SaaS has generated genuine concern in many boardroom discussions as a result of many of the highly publicized cyberattacks in 2023 centered on one or more of them. Given that GenAI applications are actually SaaS applications, this is more true than ever.
In the fourth quarter of 2023, 493 SaaS-using businesses were analyzed by Wing Security ( Wing ). Their research reveals the numerous threats that result from the widespread use of SaaS by businesses today. In addition to offering rare and significant insights into the scope and depth of SaaS-related risks, this insightful analysis also offers useful advice on how to reduce them and make sure that use of the technology is widespread without jeopardizing security posture.
The SaaS Security TL/DR Version
The North Korean group UNC4899, the 0ktapus ransomware group, and the Russian Midnight Blizzard APT, which targeted well-known organizations like JumpCloud, MGM Resorts, Microsoft ( respectively ), as well as probably many others that frequently go unnoticed, are just a few of the now notorious examples of malicious players using or directly targeting SaaS from 2023.
The initial finding from this study solidifies the idea that SaaS is the new supply chain and offers a framework for how crucial it is to ensure SAAS usage that is almost intuitive. These applications undoubtedly play a crucial role in the tools and vendors of the contemporary organization. However, the days of requiring security or IT approval for every third party with access to company data are long gone. Even in the strictest workplaces, diligent workers will look for and use quick and effective solutions to complete their tasks more quickly and effectively. Consider GenAI’s widespread use once more, and the picture will become clear.
As a result, any company that is worried about its supply chain’s security must implement SaaS security measures. A supply chain attack, according to the MITRE ATT&, CK technique” Trusted Relationships” ( T1199 ), happens when an attacker targets a vendor in order to take advantage of it and infiltrate more companies. Organizations expose themselves to supply chain risks that go beyond immediate security concerns by entrusting sensitive data to outside SaaS vendors.
Risks associated with SaaS four
SaaS is being targeted for a variety of reasons and methods. The good news is that with proper monitoring and control, the majority of risks can be significantly reduced. Organizations that are just starting to develop their SaaS security posture or need to compare it to their current solution should consider using the free, fundamental security capabilities of the platform.
Shadow SaaS, first
The first issue with SaaS usage is that it frequently goes unnoticed: Organizations typically use 250 % more applications than what a straightforward and frequently used workspace query reveals.
The following businesses were examined:
- There were a very long list of unsanctioned applications because only one person used 41 % of them.
- One out of every five users in their company was using applications that were not used by anyone else, which put security and resources under stress.
- Why keep single-user applications connected to company data when 63 % of them were not even accessed within a three-month period?
- The continuous risk and requirement for appropriate mitigation were solidified by the fact that 96.7 % of organizations used at least one application that had a security incident the year before.
2 ) Bypassing the MFA
According to Wing’s research, users are increasingly choosing to access the services they require using usernames and passwords rather than the current security measures ( see image 1 ).
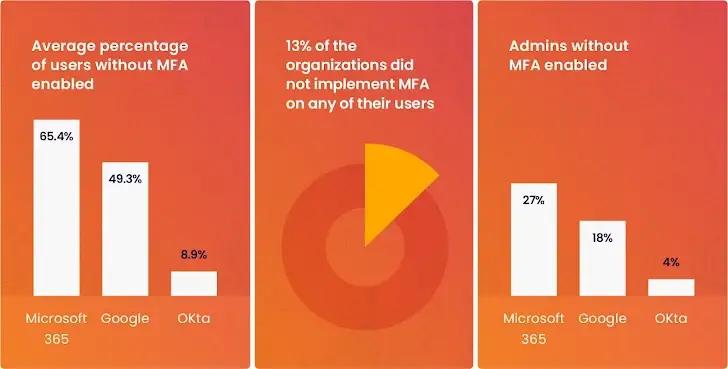 |
| Image 1: Without using MFA, from Wing Security’s research. |
3 ) Misplaced tokens
To enable SaaS applications to accomplish their goals, users must grant the applications the tokens they require. The issue is that after just one or a few uses, people frequently forget about these tokens. Over the course of three months, Wing’s research found a significant amount of unused tokens, giving many customers an unnecessarily large attack surface ( Image 2 ).
4 ) Shadow AI’s new risk
Security teams focused primarily on a small number of well-known services that provided access to AI-based models at the start of 2023. But as the year went on, thousands of traditional SaaS applications started using AI models. According to the study, 99.7 % of businesses were utilizing AI-capable applications.
In order for these applications to use and improve their models using the organizations ‘ most private data, organizations had to agree to updated terms and conditions. These updated terms and conditions, along with the use of AI itself, were frequently overlooked.
Your data may be used by AI applications in a variety of ways for their training models. To enhance the AI model, this may involve learning your data, storing it, or even having a human manually review it. Wing claims that if this capability is not disregarded, it is frequently configurable and completely avoidable.
2024: Resolving SaaS Security Issues
The report concludes with a recommendation for businesses to reduce the SaaS supply chain’s growing threat. Including:
- ongoing management and discovery of shadowIT.
- Prioritize fixing SaaS configuration errors.
- Utilize predefined frameworks to optimize anomaly detection and, when possible, automate.
- Find and keep an eye on all SaaS applications that use AI, and be sure to keep checking your SAS for any updates to T& or C that may be used with AI.
Download the complete report here for a list of all the findings, advice on ensuring secure SaaS usage, and an outlook for 2024.











