitly expanded to include cybersecurity for all organizations, regardless of type or size, as well as protecting critical infrastructure like hospitals and power plants. The CSF’s official name,” The Cybersecurity Framework,” has been changed from the more constrictive” Framework for Improving Critical Infrastructure Cryptosecurity,” and nbsp, to reflect this difference.
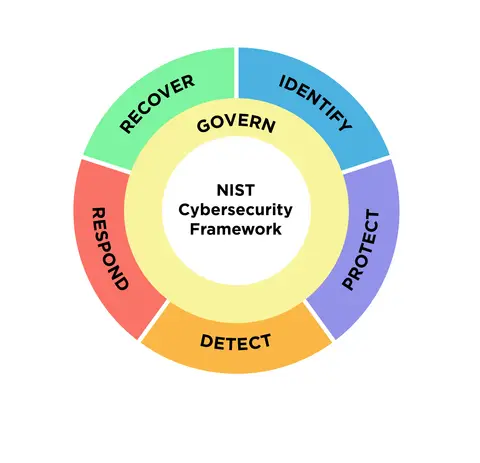
- The CSF has so far outlined the five key components of a successful, all-encompassing cybersecurity program: identify, protect, detect, respond, and recover. The govern function, which describes how an organization can choose and carry out its own internal actions to support its cybersecurity strategy, has now been added to these byNIST. It emphasizes that senior leadership should take cybersecurity into account along with legal, financial, and other risks because it is a significant source of enterprise risk.  ,
- In particular for creating profiles that tailor the CSF to specific circumstances, the draft offers improved and expanded guidance on how to use it. Profiles can assist in using cybersecurity for particular economic sectors and use cases, according to requests from the cybersecurity community. To assist organizations, particularly smaller businesses, in using the framework efficiently, the draft now includes implementation examples and nbsp for each function’s subcategories.
Explaining how organizations can apply other technology frameworks, standards, and guidelines from NIST and elsewhere is one of the main objectives of CSF2.0. The introduction of the CSF 2.0 Reference Tool supports this most recent effort. Users of   can browse, search for, and export CSF Core data in formats that are both human- and machine-readable. In order to make it simpler to use the framework and other guidance to manage cybersecurity risk, this tool will in the future offer” Informative References” to demonstrate the connections between the CSF and various resources.
According to Pascoe, the development team is urging anyone with suggestions for the updated CSF to comment by November 4th.  ,
She stated that this is a chance for users to comment on the CSF 2.0 draft. ” If you have n’t already, this is the time to get involved.”
Editor’s note ( Aug. 23, 2023 ): The CSF 2.0 Reference Tool, which was initially mentioned as an upcoming feature, is now accessible.  ,