An open-source network mapping tool called  , SSH-Snake is being used by a threat actor to move laterally along the victim infrastructure while searching for hidden private keys.
The Sysdig Threat Research Team ( TRT ) made the discovery of SSH-Snake, describing it as a” self-modifying worm” that distinguishes itself from more conventionally crafted attacks by avoiding the patterns that are typically associated with them.
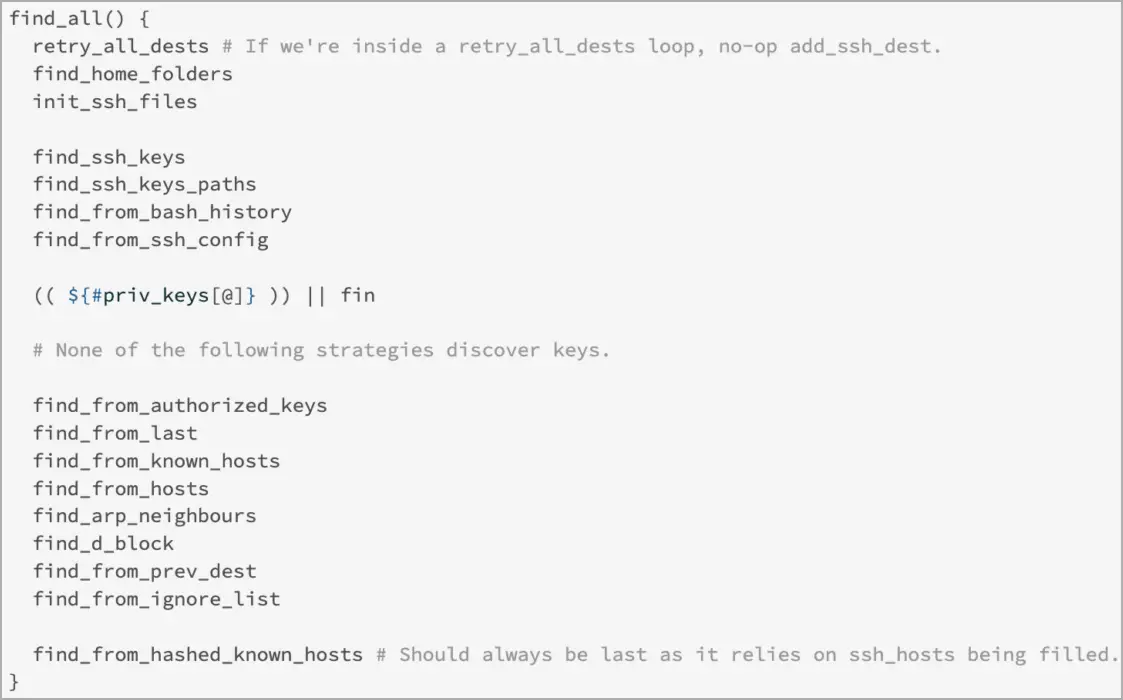
After mapping the network, the worm stealthily spreads to new systems by looking for private keys in various places, including shell history files.
For automated SSH-based network traversal, which can begin with one system and display the relationship with other hosts connected through SSS, SSHA-Snake is available as an open-source resource.
However, because SSH-Snake is more thorough in its search for private keys, researchers at the cloud security firm Sysdig claim that it elevates the conventional lateral movement concept to a new level.
SSH-Snake is a bash shell script that was released on January 4, 2024, and it is responsible for autonomously locating and utilizing sSH credentials in breached systems.
The ability of SSH-Snake to change and shrink itself when running for the first time, according to the researchers, is one of its unique characteristics. By  accomplishes this by deleting comments, superfluous features, and whitespace from its code.
SSH-Snake is plug-and-play and is made for versatility, but it can also be customized for particular operational requirements, such as finding private keys and identifying their potential uses.
To find private keys on compromised systems, SSH-Snake uses a variety of direct and indirect techniques, including:
- searching through common directories, configuration files, and other locations where SSH keys and credentials are typically kept.
- Find commands ( ssh, scp, and rsync ) that may have used or referenced SSH private keys by looking through shell history files ( e.g. ,.bash_history, etc. ).
- By parsing the bash history for commands involving SSH, SCP, and Rsync operations using the “find_from_bash_history” feature, it is possible to find out where private keys are located and what credentials they are associated with.
- analyzing network cache ( ARP tables ) and system logs to spot potential targets and gather data that could help identify and use private keys in the future.
After identifying a command and control ( C2 ) server that its users used to store information gathered by the worm, including credentials and victim IP addresses, Sysdig’s analysts confirmed SSH-Snake was operational.
The worm was deployed on these endpoints as a result of active exploitation of known Confluence vulnerabilities ( and possibly other flaws ) for initial access, according to this data.
(Sysdig)
The tool has allegedly been used offensively against about 100 victims, according to the researchers.
Because SSH-Snake targets a secure connection method that is frequently used in corporate environments, Sysdig views it as” an evolutionary step” in terms of malware.











