Threat actors have the ability to use the well-known utility command-not-found to recommend their own rogue packages and compromise systems running the Ubuntu operating system, according to cybersecurity researchers.
While” command-not-found” is a useful tool for suggesting installations for uninstalled commands, attackers can unintentionally manipulate it through the snap repository, resulting in misleading recommendations of malicious packages, according to data from cloud security company Aqua.
When attempting to run commands that are not available on Ubuntu systems, command-not-found suggests packages to install in interactive bash sessions. Both snap packages and the Advanced Packaging Tool ( APT ) are suggested.
when the tool makes use of a local database ( /var/lib/command-not-found ) It uses the “advise-snap” command to suggest snaps that provide the given command in order to” suggest” APT packages.
Therefore, software supply chain attacks may be made possible if an attacker is able to exploit this system and has their malicious package recommended by the command-not-found package.
According to Aqua, there is a security flaw that allows threat actors to use the alias mechanism to register the appropriate snap name and deceive users into downloading the malicious software.
Additionally, a malicious snap could be uploaded by an attacker using the name of an APT package, which would then be suggested when the user entered the command on their terminal.
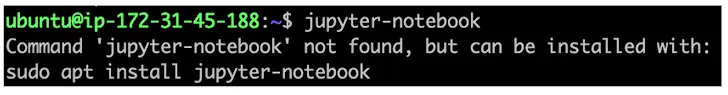
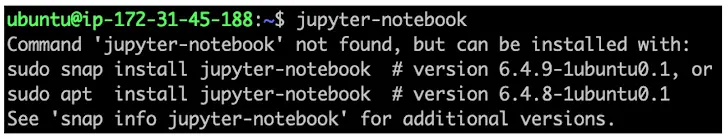
According to Aqua security researcher Ilay Goldman, the maintainers of the” jupyter-notepad” APT package had not claimed the corresponding snap name. ” This error gave an attacker the chance to seize it and upload a malicious snap with the name” jupyter- notebook.”
Even worse, the command-not-found utility misleads users into installing the fake snap package by placing it above the official APT package for jupyter-notebooks.
According to Aqua, malicious actors can impersonate up to 26 % of the APT package commands, which poses a serious security risk because they could be linked to an attacker’s account.
A third category entails typosquatting attacks, in which users ‘ typographical mistakes ( such as ifconfigg rather than fconfig ) are used to register a fake snap package under the guise of “fetchg” to suggest bogus snap packages.
In this scenario, command-not-found “would mistakenly match it to this incorrect command and recommend the malicious snap, bypassing the suggestion for “net-tools” altogether,” according to Aqua researchers.
The company is advising users to check the source of a package before installation and the credibility of the maintainers in order to prevent the misuse of command-not-found utility to recommend counterfeit packages as an urgent concern.
To stop commands from being misused, developers of APT and snap packages are also advised to register the associated snap name for their commands.
Underscoring the need for increased vigilance and proactive defense strategies, Aqua said,” It is still unclear how extensively these capabilities have been exploited.”