All public repositories on GitHub automatically enable push protection in order to prevent accidentally exposing access tokens and API keys when pushing new code.
The company introduced push protection in beta almost two years ago, in April 2022, as a simple way to prevent sensitive information leaks automatically, with today’s announcement. In May 2023, the feature became widely accessible for all public repositories.
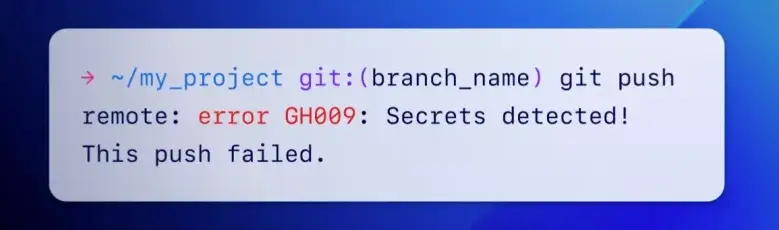
Push protection actively stops leaks by checking for secrets before “git push” operations are accepted and preventing commits when a secret is discovered.
By spotting more than 200 different token types and patterns from more than 180 service providers ( AP I keys, private keys, secret keys, authentication tokens, access tokens, management certificates, credentials, and more ), GitHub claims the secret scanning feature automatically stops secrets from leaking.
” We started the rollout of push protection for all users this week. You will have the option to remove a supported secret from your commits or, if you think it’s safe, to bypass the block, according to Git Hub’s Eric Tooley and Courtney Claessens.
You can check status and opt-in early in the code security and analysis settings, but it might take a week or two before this change affects your account.
Users of GitHub can avoid the automated commit block, even with push protection turned on by default for all public repositories. They can completely deactivate push protection in their security settings, though it’s not advised.
Organizations that are enrolled in the GitHub Enterprise plan can use GitHub Advanced Security, which secures sensitive data in private repositories. Additionally, this includes a number of additional secret scanning features, as well as code scanning, AI-driven code suggestions, and other static application security ( SAST ) features.
According to Tooley and Claessens, “accidental leaks of API keys, tokens, and other secrets risk security breaches, reputation damage, and legal liability on a mind-boggling scale.”
” Over 1 million leaked secrets were discovered by GitHub in just the first eight weeks of 2024,” according to Git Hub. Every minute, there are more than a dozen unintentional leaks.
This GitHub documentation page contains more information about using push protection from the command line or allowing some secrets to be pushed.
Exposures of credentials and secrets have resulted in numerous high-impact breaches [1, 2, 3], as BleepingComputer has reported in recent years.











