Up to$ 10 million in cash rewards have been announced by the U. S. Department of State for knowledge of people who hold important positions in the Hive ransomware scheme.
Additionally, it is dispersing an additional$ 5 million in exchange for information that could result in the arrest and/or conviction of anyone” confederating with or attempting to participate in Hive ransomware activity.”
A little more than a year has passed since the Hive ransomware-as-service ( RaaS ) gang’s darknet infrastructure was covertly infiltrated and demolished in order to receive the multi-million dollar rewards. In December 2023, one person who was thought to be connected to the group was detained in Paris.
Hive, which debuted in the middle of 2021, generated about$ 100 million in illegal revenue by targeting more than 1,500 victims across 80 nations. Bitdefender revealed in November 2023 that Hunters International, a brand-new ransomware organization, had purchased Hive’s infrastructure and source code in order to launch its own operations.
According to information gathered by Netenrich security researcher Rakesh Krishnan, the threat actors associated with Hunters International are likely based in Nigeria, specifically an individual by the name of Olowo Kehinde. However, it’s also possible that the actors used a fictitious persona to conceal their true identities.
In its 2023 review, which was released last week, blockchain analytics company Chainalysis estimated that ransomware crews collected$ 1.1 billion in extorted cryptocurrency payments from victims last year, up from$ 567 million in 2022. This estimate almost confirms the trend of a relative decline in run-off during that year.
A significant reversal from the decline seen in 2022, it claimed,” 2023 marks a major comeback for ransomware, with record-breaking payments, and substantial increase in the scope and complexity of attacks.”
The Russo-Ukranian War and the disruption of Hive have been blamed for the decline in ransomware activity in 2022, which has been deemed a statistical aberration. Additionally, 4, 496 victims were reported to data leak sites in 2023, an increase from 3, 048 and 2, 670, respectively.
Manufacturing is the most affected industry vertical in 2023, followed by profession and legal services, high technology, retail, construction, and healthcare sectors, according to Palo Alto Networks Unit 42’s analysis of ransomware gangs ‘ public listings of victims on dark web sites.
According to reports, the takedown “likely affected the broader activities of Hive affiliates, potentially lessening the number of additional attacks they could carry out,” even though the law enforcement action prevented approximately$ 130 million in ransom payments to HiVE. The effort may have prevented payments totaling at least$ 210.4 million.
Last year saw an increase in new entrants and offshoots, which is evidence that the ransomware ecosystem is drawing in a steady stream of new players who are drawn in by the promise of high profits and lower entry barriers. This increases the regularity, scope, and volume of attacks.
The number of active ransomware gangs increased from 35 to 47 between Q1 and Q4 2023, according to cyber insurance provider Corvus, either as a result of fracturing and rebranding or other actors obtaining leaked encryptors. In 2023, 25 new ransomware organizations appeared.
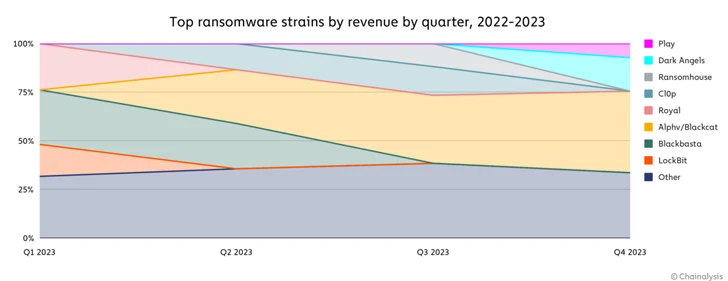
According to Chainalysis, the frequency of rebranding serves as a significant reminder that the ransomware ecosystem is not as large as its many strains would have us believe.
In addition to a notable shift toward big game hunting, which refers to the strategy of targeting very large corporations in order to collect hefty ransoms, cross-chain connections, instant exchanger, and gambling services are steadily facilitating the movement of e-crime groups away from centralized exchanges and mixers in favor of new channels for money laundering.
Sinbad, a virtual currency mixer used by the North Korea-linked Lazarus Group to launder illicit funds, was subject to sanctions from the U.S. Treasury Department in November 2023. Blender, Tornado Cash, and ChipMixer are a few of the other approved mixers.
According to Coveware data, the switch to big game hunting is also a result of businesses ‘ growing reluctance to make concessions, as the number of victims who chose to pay decreased to 29 % in the final quarter of 2023.
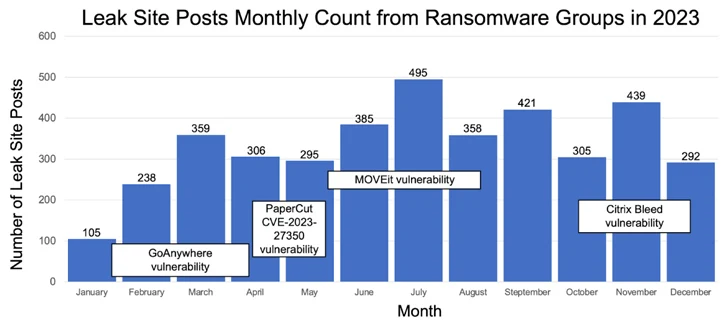
A significant change in threat actors ‘ use of vulnerabilities, according to Corvus, “was another factor contributing to higher ransomware numbers in 2023,” highlighting Cl0p’s exploitation of Fortra GoAnywhere and Progress MOVEit Transfer flaws.
A major vulnerability is like turning on a faucet if malware, like infostealers, consistently drips new ransomware victims. Access to thousands of victims can become relatively simple with some vulnerabilities and appear to happen overnight.
Ransomware groups ‘ weaponization of security vulnerabilities, according to cybersecurity company Recorded Future, can be divided into two distinct categories: vulnerabilities that have only been used by a small number of groups and vulnerabilities used frequently by numerous threat actors.
It stated that” Magniber has a special focus on Microsoft vulnerabilities, with Windows Smart Screen being the focus of half of its special exploits.” ” Cl0p has notoriously and uniquely concentrated on Accellion, SolarWinds, and MOVEit file transfer software.” Veritas and Veeam’s data backup software has been the main focus of ALPHV. Oracle, Atlassian, and Kaseya server software has been the focus of REvil’s special attention.
The increase in DarkGate and PikaBot infections after the QakBot malware network was taken down, which had been the preferred initial entry point into target networks for ransomware deployment, is another indication of the ongoing adaptation seen among cybercrime crews.
A” correlation” between inflows into initial access broker ( IAB) wallets and an increase in ransomware payments, according to Chainalysis, suggests that monitoring IABs blockchain trails may offer early indicators of potential intervention and attack mitigation.
According to Unit 42,” Ransomware organizations like Cl0p have used zero-day exploits against recently discovered critical vulnerabilities, which represent a complex challenge for potential victims.”
The impact of a vulnerability may not be fully captured by ransomware leak site data, despite the fact that it can offer useful insight into the threat landscape. Organizations must create strategies to quickly react to and lessen the effects of zero-day exploits in addition to being vigilant about known vulnerabilities.