In a previous post, we discussed some of the differences between on-premises/physical forensics, cyber investigations, and cloud-based investigations and how they can be difficult. You can quickly deploy this pre-prepared machine to be used in an investigation thanks to the method described in that blog post for creating and maintaining a VM image that can be distributed to multiple regions. This blog explains how to obtain and access a Virtual Hard Disk ( VHD ) from an investigation-marked virtual machine (VM ) now that you have your tools.
the situation
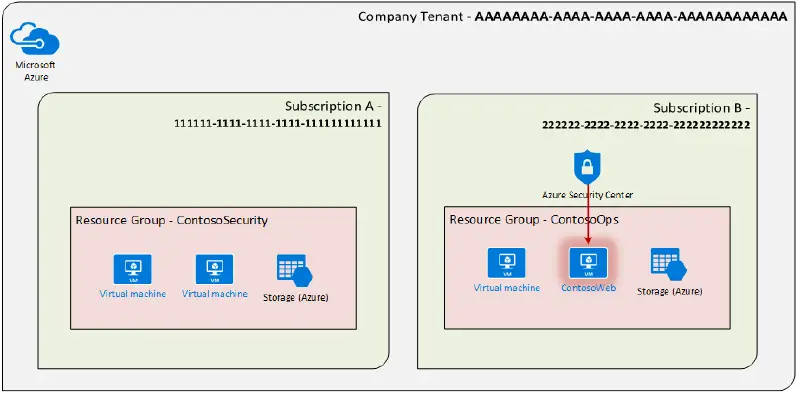
A Virtual Machine in Subscription B, within resource group ContosoOps, may have a security issue, according to an alert from Azure Security Center. On VM” ContosoWeb,” a potential web shell is present. To ascertain the event’s confidence and gather more data, we will conduct standard triage and investigative procedures. In our scenario, we’ll assume that there is a tenant with two subscriptions, each of which has its own resource group. Additionally, we assume that each tenant has permissions for the IT Security team.
acquiring a virtual machine
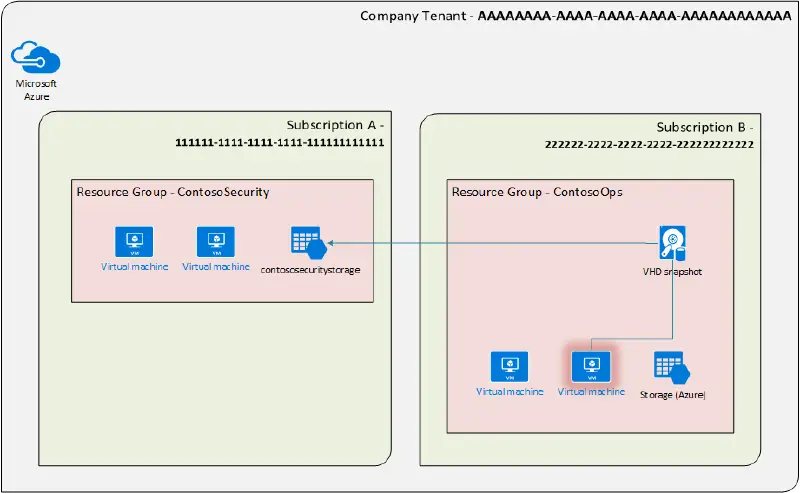
Now, in order to conduct analysis, we would like to obtain the VHD connected to the VM” ContosoWeb.” In order to do this, we must obtain a VHD snapshot for” ContosoWeb” and upload that snapshot to the storage account where it will be looked into.
First, take a disk snapshot.
We must choose the kind of storage container in which to store the snapshot before we can take a snapshot. This can be done with a variety of storage containers, including Azure Blobs, Azure File, and Azure Disks. We’ll pick a File container because we’re making the snapshot to look into it. Without having to copy the file multiple times, this will enable us to connect to the container over the network and investigate it.
As shown here and described below, we can snapshot the disk using Azure PowerShell Cmdlets and copy it to a file.
######################################### Variables #########################################$srcSubId='222222-2222-2222-2222-222222222222'#the sub containing the VM$destSubId='111111-1111-1111-1111-111111111111'#the sub containing the storage account being copied to.$srcRGName='ContosoOps'#The Resource Group containing the VM$destRGName='ContosoSecurity'# The Resource Group containing the storage account being copied to.$vmName='ContosoWeb'#Name of the snapshot being created$srcLocation='westus'#location/region of the VM being snapshot$dstLocation='westus'#location/region of the storage account$SnapshotName='ContosoWeb-Snapshot'#the name of the snapshot to be created$destSA='contososecuritystorage'#name of the storage account$destSAContainer='investigations'#name of the share within the storage account#################################################################################################################################### Login to Azure ######################################Login-AzureRmAccount-ErrorActionStop########################################################################################################################## Snapshot the OS Disk of target VM #############################Select-AzureRmSubscription-SubscriptionId$srcSubId$vm=Get-AzureRmVM-ResourceGroupName$srcRGName-Name$vmName$disk=Get-AzureRmDisk-ResourceGroupName$srcRGName-DiskName$vm.StorageProfile.OsDisk.Name$snapshot=New-AzureRmSnapshotConfig-SourceUri$disk.Id-CreateOptionCopy -Location$srcLocationNew-AzureRmSnapshot-ResourceGroupName$srcRGName-Snapshot$snapshot-SnapshotName$SnapshotName################################################################################################################## Copy the snapshot from source to file container #######################$snapSasUrl=Grant-AzureRmSnapshotAccess-ResourceGroupName$destRGName-SnapshotName$snapshotName-DurationInSecond7200-AccessReadSelect-AzureRmSubscription-SubscriptionId$srcSubId$targetStorageContext=(Get-AzureRmStorageAccount-ResourceGroupName$destRGName-Name$destSA).ContextStart-AzureStorageFileCopy-AbsoluteUri$snapSasUrl.AccessSAS-DestShareName$destSAContainer-DestContext$targetStorageContext-DestFilePath$SnapshotName-Force##############################################################################################The original Resource Group, in this instance” ContosoOps,” will still contain the snapshot. The following command can be used to remove it if you want to keep your resource groups organized:
Remove-AzureRmSnapshot -ResourceGroupName $srcRGName -SnapshotName $SnapshotName -ForceFinally, we have the option of creating a second copy of the VHD in blob storage or another storage space. Insert the following (adding the appropriate variables ) at line 31 of the script above to create a copy in both blob and file:
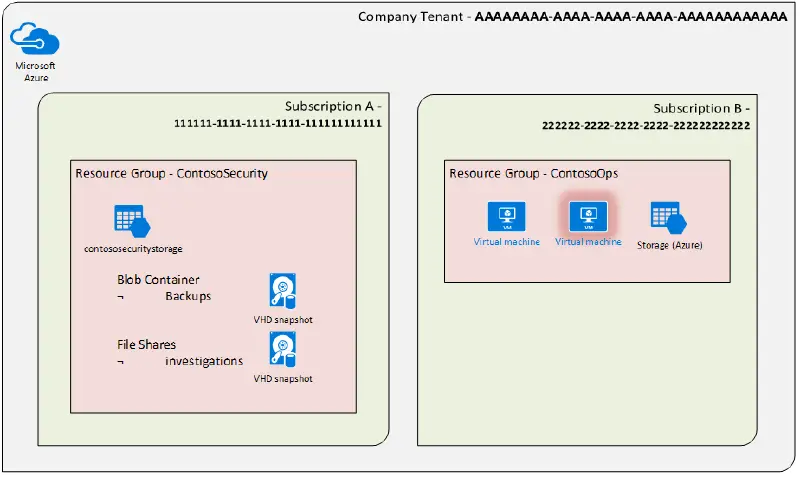
Start-AzureStorageBlobCopy -AbsoluteUri $snapSasUrl.AccessSAS -DestContainer $destSAContainer -DestContext $targetStorageContext -DestBlob $SnapshotName -ForceWe now have a backup copy of the disk for the potentially compromised machine, as well as two file shares that allow access and investigation. The snapshot from the initial resource group has also been removed.
Access the disk-containing share in step two.
We can now access and analyze the VHD of” ContosoWeb” while mounting the file share on the investigation machine. For Windows, Linux, and macOS, we can mount the share. Using the command line, as in the following example, to connect to the share is one of the simplest ways:
Windows#> net use * contososecuritystorage.file.core.windows.netinvestigations /u:contososecuritystorageLinux#> sudo mount -t cifs contososecuritystorage.file.core.windows.netinvestigations -o username=contososecuritystorageThis is the key to the storage location of the share, in this case” contososecuritystorage,” when asked for a password. This can be obtained either programmatically or by copying either the primary or secondary key after right-clicking the Azure Storage Explorer storage account.
the outcome
We have located a VM that may be infected, captured it on camera, and then saved it as an individual file share. Now that we have access to this snapshot over the network, we can use the Tools VM we built in the previous post to conduct investigations. We’ll look at how to automate some aspects of the investigation process in the following blog post in this series.
Blog post that is related: