In an effort to deploy encryptors based on the leaked LockBit ransomware builder, rogue actors are once more using TeamViewer to gain initial access to organization endpoints.
TeamViewer is a reliable remote access tool that is valued for its ease of use and capabilities and is widely used in the business world.
Unfortunately, scammers and even ransomware actors love the tool because they can use it to access remote desktops, drop malicious files, and run malicious programs without restriction.
When numerous victims confirmed in the BleepingComputer forums that their devices had been breached using TeamViewer to encrypt files with the Surprise ransomware, a similar case was first reported in March 2016.
At the time, TeamViewer’s justification for the unauthorized access was credential stuffing, which meant that the attackers used users ‘ leaked credentials rather than taking advantage of a zero-day vulnerability in the software.
The software vendor at the time stated that because TeamViewer is a widely used program, many online criminals try to log in using the information from compromised accounts to see if there are any corresponding TeamsViewers with the same credentials.
If so, it’s likely that they have access to every device that has been given permission to install malware or ransomware.
TeamViewer once more targeted
According to a recent Huntress report, cybercriminals continue to use TeamViewer to try to install ransomware on devices, demonstrating that they have n’t given up on these tried-and-true methods.
The log files that were examined ( connections_incoming ). txt ) displayed connections from the same source in both instances, pointing to a shared attacker.
Huntress observed multiple employee accesses in the logs for the first compromised endpoint, indicating that the staff was actively using the software for legitimate administrative tasks.
Huntress ‘ second endpoint, which has been operational since 2018, showed no activity in the logs for the previous three months, suggesting that it was being watched less frequently, possibly making it more alluring to attackers.
The attackers used a DOS batch file ( PP ) to deploy the ransomware payload in both instances. bat ) was installed on the desktop, and a rundll32 was used to execute dll files ( payload ). exe command.
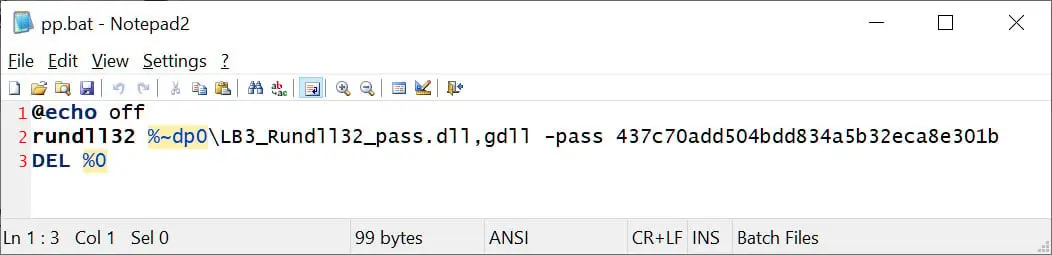
Source: BleepingComputer
Although successful, the attack on the first endpoint was contained. The antivirus software stopped the effort on the second, forcing numerous unsuccessful payload execution attempts.
Huntress notes that the attacks are comparable to LockBit encryptors made using a leaked LockBeit Black builder, even though she has n’t been able to definitively link any known ransomware gangs to them.
The LockBit 3.0 ransomware builder was leaked in 2022, and the Bl00dy and Buhti gangs quickly started using it to launch their own campaigns.
With the help of the leaked builder, you can make various encryptor versions, including executables and DLLs that need passwords to properly launch.
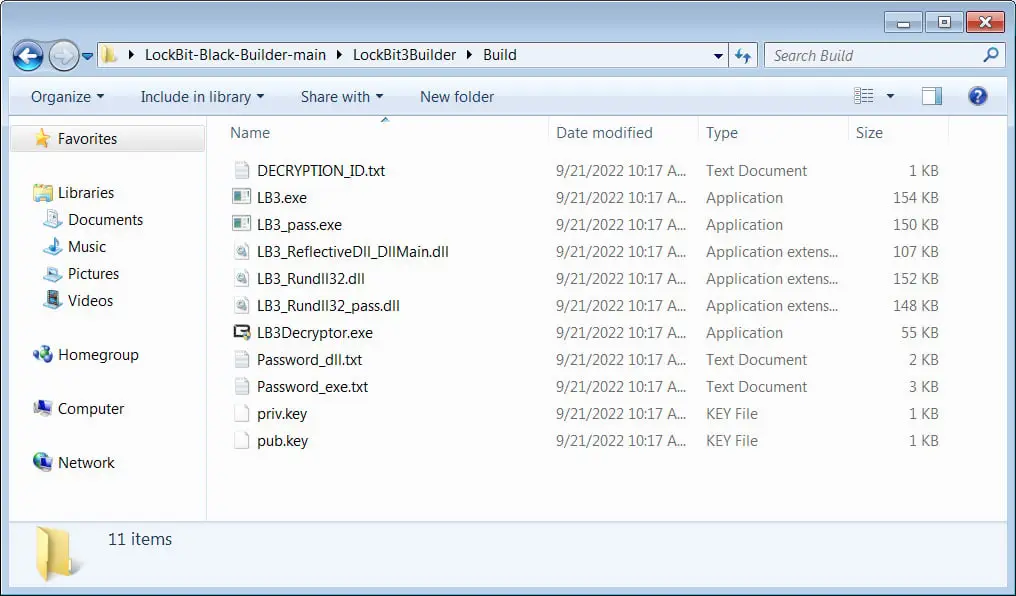
Source: BleepingComputer
The attacks through TeamViewer appear to be using the password-protected LockBit 3 DLL, according to the IOCs provided by Huntress.
While BleepingComputer was unable to locate the specific sample that Huntress had seen, we did discover a different sample last week that was uploaded to VirusTotal.
Although the standard LockBit 3.0 ransomware note is not used in this sample, it is clear that it was made by a different ransomeware gang using the leaked builder.
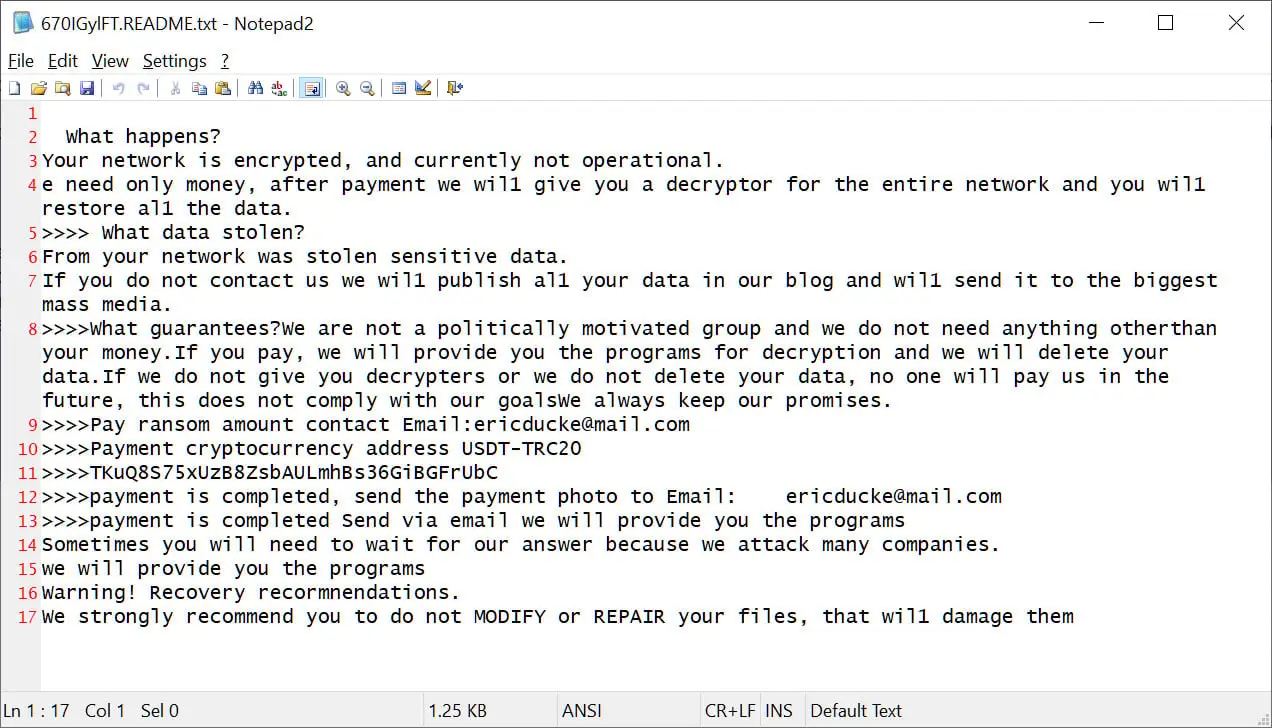
Source: BleepingComputer
The company provided the following statement to BleepingComputer regarding the attacks and installation security, though it is unclear how the threat actors are currently gaining control of TeamViewer instances.
” At TeamViewer, we take the security and integrity of our platform very seriously, and we categorically reject any malicious software use.”
According to our analysis, TeamViewer’s default security settings are typically compromised in cases of unauthorized access. This frequently involves using passwords that are simple to guess, which can only be done by using an out-of-date version of our product. We consistently stress the significance of upholding strict security procedures, such as the use of complex passwords, two-factor authentication, allow lists, and routine updates to the most recent software versions. In order to prevent unauthorized access, these actions are essential.
We have published a set of best practices for secure unattended access, which can be found at TeamViewer Support, under the title” Best practices, secure access.” This is done to further assist our users in maintaining secure operations. To improve their security posture, we strongly advise all of our users to abide by these recommendations.