Malware for the Android phone was downloaded 150 000 times from Google Play
By infecting Android devices with malware droppers hosted on Google Play, the Anatsa banking Trojan has been aimed at European users.
Security researchers have identified five malware delivery campaigns over the past four months that are targeted at users in the Czech Republic, Slovakia, Slovenia, Germany, and the UK.
Since November, at least 150 000 infections have been reported, according to researchers at the fraud detection company ThreatFabric.
Each attack wave targets a particular geographic area and uses dropper apps designed to enter Google Play’s” Top New Free” categories, giving them credibility and boosting their success rate.
According to ThreatFabric’s report , the dropper apps now use a multi-staged infection process and have evolved to take advantage of the Accessibility Service on Android in order to get around security restrictions in up to Android 13 versions.
ThreatFabric forewarned of a new Anatsa campaign last summer that targeted Europe and made use of dropper Google Play apps, mostly fake PDF viewer apps.
Dropper apps like Anatsa and nbsp
The malware developers ‘ most recent Anatsa campaign makes use of the fake cleaner apps PDF and  , which claim to free up space on the device by removing extra files.
The app” Phone Cleaner- File Explorer,” which received over  , 10,000 downloads, is one example that ThreatFabric’s researchers highlight.
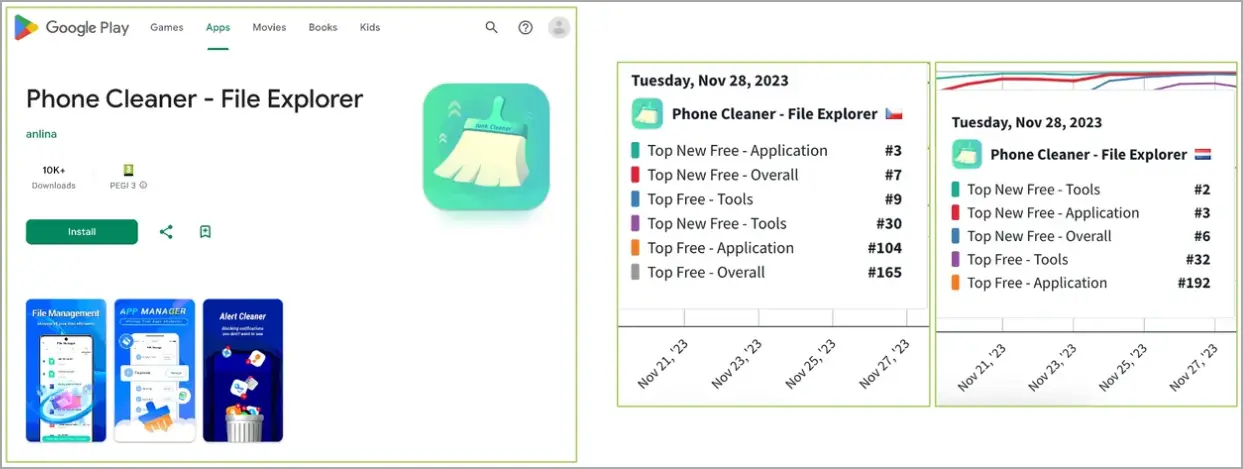
According to ThreatFabric, one Anatsa campaign also used the” PDF Reader: File Manager” app, which received more than 100,000 downloads, according to BleepingComputer .
Except for the PDF Reader, which is still accessible, Google had removed all Anatsa dropper apps from the official Android store at the time of writing.

The 150, 000 download count for Anatsa droppers on Google Play andnbsp, according to ThreatFabric researchers, is a conservative estimate, and given that they used the lower estimates, the actual number would be closer to 200,000.
The following five apps are malicious:
- File Explorer ( com ) PhoneCleaner volabs. ( Android Cleaner )
- File Explorer , PDF Viewer, ( com ) xolab. ( File Explorer )
- Editor ( com ), Viewer &, and PDF Reader. jumbodub. ( File Explorer, PDF Viewer )
- File Explorer , ( com ) is a phone cleaner. iClouds ( Cleaner )
- File Manager ( com ) is a PDF reader. Tragisoap. ( fileandpdfmanager )
The number of downloads is anticipated to rise further given that Anatsa frequently introduces new attack waves using brand-new dropper apps,the . Already, it has surpassed Anatsa ’s 130, 000 accomplishments from the first half of 2023.
technical information
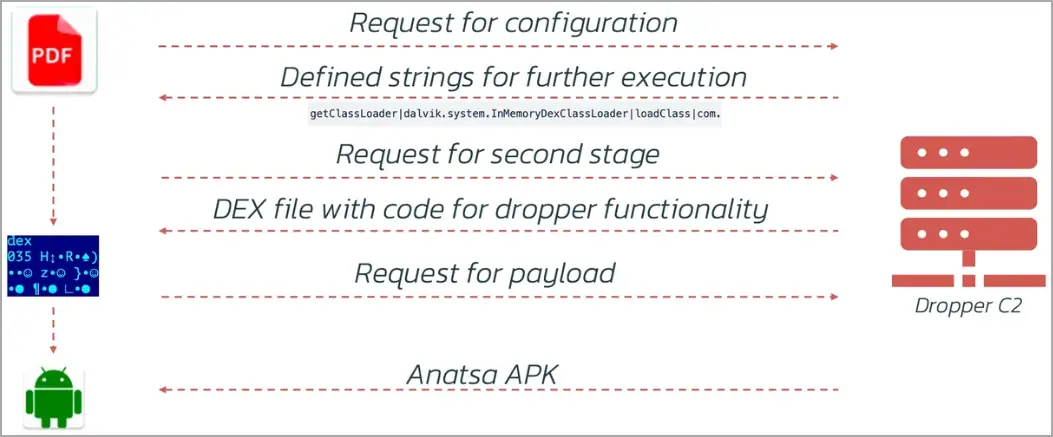
The dropper apps dynamically download malicious components from a command and control ( C2 ) server in order to avoid detection, according to technical insights from ThreatFabric’s report.
A notable tactic involves using AccessibilityService—a malware vector in the past—to automate the installation of payloads without the user’s input.
Despite Google’s recent policy updates that added  restrictions to combat misuse, malware abusing this potent Android service designed to help users with disabilities happens frequently.
The need to “hibernate , battery-draining apps,” which appears to be a legitimate feature in the context of an app that is cleaner, concealed Anatsa & NBP, droppers ‘ permission to access the Accessibility Service.
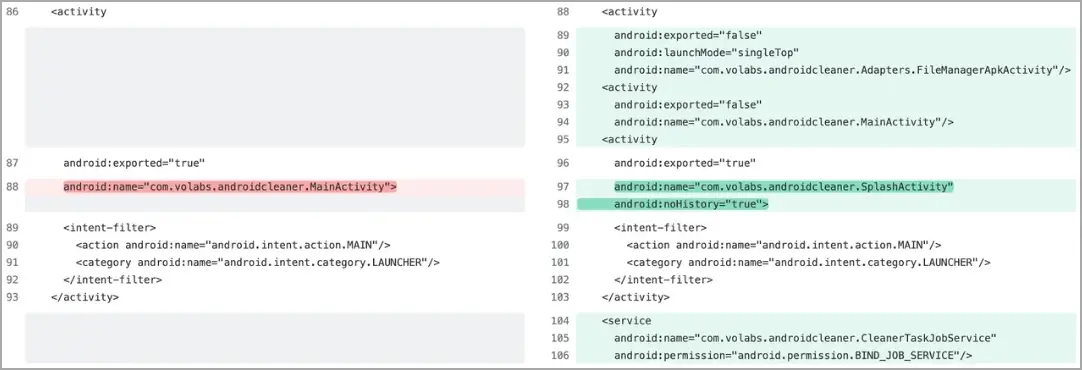
Threat Fabric discovered in one instance that the dropper app’s user interface navigation parameters match those of Samsung devices ( One UI), and the malicious code update was released a week after it was uploaded to Google Play.
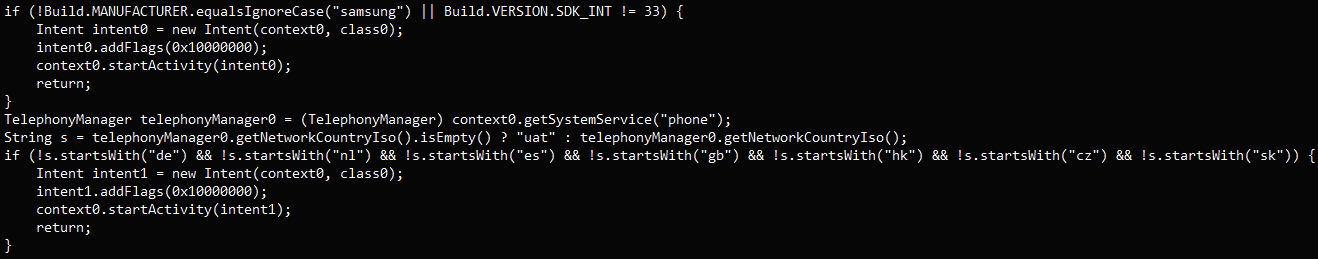
Due to the lack of vendor-specific code in other droppers used in the same campaign, a wider range of Android devices are the target audience.
Four separate steps are used to download the malicious code update from C2, likely as a strategy to avoid being found out and flagged by Google’s code review systems.
- Configuration Retrieval: By hiding suspicious indicators, configuration retrieval prevents immediate detection by downloading configuration from the C2 server that contains crucial strings for malicious code.
- Downloading a DEX file reveals malicious code that has been activated by previously downloaded strings and is in charge of installing payloads.
- Downloading a configuration file with the payload’s URL enables attackers to modify the link as necessary.
- Payload Installation: The infection process is finished by downloading, installing, and launching the Anatsa malware using the DEX file.
The Anatsa campaign’s significant growth carries a risk of financial fraud. Before installing an app, Android users are advised to carefully examine publisher and user reviews.
Avoiding performance-enhancing, productivity-boosting, and secure messaging apps that do n’t originate from vendors with a solid reputation will help you stay protected.
Checking the list of permissions requested and denying those unrelated to the app’s purpose ( e .g., a photo editing app does not require microphone access ) is strongly advised when installing new apps.
Examine the permissions that are requested when installing new apps, especially those that pertain to the Accessibility Service, as these should be considered suspicious of malware threats.
Google Play Security is bypassed by the Analytic Android Trojan, which also expands its reach to new nationscreating a Rust COM libraryGoogle Chrome(Opens in a new browser tab)How Applied Geometry and Artificial Intelligence Can Help Us Win the Race for Renewable Energy(Opens in a new browser tab)
(Opens in a new browser tab)(Opens in a new browser tab)
Users can keep their phone numbers private thanks to the signal that introduces usernames.(Opens in a new browser tab)(Opens in a new browser tab)











