The United States government is putting a stop to ransomware attacks targeting the healthcare industry that have recently risen, as recently as this month.
The healthcare industry has been the most frequently impacted by the nearly 70 leaked victims since mid-December 2023, according to the government’s updated advisory.
According to the ALPHV/BlackCat administrator, this is likely in response to a post encouraging its affiliates to target hospitals in response to early December2023’s operational action against the organization and its infrastructure.
The Federal Bureau of Investigation ( FBI ), the CISA ( CISA ), and the HHS ( HHS) are the recipients of the alert.
After a coordinated law enforcement operation led to the sequestration of its dark leak sites, the BlackCat ransomware operation suffered a significant blow late last year. After the group gained control of the sites and switched to a new TOR data leak portal, which is still active to this day, the takedown ended up being unsuccessful.
In recent weeks, it has also attacked crucial infrastructure organizations, including UnitedHealth Group subsidiary Optum and LoanDepot, which it claims is responsible for attacks.
The U.S. government has received up to$ 15 million in financial rewards for information that leads to the identification of key members and e-crime group affiliates as a result of this development.
Following similar disruption efforts led by the U.K. National Crime Agency (NCA ) last week, BlackCat’s ransomware spree coincides with LockBit’s return.
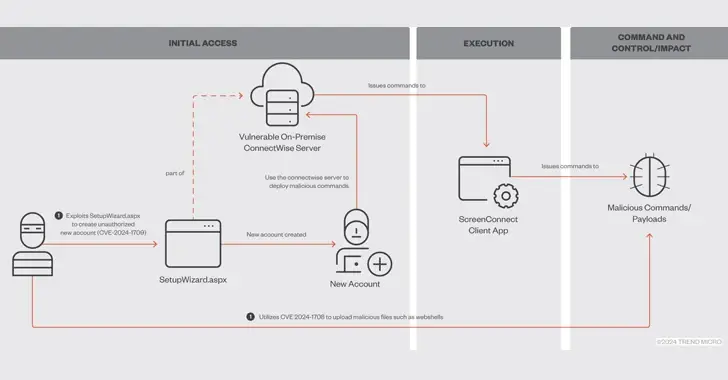
Threat actors used ConnectWise’s ScreenConnect remote desktop and access software’s recently discovered critical security flaws to breach Optum’s network, according to a report from SC Magazine.
The vulnerabilities that allow remote code execution on vulnerable systems have also been used by the Black Basta and Bl00dy ransomware gangs as well as other threat actors to distribute Cobalt Strike Beacons, XWorm, and even other remote management tools like Atera, Syncro, and another ScreenConnect client.
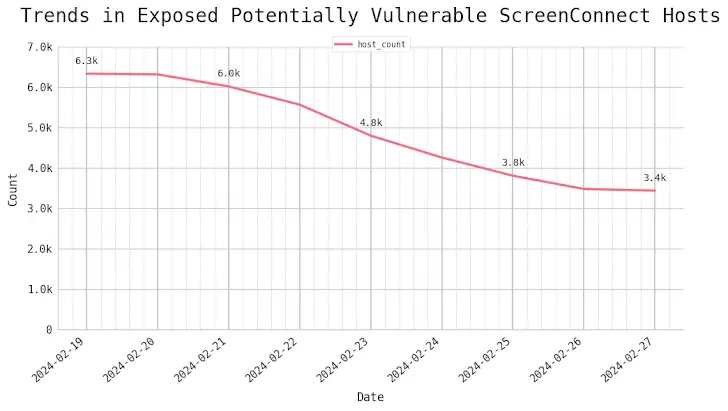
As of February 27, 2024, attack surface management company Censys reported that it had discovered no fewer than 3,400 potentially vulnerable ScreenConnect hosts online, the majority of which were located in the United States, Canada, Australia, Germany, France, India, the Netherlands, Turkey, and Ireland.
According to Censys security researcher Himaja Motheram, it is obvious that threat actors continue to target remote access software like ScreenConnect.
The findings come as ransomware-related organizations like RansomHouse, Rhysida, and a Phobos variant called Backmydata have continued to compromise various organizations in the United States, the UK, Europe, and the Middle East.
RansomHouse has created a custom tool called MrAgent to deploy file-encrypting malware at a scale as a sign that these cybercrime organizations are adopting more nuanced and sophisticated strategies.
The sole purpose of” MrAgent is a binary that runs on]VMware ESXi] hypervisors,” according to Trellix, is to track and automate the deployment of ransomware across large environments with a lot of hypervisors. MrAgent’s details first became public in September 2023.
According to KELA, some ransomware organizations have also adopted the sale of direct network access as a new monetization strategy through their own blogs, on Telegram channels, or data leak websites.
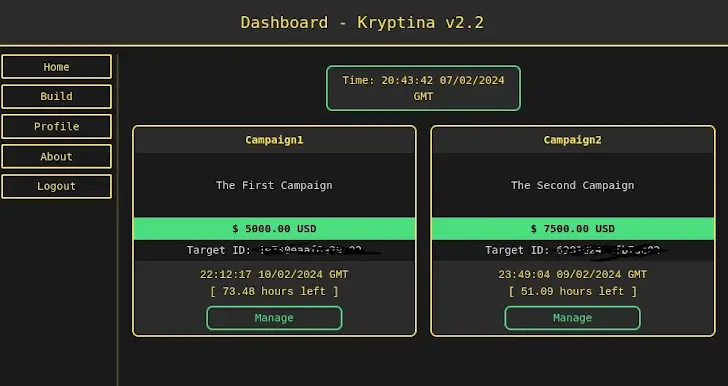
It also follows the public release of Kryptina, a C-based ransomware threat that was discovered in underground forums in December 2023, and has since been made freely available on BreachForums by its creator.
According to SentinelOne researcher Jim Walter,” the release of the RaaS source code, complete with extensive documentation, could have significant effects on the spread and impact of ransomware attacks against Linux systems.”
It is likely to make the ransomware builder more appealing and user-friendly, enticed by the ecosystem’s low-skilled users. There is also a significant chance that it will cause more spin-offs to develop and there will be more attacks.