As part of a malicious campaign that uses a malware-loader called IDAT Loader to distribute a commercial remote access trojan known as Remcos RAT, Ukrainian entities based in Finland have been targeted.
The Computer Emergency Response Team of Ukraine ( CERT-UA) has identified an attacker responsible for the attack under the moniker UAC- 0184.
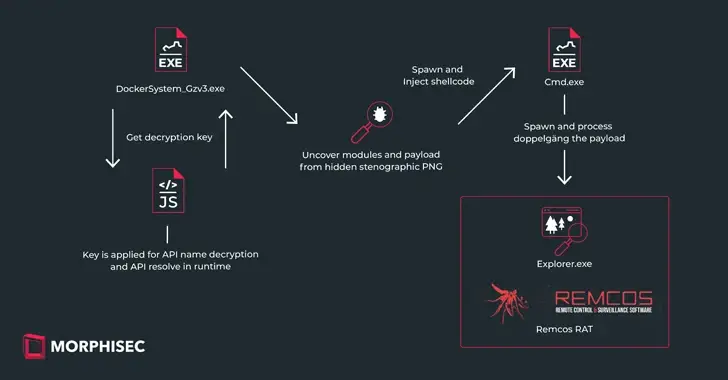
In a report shared with The Hacker News, Morphisec researcher Michael Dereviashkin claimed that the attack, as part of the IDAT Loader, employed steganography as a method. Stego or steganographic techniques are well-known, but it is crucial to understand how to defend against them because they play a significant role in defense evasion.
In recent months, IDAT Loader, which overlaps with another loader family called Hijack Loader, has been used to deliver additional payloads like RedLine Stealer, SystemBC, and DanaBot. A threat actor identified as TA544 also distributed Remcos RAT and SystemBC through phishing attacks.
The phishing campaign, which was first exposed by CERT-UA in early January 2024, involves using war-themed lures as a pretext to launch an infection that results in the deployment of IDAT Loader, which then locates and extracts Remcos RAT using an embedded steganographicPNG.
The development comes as CERT-UA revealed that defense forces in the nation have been targeted by the Signal instant messaging app to distribute a booby-trapped Microsoft Excel document that runs COOKBOX, a Power Shell-based malware capable of loading and running cmdlets. A cluster dubbed UAC- 0149 has been given the credit for the activity by CERT-UA.
It also follows the resurgence of PikaBot malware propagation since February 8, 2024, with the release of an updated variant that appears to be in active development.
Elastic Security Labs described the PikaBot loader as using a new method for unpacking and extensive obfuscation. ” The core module has made changes to the obfuscation functionality, a new string decryption implementation, and a number of other modifications.”