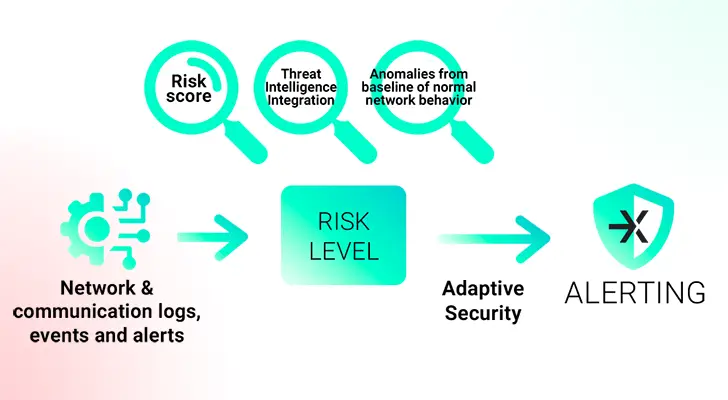
How to Get the Best Risk-Based Alerting Bye, Bye SIEM
Did you know that the best technology for identifying cyber threats is Network Detection and Response ( NDR)? NDR provides adaptive cybersecurity with fewer false alerts and effective threat response, as opposed to SIEM.
Do you know how Network Detection and Response ( NDR) has evolved into the most potent tool for spotting online threats?
Through risk-based alerting, which prioritizes alerts based on the potential risk to your organization’s systems and data, NDR significantly improves your security. How? Real-time analysis, machine learning, and threat intelligence from NDR, however, offer immediate detection, lowering alert fatigue and enabling better decision-making. NDR provides adaptive cybersecurity with fewer false positives and effective threat response, as opposed to SIEM.
Why Do People Use Risk-Based Alerting?
According to the level of risk they pose to an organization’s systems, data, and overall security posture, risk-based alerting prioritizes security alerts and responses. Organizations can focus their resources on dealing with the most serious threats first thanks to this strategy.
Effective resource allocation is one of the advantages of risk-based alerting, among others:
- Organizations can allocate resources more effectively and save time by prioritizing alerts based on risk.
- Lower-risk alerts can be managed more methodically and with fewer resources, while high-risis alarms need to be dealt with right away.
- When dealing with numerous alerts, many of which may be false positives or minor issues, security teams frequently experience alert fatigue. Risk-based alerting enables teams to concentrate on alerts with the greatest potential impact, helping to reduce alert fatigue. The impact of security incidents can be greatly reduced or prevented by doing this.
- Better decision-making is made by prioritizing alerts based on risk. Security teams can choose which alerts to look into first and how to allocate resources in accordance with the organization’s potential impact.
- Additionally, it encourages the use of threat intelligence in decision-making. Organizations can evaluate the seriousness of alerts more effectively by taking into account the context of threats and comprehending their potential effects.
Establishing Your Risk-Based Cybersecurity Strategy in Three Steps
1. NDR’s Function in Risk-Based Alerts
The implementation of risk-based alerts within an organization’s cybersecurity strategy is greatly facilitated or enabled by Network Detection and Response ( NDR).
NDR solutions analyze network traffic patterns and behavior to find anomalies that point to potential security risks. They are made to identify threats on your network, respond to them, and offer insights into the potential risks of various activities or incidents.
They can determine various alert levels based on the weighting of the evidence using this contextual information about network activity, various network analyzer weights, and an accumulation of various alarms up to the alarm threshold. Asset management can also define particular critical zones. In order to align with the risk-based approach, this context is essential for assessing the severity and potential impact of security alerts.
2. Increasing Risk Assessment Through Threat Intelligence Feeds
NDR solutions enrich the data used to analyze and categorize network activity because they are integrated with threat intelligence feeds. OSINT, Zeek, or MITRE ATT&, CK information may improve criticism. The ability to evaluate the risk connected to particular alerts is improved by this integration.
Organizations can quickly respond to high-risk alerts thanks to some NDR systems ‘ automated response capabilities. This complies with risk-based alerting’s objective of addressing serious threats right away:
- Based on a variety of factors, such as the seriousness of the activity, the setting in which it took place, impacted assets or systems, and historical data, detected events or alerts are given risk scores. The goal is to evaluate the detected event’s potential harm or impact.
- Different factors that affect risk assessment are weighted differently in the risk booster. Activities involving valuables or privileged accounts, for instance, might be given a higher risk score. Additionally, events that significantly deviate from predetermined norms or patterns might be given a heavier weight.
- In order to find hidden attacks hidden in the background of regular network activities, correlated alerts are essential. By reducing the number of specific alerts analysts must deal with, increased alert correlation significantly reduces the workload.
3. Automating High-Risk Alert Responses
Given the significant daily communication volumes within networks that attackers could take advantage of, the strategic use of automation is crucial for bolstering network defenses against potential attacks.
Insider threats, compromised accounts, or suspicious user behavior can be more easily identified and used for risk assessment because user and entity behavior analysis is already built into the NDR to analyze the behavior of users and entities ( e .g., devices ) within the network.
Risk scores can be changed as new data becomes available or the security landscape changes because they are dynamic and change over time. The risk score is modified if an initially low-risk event develops into a higher risk event.
Utilizing NDR with machine learning to improve cybersecurity and dynamic risk assessment
Large amounts of data can be sorted through by machine learning algorithms to find common patterns or baselines for network behavior. In order to spot deviations that might indicate suspicious or malicious activity, these baselines serve as a benchmark. Security teams can focus their efforts on investigating and reducing high-risk alerts thanks to the automation, which improves overall efficiency. The security system can become more adaptable and capable of dealing with new risks thanks to machine learning algorithms ‘ ability to continuously learn and adapt to new patterns and threats. In the rapidly changing cybersecurity landscape, continuous learning is essential.
Organizations can dynamically assess the risk connected to various network activities by combining NDR capabilities with machine learning. A more accurate and timely risk assessment is made possible by machine learning algorithms ‘ ability to adapt to changing threats and network behavior.
Examples & Use Cases: Increased Detection; Reduced False Alerts
An organization evaluates risk scores for detected events based on their potential impact and contextual information if it uses a network detection and response ( NDR) solution to monitor its network traffic.
1. Attempt at Unauthorized Access:
An important server is attempted to be accessed without authorization by an external IP address. A crucial server that holds private customer data is one of the assets that is at risk.
Anomalous behavior: This server has never been accessed by the IP address before. There is a high risk score. Due to the involvement of a crucial asset and the detection of anomalous behavior, the NDR system assigns the alert to an extremely high risk score, indicating that there may have been an intrusion into security. Quickly escalated for investigation and response is the high-risk alert.
2. Updated software:
An internal device initiates an update from a reliable source in this alert, which is described as an ordinary software update event. A low risk score is caused by the risk factors, which include the affected asset ( a non-critical user workstation ) and the update’s regular behavior from a reliable source.
This alert receives a low-risk score from the NDR system, indicating that it involves an uncritical asset and that the behavior is typical and expected. This low-risk alert can therefore be recorded and monitored, but immediate action is not necessary.
Conclusion: For this reason, SIEM is superior.
For risk-based alerting, NDR is regarded as superior to Security Information and Event Management ( SIEM) because it focuses on real-time analysis of network traffic patterns and behaviors, providing immediate detection of anomalies and potential threats, as opposed to SIEM, which relies solely on log analysis and may experience delays and miss subtle, network-centric threats in addition to producing numerous alerts ( false ones ).
Last but not least, compared to conventional SIEM approaches, NDR uses machine learning and threat intelligence to improve its capacity to adapt to changing risks and reduce false positives.
So, are you prepared to improve your detection skills? Download our new Security Detection whitepaper to learn more about how risk-based alerting can help you save money, save time, and significantly reduce the number of false alerts if you’re still thinking about it.