The SOC Automation Capability Matrix ( SOC ACM) was developed by John Tuckner and the team at workflow and automation platform Tines to aid security operations teams in better comprehending their automation capabilities and incident-response.
Since its introduction in January 2023, the security community has shared and endorsed this customizable, vendor-agnostic tool with lists of automation opportunities, most notably Airbnb engineer Allyn Stott in his BSides and Black Hat talk, How I Learned to Stop Worrying and Build a Modern Detection &, Response Program.
One user claimed that the SOC ACM could serve as a benchmark for classifying SOAR automations, similar to the MITRE ATT&, CK, and RE&, CT frameworks but with more of an emphasis on automation. Organizations in Fintech, Cloud Security, and other fields have used it as a starting point for evaluating and improving their security automation programs.
Here, we’ll examine the SOC ACM’s operation in more detail and discuss how you can apply it to your company.
The SOC Automation Capability Matrix: What Is It?
Security operations teams can take proactive action in response to frequent cybersecurity incidents thanks to the SOC Automation Capability Matrix’s interactive set of techniques.
It’s not a list of specific applications for any one good or service; rather, it serves as an outline for potential organizational capabilities.
For beginners, it provides a strong foundation to comprehend the potential of security automation. It provides inspiration for more complex programs ‘ upcoming implementations, acts as a success indicator, and allows for the reporting of results.
The tool is vendor-agnostic, but it works well with a security practitioner-developed platform called Tines to assist other security practitioners in automating their mission-critical procedures.
What is the operation of the SOC Automation Capability Matrix?
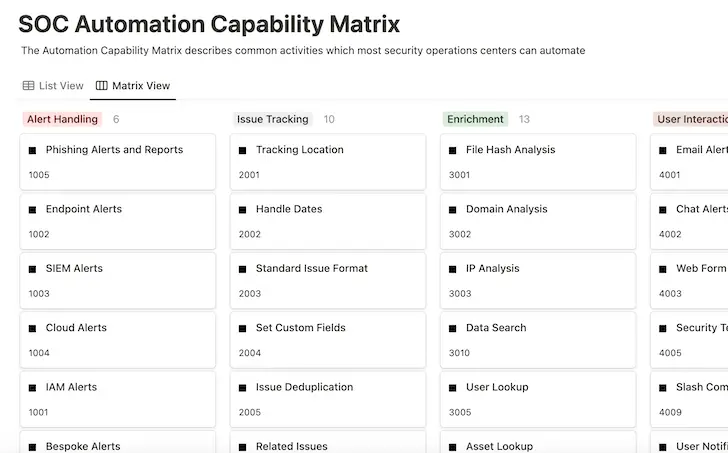
Automation-related categories make up the SOC ACM.
Each capability consists of:
- An overview of the capability’s activities is provided in the description.
- Techniques, technology, and agnostic concepts for putting the capability into practice
- Examples and pertinent Tines library workflow templates
- References and additional research that improves the capability
Within categories, the framework reads from top to bottom and left to right. The framework can be modified to fit what organizations find to be most valuable, even though there is little disagreement about which capabilities are more valuable or simpler to implement.
In the matrix, each capability can exist independently, but combining several capabilities can result in outcomes that are much more intricate and powerful.
Utilizing the SOC Automation Capability Matrix
Then, using the phishing response as an example, we’ll demonstrate how to use the SOC ACM. In order to properly respond to malicious emails, many organizations use a variety of techniques to identify and analyze suspicious messages.
Here are some procedures that a typical phishing investigation might involve:
- phishing email or alert
- For processing, notify the security team by sending a notification.
- To monitor and record the analysis, create a ticket.
- Examine the email’s components, such as attachments, links, and message headers.
- Remove the email and add features to blocklists if you think someone is suspicious.
- Send a status update notification to the recipient.
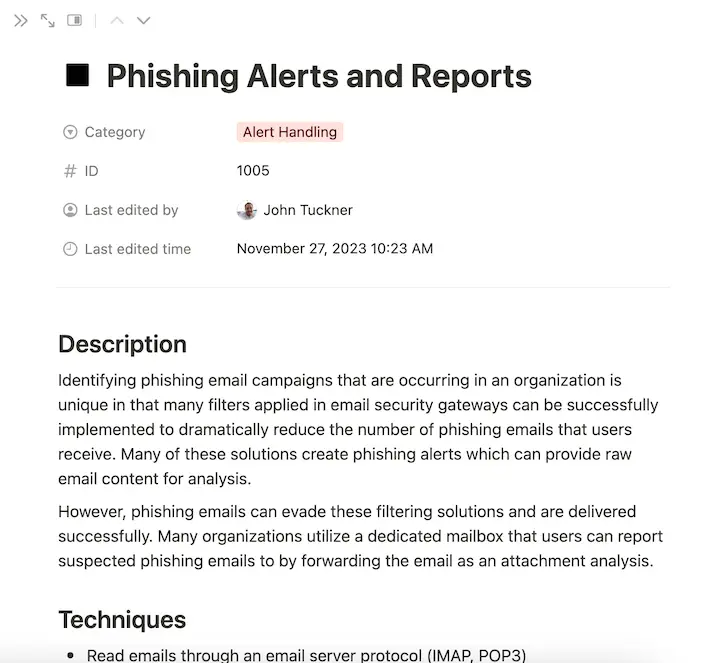
Phishing Alerts, which are included in the matrix capability, mention how many businesses use tools like email security gateways to stop the delivery of suspicious emails to inboxes and to automatically generate alerts of attack campaigns.
Users can easily forward phishing emails that may have gotten through the filters by using the capability to design a purposeful inbox. An opportunity to start an automation workflow is presented by implementing both of these capabilities.
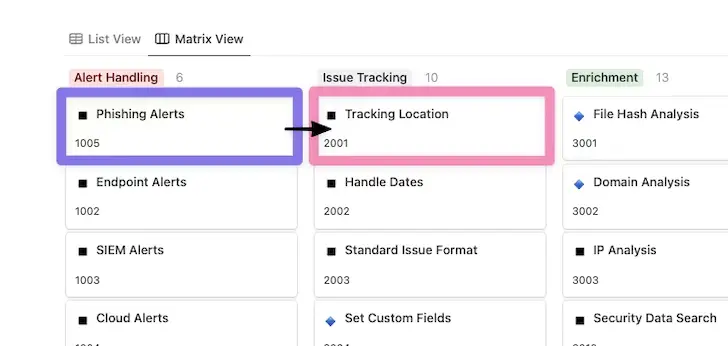
More automation options are made available once a suspicious message has been discovered, either through user reporting or generated alert. One suggestion is to set up a location as soon as you can for tracking each alert’s lifecycle.
We can determine where these alerts should be updated, recorded, and reported by using the Tracking Location feature in the issue tracking section. Take note of how the workflow has expanded the process by moving between the Automation Capability Matrix’s sections.
We can proceed to conduct a thorough analysis of the relevant phishing alert once the alert and tracking location have been determined. Phishing emails are frequently sent from spoofed sources and frequently include suspicious links and potentially malicious attachments to collect authentication data.
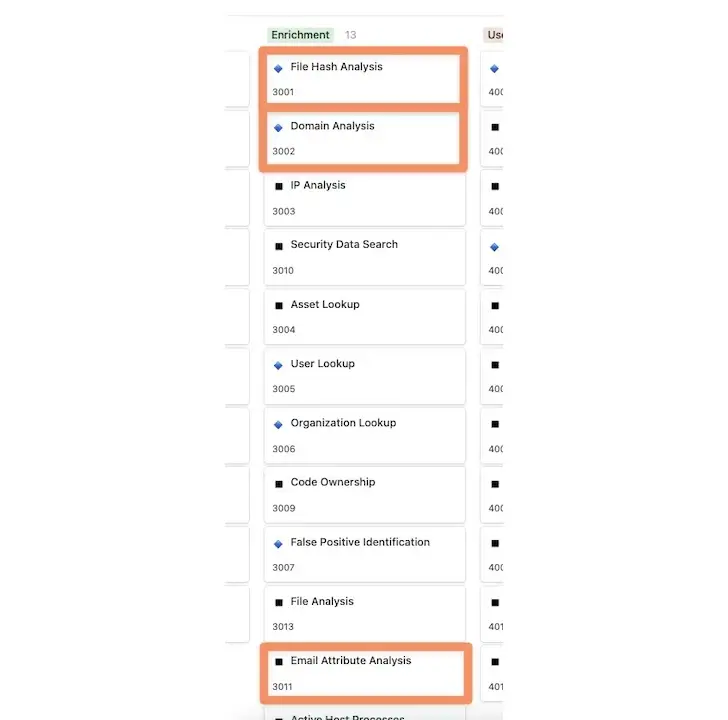
As we move into the enrichment phase, we want to concentrate on using a few essential tools at the very least: Email Attributes to examine email headers for indications of emails coming from spoofed addresses, File Hash Analysis/File Analysis to look at any attachments to the email, and Domain Analysis for any links present in email body.
The variety of API-driven tools and services that can be used to offer these capabilities is exponentially increasing in terms of enrichment opportunities. VirusTotal for files, URLscan for domains, and EmailRep for sender information are a few popular choices. To document the outcomes and give analysts a view of the results, each of these enrichment results can be recorded in the associated tracking location that was previously identified.
This demonstrates how many capabilities from the same section can be used to automate a workflow in this instance, giving analysts as much information as possible.
After enrichment, a decision may already be made, but it’s more likely that an analyst will need to quickly review the situation. The User Interaction section becomes crucial at this point.
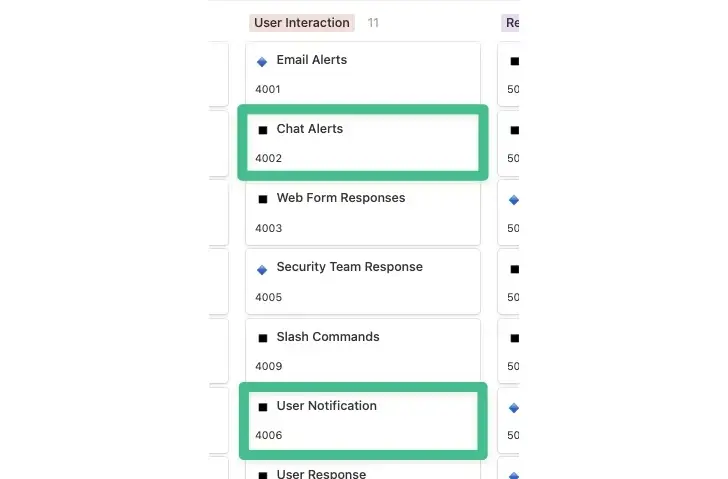
A phishing email has arrived, a tracking issue has been created, and various enrichment details have been added as more context is ready for review. To start, we can use chat alerts to let the security team in your Slack channel know.
The security team will be informed, but what about updating any users who may have been harmed or whose email was reported? Because many businesses actively train users to report emails they may find suspicious, phishing response processes in particular are distinctive. A great way to support processes like quickly signing sensitive documents or preventing widespread malware outbreaks is to provide these users with a confident verdict quickly.
To accomplish this, we can use the User Notification feature to track down the email reporter and give them access to the analysis ‘ findings. When it comes to user interaction, it’s not just about giving the security team more notice, but also about broadening the audience and giving them real-time information to help them make informed choices.
There has been a lot of activity up to this point, and we are very knowledgeable. Even though more information is always beneficial, the corrective action is ultimately what matters most, leading to the remediation phase. We can take corrective action with the help of many of the data points ( indicators ) we previously gathered. We could take a few of the following actions, depending on how things turned out:
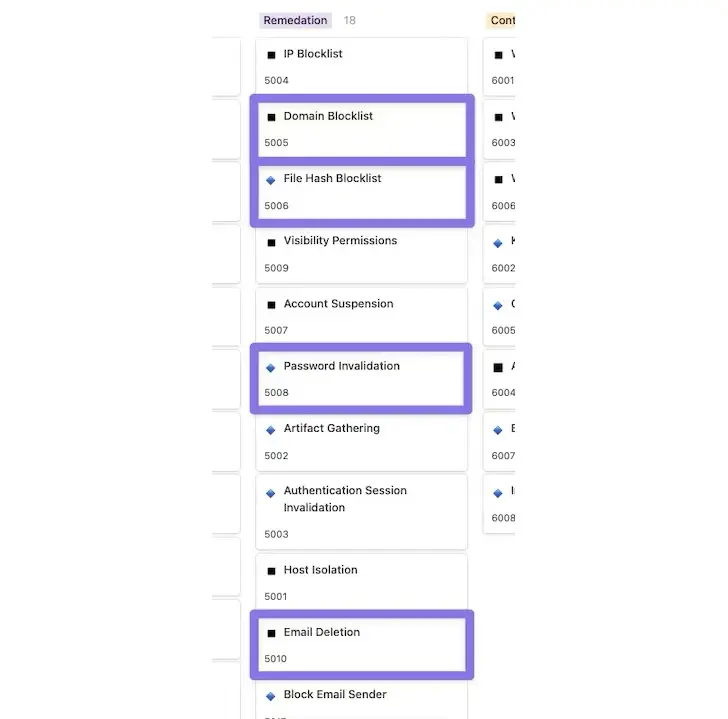
- Add any suspicious-looking domains and URLs to a blocklist by adding them.
- Any file hashes that have been flagged as malicious should be added to a blocklist.
- Email removal: Remove emails from inboxes that are connected to an attack campaign.
- Change any users ‘ passwords who are discovered to have provided credentials to a phishing website to prevent password invalidation.
Knowing what’s possible and starting small is essential for any remediation, especially when using automation to increase confidence. Offering links or buttons that must be manually clicked in order to take corrective action in a repeatable way is one way to achieve this. Keeping lists of suspicious domains that can be blocked offers you great utility, little risk, and the ability to quickly fix errors with little overall impact if you want to implement full automation.
We have used the following capabilities to help automate crucial actions for many cybersecurity teams by looking at the entire process:
- Alerts for phishing
- location tracking
- analysis of filehash
- analysis of domains
- email addresses
- alerts for chats
- notification from the user
- blocklist for domains
- Blocklist for a file
- deletion of emails
- invalidation of the password
The fact that many of these capabilities can now be used for other purposes, like malware detection or handling suspicious logins, makes each subsequent automation opportunity easier. This is a significant advantage of developing these abilities in your organization to address one process, such as phishing.
The matrix can be customized
For those who would rather contribute or run the SOC ACM themselves, it is also accessible on Git Hub.
The SOC ACM can be completely tailored to your requirements in this way. This covers the following:
- Adding fresh capabilities and categories
- reorganizing to reflect your priorities
- tracking automation processes that meet these requirements
- exporting the configuration
- Modes of darkness and light
By making separate boards, you can evaluate various settings or organizations in a different way. For instance, you can use the matrix to visualize an environment entirely differently if your company buys a business with different capabilities than yours.
For privacy, you can store all of this configuration locally in your browser. Without a login account and without any tracking, you can import the configuration in addition to exporting it in order to revive previous assessments.
As a reporting tool, the SOC ACM
The matrix can be used by teams logging into the SOC ACM on GitHub to visually show leadership and other important stakeholders where they are in their automation journey.
Teams will quickly realize which capabilities they are using the most, the activities that go along with them, and their value, such as time saved or decreased response time, after implementing a few capabilities. They can then discuss their findings with pertinent teams and choose their next course of action.
Case study: using the SOC ACM to track executions and time saved
John Tuckner, the creator of the SOC Automation Capability Matrix, discussed how he used the matrix to evaluate and improve a fintech company’s automation program at the Tines Roadshow. They explained to Tuckner that” The Automation Capability Matrix aids in workflow organization, pinpoints the workflows that are saving us the most time, and identifies opportunities for the future.”
Highlights:
- Implemented and tagged 25 capabilities
- 10 workflows with 2, 000 executions using Slack Commands to slash
- Send multifactor prompt workflows saved 6.5 % of time each month by running 721 times.
Recommendations:
- Take a look at the” IP list,” “domain list, and “hash list” management lists for IOCs ‘ response capabilities.
- Use case management to document and highlight the time-saving efforts made.
What they’ll do differently in the future:
- Distributed alerting and Slack user interaction
- notification from the user
- response from the user
- Using a Slack bot, route reports, and asks to the appropriate subteam, users can updating security Slacker channels and incident reports.
- Alert the police to an emergency
- escalations that are timed
- Commands to slash
- Through our Slack bot, add more Tines automation response actions.
- gathering of artifacts
- MFA device disabling
- Asset lookup ( need to include cloud assets, not just endpoints )
Teams can use the SOC Automation Capability Matrix as inspiration for their upcoming automation builds and as a tool to evaluate their automation program at any point along the automation journey.
The Tines team hosts the SOC Automation Capability Matrix on Notion, where you can learn more about it.