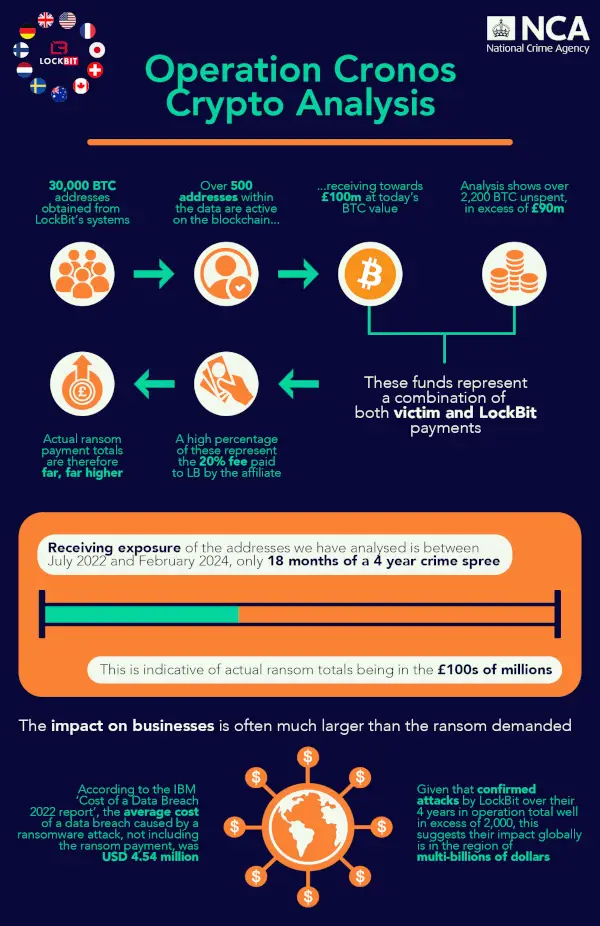
Analysis of hundreds of cryptocurrency wallets connected to the operation revealed that the LockBit ransomware gang had received more than$ 125 million in payments over the previous 18 months.
The National Crime Agency (NCA ) in the United Kingdom identified more than 500 active cryptocurrency addresses as a result of the andnbsp, LockBit takedown, and Operation Cronos.
Money from LockBit
Law enforcement obtained 30, 000 Bitcoin addresses, which were used to manage the group’s ransom payment profits, after hacking the infrastructure of LockBit.
Between July 2022 and February 2024, more than 500 of these addresses received over$ 125 million ( at the current Bitcoin value ).
When LockBit was disrupted, the investigation discovered that more than 2, 200 BTC—more than$ 110 million at the current exchange rate—remained unspent.
These funds “represent a combination of victim and LockBit payments,” according to an NCA press release from today. A sizeable portion of this money represents the affiliates ‘ 20 % fee to the developers of ransomware.
According to the NCA, this means that the total ransoms victims paid to prevent a data leak are “far, far higher.”
Even if the victim paid the ransom, the threat actor did not always delete all of the stolen data, as the  agency highlighted.
According to the law enforcement organization, the amounts found during the investigation suggest that hundreds of millions of dollars have actually been paid in ransom.
It’s important to note that the impressive sums only cover the cybercriminal activity at LockBit over a period of 18 months.
According to the UK’s National Crime Agency,” Given that confirmed attacks by LockBit over their four years of operation total well over 2, 000, this suggests that their impact globally is in the multi-billions of dollars.”
NCA is the source.
The American Cyber Defense Agency ( CISA ) claimed that LockBit was behind 1,700 ransomware attacks and nbsp in the U.S. since 2020, and the gang extorted$ 91 million from victims.
Additionally, the NCA claimed that by taking control of LockBit’s infrastructure, 85 cryptocurrency exchange accounts with hundreds of thousands of USD worth of crypto assets were found. These accounts are currently restricted by Binance.
In the game for almost four years
As ABCD, LockBit was founded in September 2019 with a focus on high-profile companies like Accenture, Boeing, the UK Royal Mail, Continental, and Bangkok Airways.
With the majority of attacks of this kind occurring in 2023, it rose to the top of the list of active ransomware groups. Over the years, LockBit 2. 0 and a , 4.0 and 3. 0, respectively, switched to new malware that encrypted multiple files.
The LockBit group, which had close to 200 affiliates and was the oldest on the ransomware scene at the time of its disruption, was also one of the biggest.
In order to control the infrastructure of the threat actor, coordinate the disruption, gather data from the servers, arrest people, and impose sanctions, law enforcement from 10 countries worked together.
The group’s leaders and the majority of its affiliates are still unknown, despite the fact that law enforcement is in charge of the hackers ‘  infrastructure.
Anyone who can provide details about the members of the LockBit ransomware gang and their partners will receive rewards worth up to$ 15 million from the U.S. State Department.











