Up to$ 15 million in cash rewards have been announced by the U. S. State Department for information that could help identify important members of the LockBit ransomware group and result in their arrest.
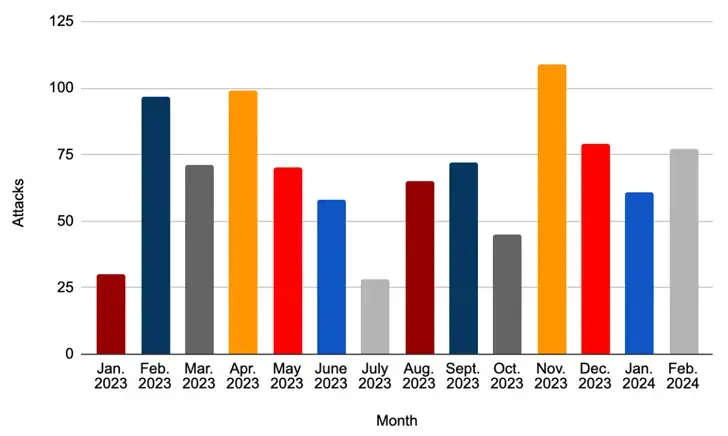
According to the State Department, LockBit actors have carried out more than 2, 000 attacks on victims worldwide and in the United States since January 2020, resulting in costly operational disruptions and the exfiltration or destruction of sensitive data.
” To recover from LockBit ransomware events, more than$ 144 million has been paid.”
The development comes as part of a massive law enforcement campaign spearheaded by the U.K. National Crime Agency (NCA ) that has disrupted LockBit, an international ransomware gang linked to Russia for more than four years.
Russian e-crime organizations that operate with impunity by taking advantage of the fact that they are outside the purview of Western law enforcement profit from ransomware as a service ( RaaS ) operations like LockBit and others that extort businesses by stealing their sensitive data and encrypting it.
In order to carry out the attacks using LockBit’s malicious infrastructure and software, the core developers frequently use a network of affiliates. In turn, it is well known that affiliates use initial access brokers ( IABs ) to buy access to desired targets.
Since Conti left the scene in the middle of 2022, LockBit has become the most active ransomware group, according to Chester Wisniewski, global field CTO at Sophos.
They have become the most destructive in recent years due to their frequent attacks and lack of restrictions on the types of infrastructure they can destroy. Law enforcement benefits greatly from anything that interferes with their operations and fosters mistrust among their partners and suppliers.
In 2022, LockBit, the first ransomware organization, announced a bug bounty program with rewards of up to$ 1 million for discovering security flaws in website and locker software.
According to Intel 471, LockBit’s business expanded by consistently releasing new product features, offering excellent customer service, and occasionally engaging in marketing stunts like paying customers to have their own logo tattoos done on them.
 |
” LockBit changed the rules, allowing its affiliates to take the ransom and paying a portion of it.” This increased affiliates ‘ confidence that they would n’t lose out on a payment, which led to an increase in affiliate traffic.
From July 2020 through January 2024, the SecureWorks Counter Threat Unit ( CTU), which is monitoring the organization as Gold Mystic, said it looked into 22 LockBit ransomware compromises, some of which only used data theft to extort victims.
The cybersecurity firm added that LockBit was able to grow and attract a number of affiliates over time thanks to its practice of delegating control to them to handle ransom negotiations and payments.
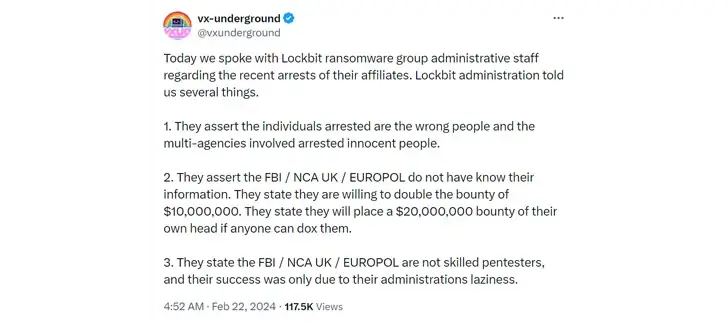
Following a months-long investigation that began in April 2022 and resulted in the arrest of three affiliates in Poland and Ukraine, the indictment of two additional alleged members, and the seizure of 34 servers and 1, 000 decryption keys that can aid victims in recovering their data without having to pay, LockBit was taken down.
A 38-year-old man from Warsaw and a “father and son” duo from Ukraine are among the people who have been detained. Between January 31, 2022, and February 5, 2024, LockBit is thought to have employed about 194 affiliates, all of whom were using StealBbit, a specialized data exfiltration tool.
The NCA stated that LockBit’s attempt to provide its affiliates with a comprehensive “one-stop shop” service is exemplified by the fact that the executable is used to export the data before StealBits in an effort to avoid detection.
However, due to these RaaS brands ‘ fluid structure, closing them down might not have a significant impact on the criminal enterprise, allowing them to regroup and reappear under new names. It wo n’t be long before they rebrand and pick up where they left off, if the recent history of similar takedowns is any indication.
According to ZeroFox,” Comprehensive degradation of LockBit’s infrastructure will likely result in a brief cessation of activity by LockMit operatives before they resume operations—either under the name of the company or another banner.”
Wisniewski continued,” A win is still a win even if it means imposing disruption, inciting their fear of being discovered, and escalating the friction of running their criminal syndicate,” as was the case with QakBot. ” Until we can put them all in jail, where they belong, we must continue to work together to raise their costs ever higher.”