How are the targets chosen by ransomware groups? It’s a rhetorical question because they typically do n’t. The access to corporate IT environments is made possible by a sophisticated cybercrime supply chain, which is used by ransomware as-a-service ( RaaS ) platforms and affiliate ecosystems.
In many cases, affiliates and ransomware groups buy targets rather than” chosen” them.
Opportunistic criminals known as ransomware attackers take advantage of easily accessible targets by frequently using other cybercriminals ‘ initial access points rather than making their own.
The cybercrime ecosystem has significantly expanded in size, sophistication, and complexity in recent years. There are now numerous independent supply chains working together with intricate interdependencies, much like in our modern economy.
This article will examine various components of the supply chain for cybercrime and explain how they interact to produce the two-year-old explosion in online crime.
Infostealer malware: on the rise
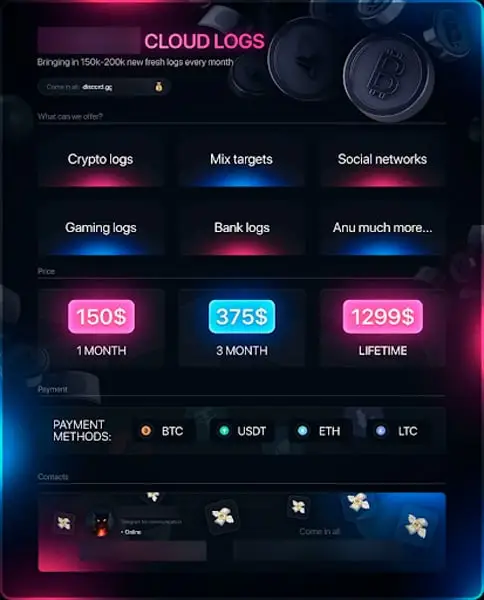
Ransomware attacks frequently start with” stealer logs,” which are leftovers from malware infections that infect information thieves. Infostealers, a type of malware that steals all sensitive data from one host, exports it to C2 infrastructure, and then self-terminates on the machine, have grown dramatically over the past three years.
Infostealer malware variants are produced and sold by specialized malware vendors on Telegram channels, typically with a monthly or lifetime license.
The malware is then spread by other threat actors via malware distribution, malware deception, and phishing emails before being monetized from the resulting stealer logs.
A single compressed file called a” snareer log” contains all of the data for one user that was previously mentioned.
Threat actors primarily use illicit Telegram channels to monetize their logs. Free channels act as” samples” to demonstrate the actor’s high-value and distinctive logs. These are paid channel advertisements that have a small user base and frequently have higher-value logs.
Over 46 million stealer logs, each containing up to hundreds of user credentials per infected device, have been found and consumed by Flare so far.
Approximately 400,000 new infections are currently reported each week, and we estimate that 5 % of them have corporate credentials.
The presence of session cookies in the stealer log makes infostealers particularly dangerous. In session replay attacks, where the actor can get around multi-factor authentication, active session cookies can be used.
Infostealers are a very easy and straightforward way to gain access to corporate IT systems and infrastructure at first and establish persistence.
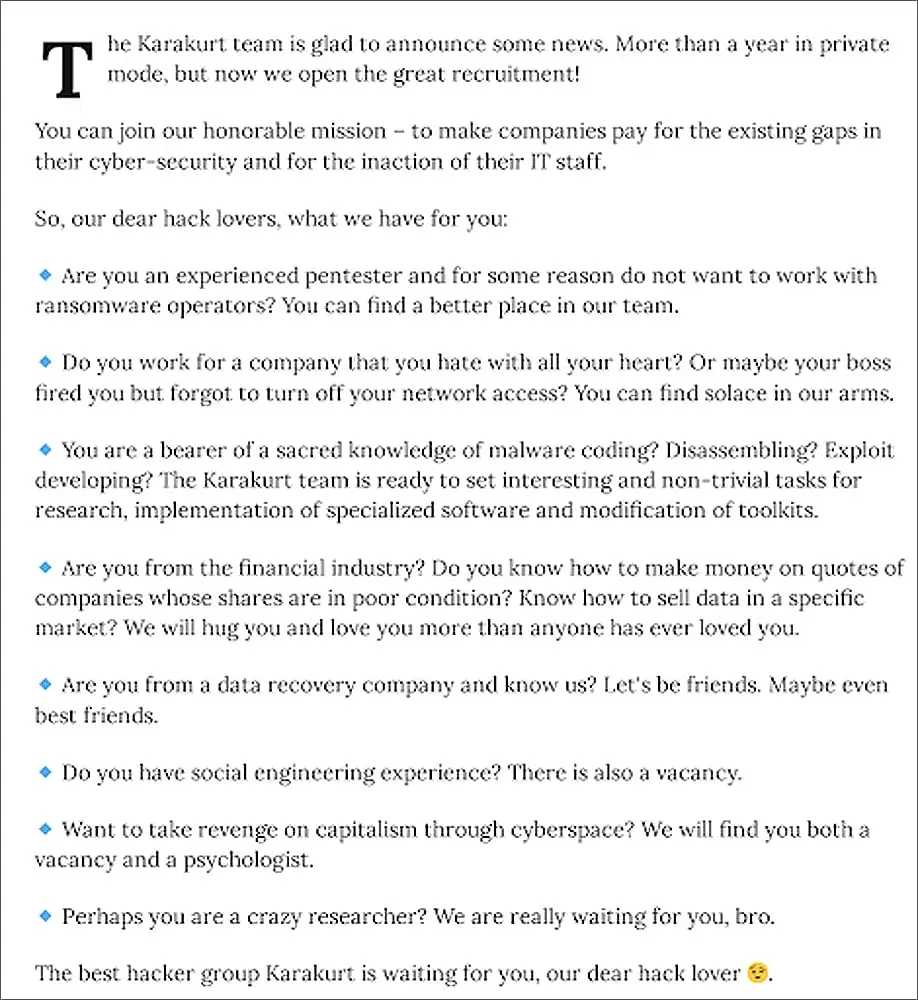
Many ransomware organizations and affiliates, while we suspect they use infostealers to gain access, prefer the” white glove” service provided by initial access brokers.
Ecosystem for Initial Access Brokers
Threat actors with a high level of specialization known as initial access brokers concentrate on carrying out an attack’s initial stages, gaining access to the corporate IT environment, and building persistence.
Then, in an auction-style format, this access is either privately sold via direct messages in pre-existing relationships or sold to other actors on three significant dark web forums: Exploit, XSS, and RAMP.
For affiliates and ransomware groups, initial access brokers are a significant source of supply. By establishing the privileged IT access and then auctioning it off, they remove a significant barrier to entry, especially for affiliates of low-level ransomware.
According to Flare’s initial research, initial access brokers compromised critical infrastructure sells for a premium and more than 500 companies in 2023, disproportionately target organizations in NATO nations.
Direct evidence of initial access brokers buying” stealer logs in bulk” has been found in Flare. The high-value credentials, such as corporate emails, SSO portals, and development environments, can then be found by sorting through these logs.
Exploiting Access: Affiliates and ransomware groups
The sophistication and complexity of the ransomware market are only increasing. Today, there are reportedly more than 50 ransomware organizations operating, many of which sell affiliate work.
In exchange for a cut of the profits, ransomware affiliates use the software and name recognition offered by the larger group.
The ecosystem depends heavily on affiliates. A ransomware group can concentrate on creating increasingly sophisticated ransomeware code and perfecting extortion techniques with the help of competent affiliates.
As a result of this role specialization, the criminal organization becomes more effective, which increases attacks, payouts, and incentives.
Since successful ransoms of well-known companies can fetch hundreds of thousands of dollars in a matter of days, e-commerce groups that have established themselves frequently compete with top affiliates.
The most recent episode of the Russian dark web forum XSS, in which LockBit claimed that CL0P’s leader had set him up to be detained by the FSB and even poisoned by polonium, made this competition abundantly clear.
Given the complexity of the cybercrime ecosystem, what we have described here is merely a very succinct and high-level overview of its significant and expanding economy, which includes clear net sites, TOR forums, Telegram, and other social media platforms.
In the modern environment, it is essential to create a strong corporate continuous threat exposure management ( CTEM) program that can disrupt every component of the cybercrime supply chain.
Remediate Stealer Logs with Flare, Detect &
Organizations can proactively identify, prioritize, and reduce the kinds of exposures that threat actors frequently take advantage of thanks to the Flare Continuous Threat Exposure Management ( TEM) solution.
To identify unidentified events, prioritize risks, and provide actionable intelligence you can use right away to enhance security, our platform automatically scans the dark web, free and illegal Telegram channels around the clock.
Flare quickly replaces a number of SaaS and open source tools and integrates into your security program.  ,
Join our free trial to find out more.
Flare served as the writer and sponsor.