PetSmart, a pet-retail company, is advising some customers that their passwords have been reset as a result of an ongoing credential-loading attack attempting to access accounts.
With over , 60 million customers, and 1,600 stores spread across the US, PetSmart is the largest retailer specializing in pets and related products.
Customers are being targeted by credential-loading attacks, according to new email notifications sent to PetSmart customers , which DarkWebInformer first discovered.
Because they could n’t tell whether the logged-in user was the account owner or the hackers, PetSmart secured passwords for any accounts that had been logged into during the credential-stamping attacks.
The PetSmart email alert states,” We want to assure you that no indications exist that petsmart.com or any of our systems have been compromised.”
Your account was logged into during this time, according to our security tools, which saw an increase in password guessing attacks on petsmart.com. We wanted to know, even though the log-in may have been valid.
Your password petsmart.com has been inactivated “in an abundance of caution to protect you and your account.” Simply click the “forgot password” link when visiting petsmart.com to reset your password.
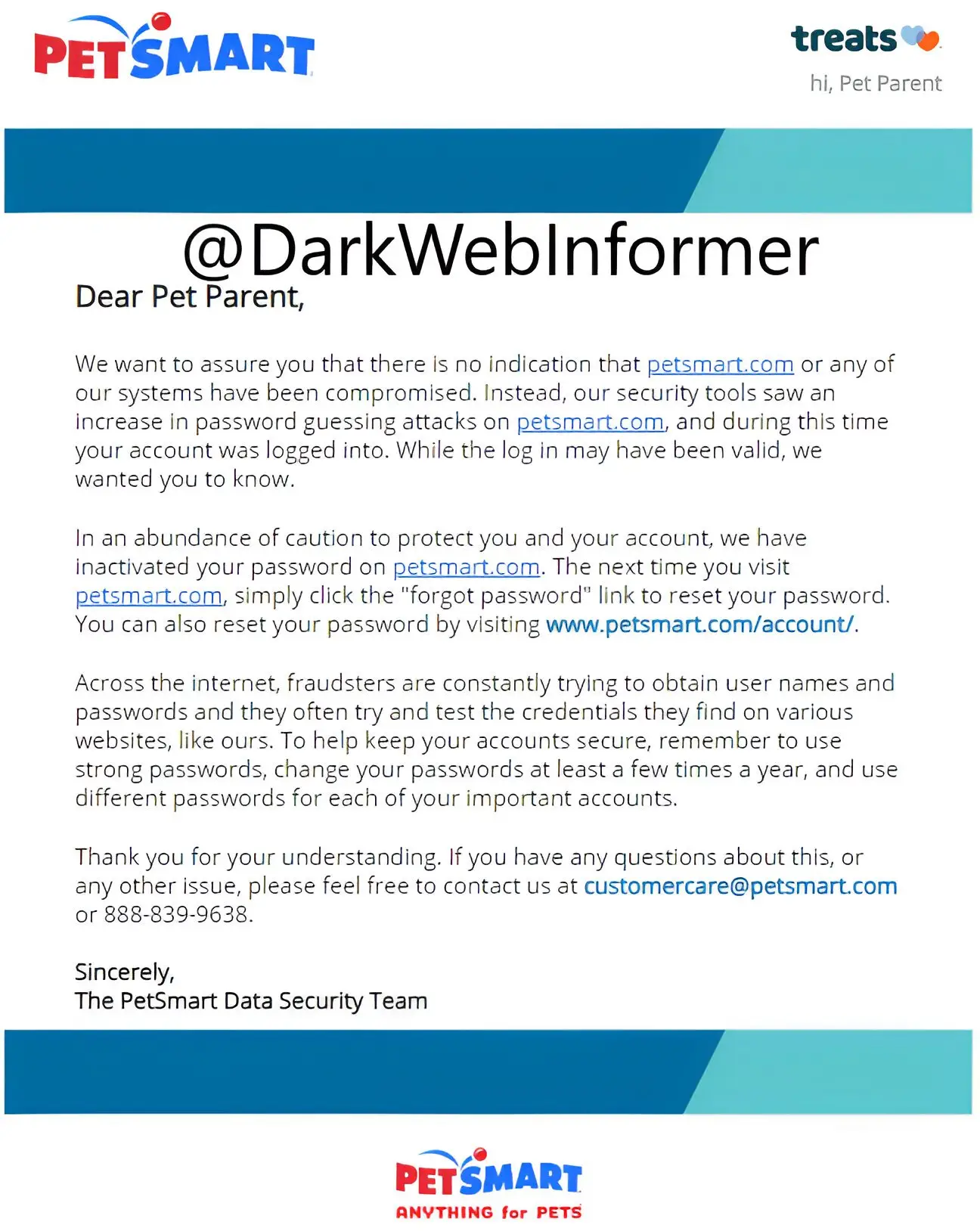
Source: DarkWebInformer
When data breaches lead to credential-stamping attacks, threat actors use the login information they have been given to attempt to access other websites.
Once a threat successfully infiltrates an account, it is used for defraudulent purchases, spam-sending, or other types of attacks.
The threat actors typically sell the compromised accounts to others so they can use them to purchase goods, redeem rewards, or steal money.
Other businesses that have suffered credential-stamping losses include  , PayPal,  , Spotify,  , Xfinity, and Chick-fil-A, as well as  , FanDuel, and  , DraftKings, which have also experienced more damaging losses.
An 18-year-old man was charged with selling 60, 000 DraftKings betting accounts on the stolen account marketplace called the Goat Shop in May 2023.
The Department of Justice later discovered that$ 600,000 had been taken from 1,600 compromised accounts, despite initial estimates that only$ 300,000 had been taken as a result of the attacks.











