TA866 deploys WasabiSeed and, Screenshotter Malware, according to an invoice Phishing Alert
After a nine-month hiatus, the threat actor known as TA866 has resurfaced, this time delivering well-known malware families like WasabiSeed and Screenshotter.
Thousands of invoice-themed emails bearing fake PDF files were sent to North America as part of the campaign, which was observed earlier this month and blocked by Proofpoint on January 11, 2024.
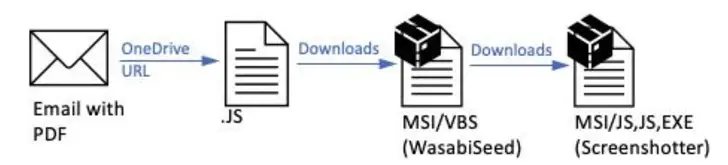
According to the enterprise security company,” The PDFs contained OneDrive URLs that, if clicked, started a multi-step infection chain eventually leading to malware payload, an adaptation of the WasabiSeed and Screenshotter custom toolset.”
The company first reported TA866 in February 2023, attributing it to the Screentime campaign that distributed WasabiSeed, a Visual Basic script dropper used to download Screenshotter and extract screenshots of the victim’s desktop periodically to an actor-controlled domain.
Due to Screenshotter’s role as a reconnaissance tool to identify high-value targets for post-exploitation and deploy an AutoHotKey ( AHK)-based bot to ultimately drop the Rhadamanthys information stealer, there is evidence to suggest that the organized actor may be financially motivated.
Screentime and another intrusion set known as Asylum Ambuscade, a crimeware organization active since at least 2020 that also engages in cyber espionage operations, were found to overlap in later research from the Slovak cybersecurity firm ESET in June 2023.
With the exception of the transition from macro-enabled Publisher attachments to PDFs bearing a rogue OneDrive link, the most recent attack chain is essentially unchanged. The campaign relies on the spam service offered by TA571 to distribute the booby-trapped PDF files.
According to Proofpoint researcher Axel F, “TA571 is a spam distributor, and this actor sends high volume spam email campaigns to deliver and install various malware for their cybercriminal customers.”
This includes DarkGate, the last of which enables attackers to carry out a variety of commands, including information theft, cryptocurrency mining, and the execution of arbitrary programs. It also includes AsyncRAT, NetSupport Rat, IcedID, PikaBot, QakBot ( also known as Qbot ).
In an analysis of the malware this week, South Korean cybersecurity company S2W stated that” Darkgate first appeared in 2017 and is sold only to a small number of attack groups in the form of Malware-as-A-Service through underground forums.”
DarkGate” continues to update it by adding features and fixing bugs based on analysis results from security researchers and vendors,” highlighting adversaries ‘ ongoing efforts to use anti-analysis techniques to avoid detection.
Cofense revealed that shipping-related phishing emails primarily target the manufacturing sector to spread malware like Agent Tesla and Formbook, which is why TA866 has resurfaced.
According to Cofense security researcher Nathaniel Raymond,” Shipping-themed emails increase during the holiday seasons, albeit only slightly.”
The yearly trends” suggest that these emails follow a particular trend throughout the year with varying degrees of volumes, with the most significant volumes being in June, October, and November,” according to the statistics.
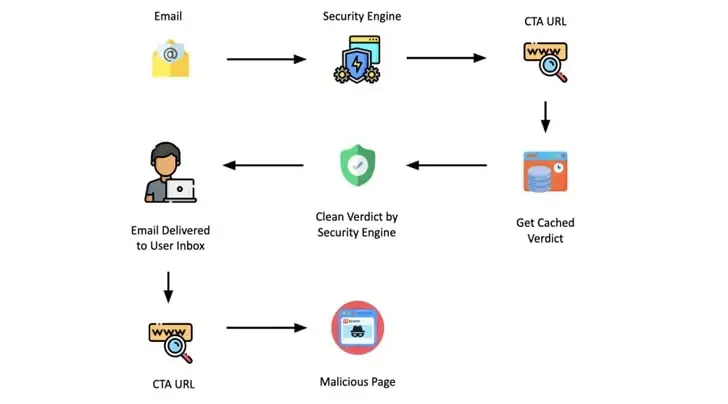
The change also comes after the identification of a novel evasion strategy that uses security products ‘ caching mechanisms to circumvent them by incorporating an appropriate Call To Action ( CTA ) URL in the phishing message sent to the intended recipient.
According to Trellix, such attacks have disproportionately targeted financial services, manufacturing, retail, and insurance verticals in Italy, the U.S., France, Australia ,and India. Their strategy involves caching a seemingly benign version of the attack vector and then altering it to deliver an evil payload.
Such a URL is scanned by the security engine, which then flags it as safe and stores the result in its cache. This also implies that the cached result is served if the URL is encountered again during that time frame.
Trellix emphasized that attackers are utilizing this flaw by waiting for security vendors to process the CTA URL and cache their decision before changing the link to point to the intended phishing page.
Security experts Sushant Kumar Arya, Daksh Kapur, and Rohan Shah claimed that because the verdict was favorable, the email simply landed in the victim’s inbox. The recipient would be taken to the malicious page if they chose to open the email and click the link or button in the CTAURL.
See Related Blogs
Meet the Airmen Who Assist Families of the Fallen During Respected Transfers
Important Reminders from the Most Recent Phishing Attacks(Opens in a new browser tab)Insights into the State of Cyber ThreatsIT Users Are Targeted by a Tax-themed Phishing Scam Using TerrorStealer Malware Spreading.(Opens in a new browser tab
FISSEA Summer Forum: August 23, 2023
Math-heavy research papers will be easier to view online thanks to the NIST tool.
About DoD Cybersecurity Forescout Sheds New Light on Denmark’s Energy Sector CyberattacksHackers squander a 14-year-old CMS editor to create SEO poisoning on government and academic websites.(Opens in a new browser tab)
After being shut down by law enforcement, the LockBit ransomware group resurfaces
Banking Trojans Target Latin America and Europe Through Google Cloud Run