A covert cyber espionage campaign intended to expose a previously undocumented backdoor called Zardoor has targeted an unnamed Islamic non-profit organization in Saudi Arabia.
The campaign has likely continued since at least March 2021, according to Cisco Talos, which made the discovery in May 2023. It has only so far identified one compromised target, though it is possible that there are other victims.
Security researchers Jungsoo An, Wayne Lee, and Vanja Svajcer criticized the threat actor’s capacity to maintain long-term access to victim environments without drawing attention to themselves, saying that the adversary used living-off-the-land binaries ( LoLBins ) to deploy backdoors, establish command-and-control ( C2 ) and maintain persistence throughout the campaign.
Data were periodically filtered twice a month as part of the intrusion that was intended for the Islamic charitable organization. It is currently unknown exactly what initial access vector was used to infiltrate the entity.
However, the gained foothold was used to drop Zardoor for persistence and then use open-source reverse proxy tools like Fast Reverse Proxy ( FRP ), sSocks, and Venom to establish C2 connections.
The threat actor used Windows Management Instrumentation ( WMI ) to move laterally and spread the attacker’s tools, including Zardoor, by spawning processes on the target system and carrying out C2 commands, according to the researchers.
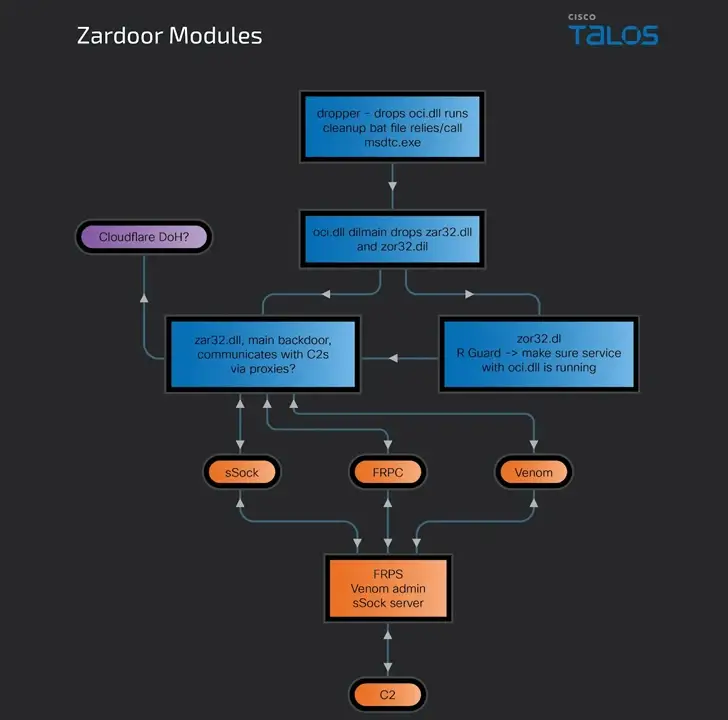
A dropper component that deploys a malicious dynamic-link library ( “oci) is made possible by the as-yet-undetermined infection pathway. dll” ), “zar32,” is in charge of delivering two backdoor modules. dll” and “zor32” dll.
The latter ensures that “zar32,” whereas the former is the essential backdoor component that facilitates C2 communications. Administrator privileges have been granted for the deployment of dll. Data can be accessed by Zardoor, along with shellcode and executables that are remotely retrieved, C2 IP address updates, and host deletion.
The campaign’s motivations are unknown, and it does not at this time have any tactical similarities to a well-known, widely publicized threat actor. However, it is determined to be an “advanced threat actor’s” work.











![A computer screen displaying red text on a black background shows various lines of code, including commands for transferring files, executing scripts, and listing network connections; some sensitive information is redacted with "[Redacted]". This high-level security setup underscores the importance of a robust VPN to mitigate any potential cyberthreat.](https://dodcybersecurityblogs.com/wp-content/uploads/2024/02/malware-4.webp)