Midjourney
Ransomware gangs known as” Black Basta” and” Bl00dy” are now launching widespread attacks against ScreenConnect servers that have been patched using a maximum-severity authentication bypass vulnerability.
This critical flaw ( CVE- 2024- 1709 ) enables hackers to take over any vulnerable instance, create admin accounts on Internet-exposed servers, and remove all other users.
CVE- 2024- 1709 has been in use since last Tuesday, one day after ConnectWise released security updates and proof-of-concept vulnerabilities from a number of cybersecurity firms.
A high-stakes path traversal vulnerability ( CVE- 2024- 1708 ) was fixed by ConnectWise last week, which is only accessible to threat actors with high privileges.
Given that these two security flaws affect all ScreenConnect versions, the company removed them last week so that customers with expired licenses can protect their servers from recurring attacks.
CISA added CVE- 2024- 1709 to its Known Exploited Vulnerabilities Catalog on Thursday, mandating that all federal agencies in the United States secure their servers by February 29.
Shodan currently tracks over 10,000 ScreenConnect servers ( only 1, 559 of which are running the ScreenConnect 23.9.8 patched version ) while Shadowserver claims that CVE- 2024- 1709 is now frequently used in attacks.
Trend Micro discovered that the Black Basta and Bl00dy ransomware gangs have also started utilizing the ScreenConnect vulnerabilities for initial access and by using web shells to access the victims ‘ networks while analysing these ongoing attacks.
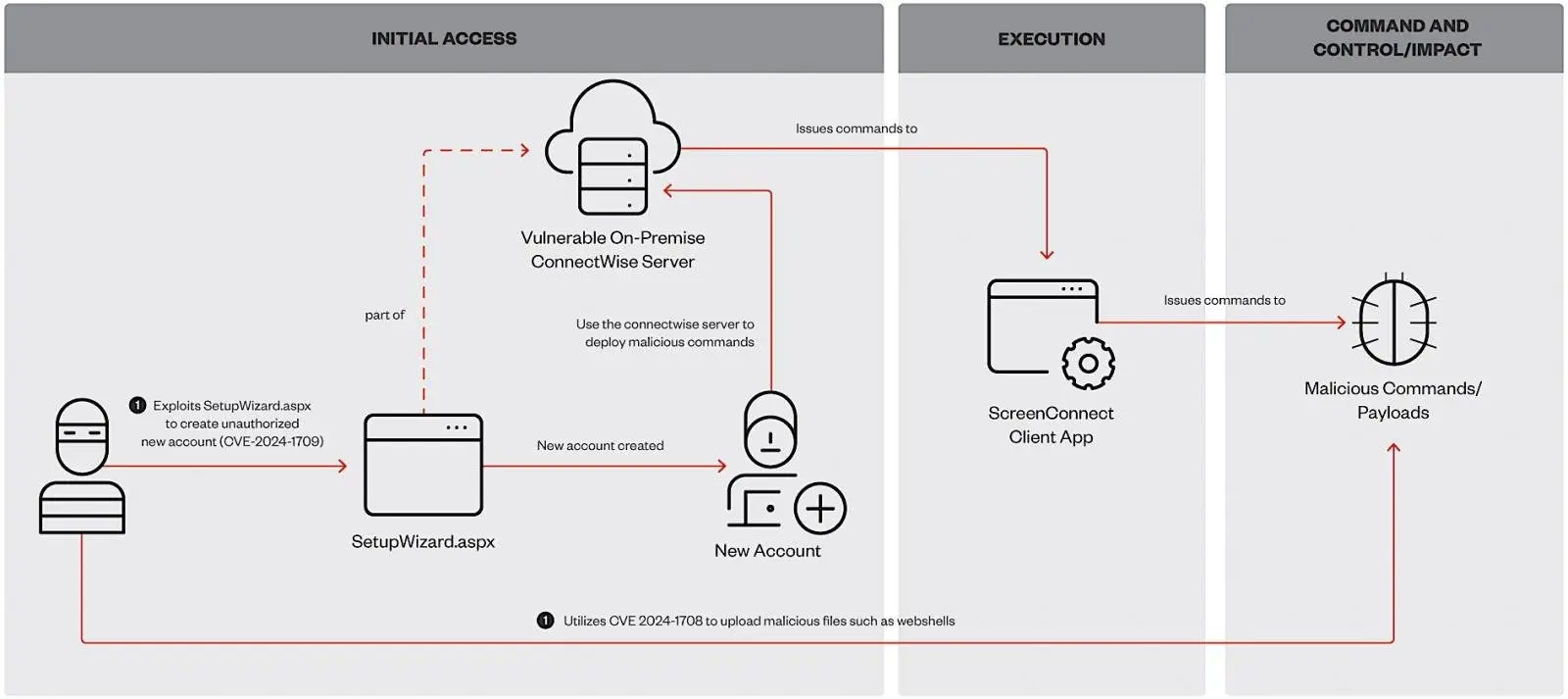
After the attackers gained access to the network and the use of Black Basta-linked Cobalt Strike beacons on compromised systems, Trend Micro observed reconnaissance, discovery, and privilege escalation activity as they conducted their investigations.
Payloads created by the Bl00dy ransomware gang were created using Conti and LockBit Black leaks. However, the attackers were identified by their dropped ransom notes as being involved in the Bl00dy cybercrime operation.
Additionally, according to Trend Micro, attackers used the multi-purpose XWorm malware with RAT and ransomware capabilities.
Other threat actors deployed a number of remote management tools, including Atera and Syncro, or a second ConnectWise instance, using newly gained access to compromised ScreenConnect servers.
The recently patched ScreenConnect flaws are exploited in ransomware attacks, Sophos first reported in a report on Thursday.
A buhtiRansom payload found on 30 different networks and a second LockBit variant created using the leaked Lockbit builder were just two examples of ransomware payloads discovered online in late September 2022.
Ransomware attackers who used the CVE- 2024- 1709 auth bypass to breach the victims ‘ networks also targeted a local government, including systems likely linked to their 911 Systems, according to Huntress, a cybersecurity firm that confirmed their findings last week.
We emphasize the need to update to the most recent version of the software in response to our thorough analysis of the various threat actors who are exploiting vulnerabilities in ConnectWise ScreenConnect, according to Trend Micro today.
” To protect your systems from these identified threats, immediate patching is not only recommended, it is a critical security requirement.”











