Numerous high-profile social media accounts have been compromised and used to spread malicious content intended to steal cryptocurrency as part of a recent wave of Twitter/X account takeover attacks.  , The attacks make use of a class of malware known as crypto-drainers, which is frequently made available via Drainer- as-a-Service ( DaaS ) platforms.  , The SEC and Mandiant are two recent high-profile victims.
Despite being around since at least 2021, security researchers have n’t paid much attention to crypto drainers and drainage systems as a service to date. To better understand this family of threats and how it affects organizations, we focus on Crypto Drainers and DaaS in this post.
Introduction to Crypto Drainers and DaaS
A malicious tool or script known as a crypto drainer is specifically created to transfer or redirect cryptocurrency from the victim’s wallet to the wallet of an attacker. Around 2021, MetaMask-targeting drainers first appeared, and they were widely distributed in marketplaces and underground forums.
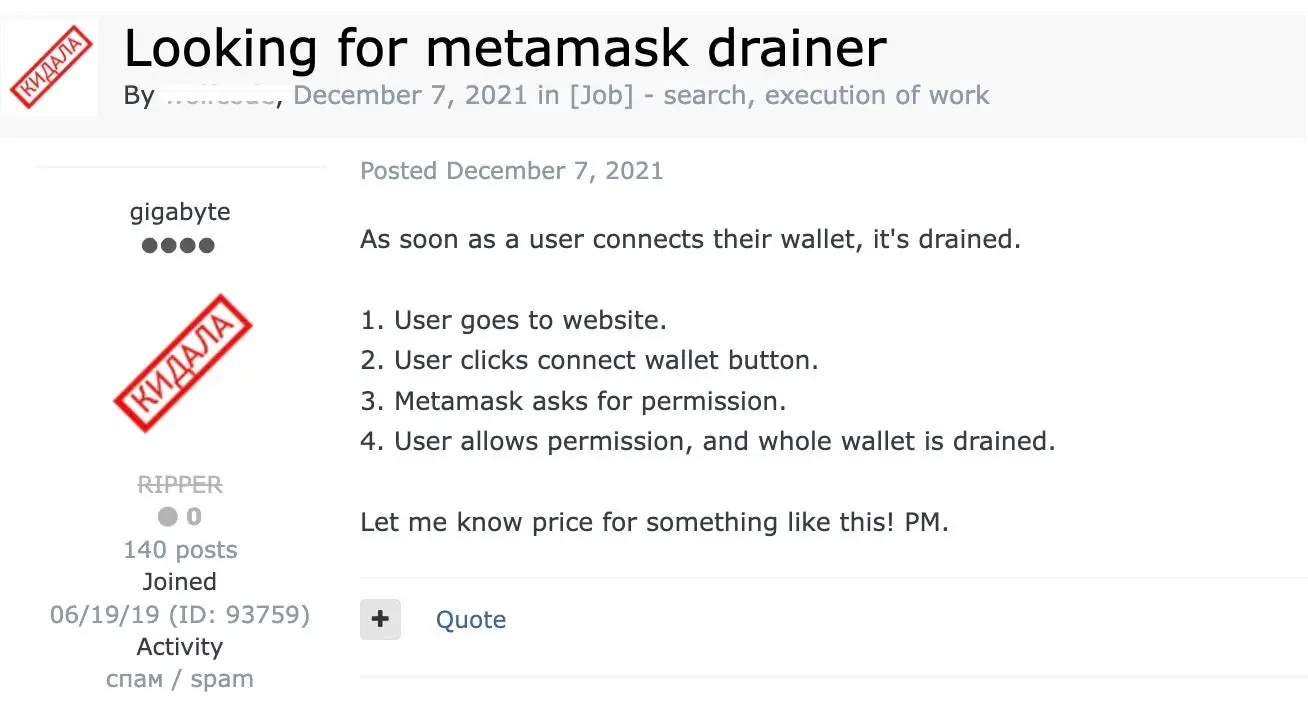
However, there are various types of drainers and drainer-style attacks. Malicious smart contracts might have hidden features that allow for unauthorized transfers. Other types of drainers might use NFT or token-based triggers to create fictitious resources, which would then make it easier to transfer cryptocurrencies covertly and illegally.
With DaaS vendors offering software and support to cybercriminals in exchange for a percentage of the stolen funds, cryptocurrency drainers are frequently offered through the Drainer- as-a-Service model. Services that a modern DaaS typically provides include
- Crypto-draining scripts that are turnkey
- Flexible smart contracts
- Social engineering services and phishing kits
- Security and anonymity or premium OPSEC services
- assistance with integration and mixing/obfuscation
- maintenance, technical support, and ongoing updates.
For instance, turnkey or ready-to-use crypto draining scripts are used to make it easier to automate the removal of cryptocurrency from target wallets. They are designed to be easy to understand and use, requiring little to no prior knowledge.
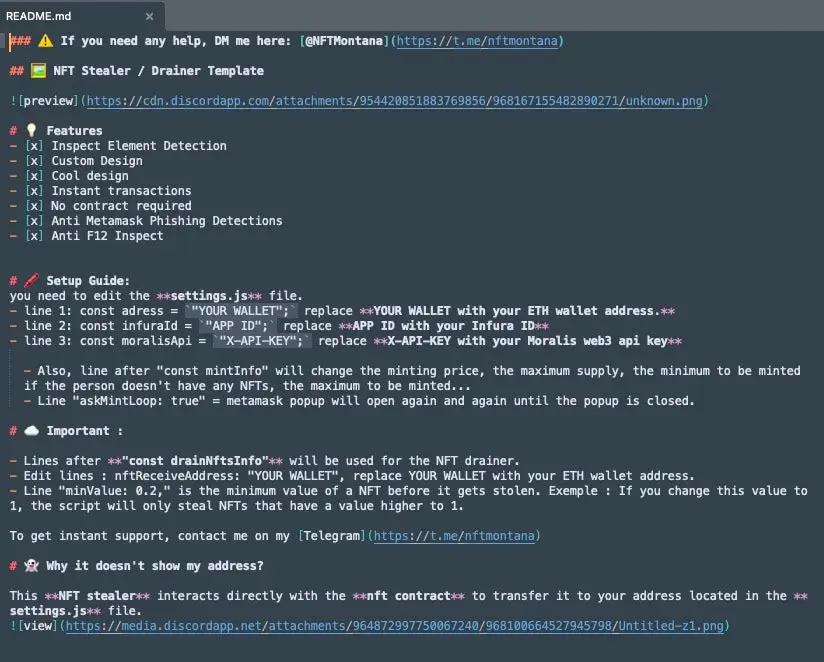
The stolen cryptocurrency is distributed among the Daas operators and affiliates ( DaaS users ). Depending on the services offered, operators typically take between 5 % and 25 % of the cut.
Attacks on account takeovers are a threat.
When threat actors successfully seize control of high-profile social media accounts and use them to push malicious content to large audiences from what appears to be a trusted source, as recently happened to Mandiant and the U. S. Securities and Exchange Commission, crypto draining can be extremely profitable for them.
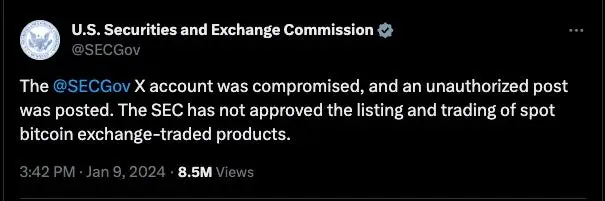
CertiK and Bloomberg Crypto are two additional high-profile account takeovers. A crypto drainer allegedly stole$ 59 million from 63, 000 people using more than 10,000 phishing websites in late December.
These attacks typically start with a password attack using brute force. This entails methodically trying every possible password until the right one is discovered. Accounts without 2FA or MFA are more susceptible to attacks of this nature.
An attacker is able to distribute phishing links to websites hosting drainers once they have access to the account. For instance, they might post content from the account and offer users who visit the site and complete a transaction free NFTs or other rewards. Unknowingly, victims are all too eager to connect their wallets because they think they will get something worthwhile, but they are unaware that the website has a drainer script that will empty their pockets.
Attackers use trusted but compromised accounts ‘ trust and reach to target more victims by using platforms like X, Telegram, and Discord to spread their phishing links.
Attack Anatomy | CLINKSINK Drainer
Attackers in the Mandiant incident used the obfuscated JavaScript drainer CLINKSINK, which was waiting for victims to fall for phishing links with cryptocurrency-themed lures. These allures frequently pass for legitimate cryptocurrency resources like BONK, DappRadar, and Phantom.
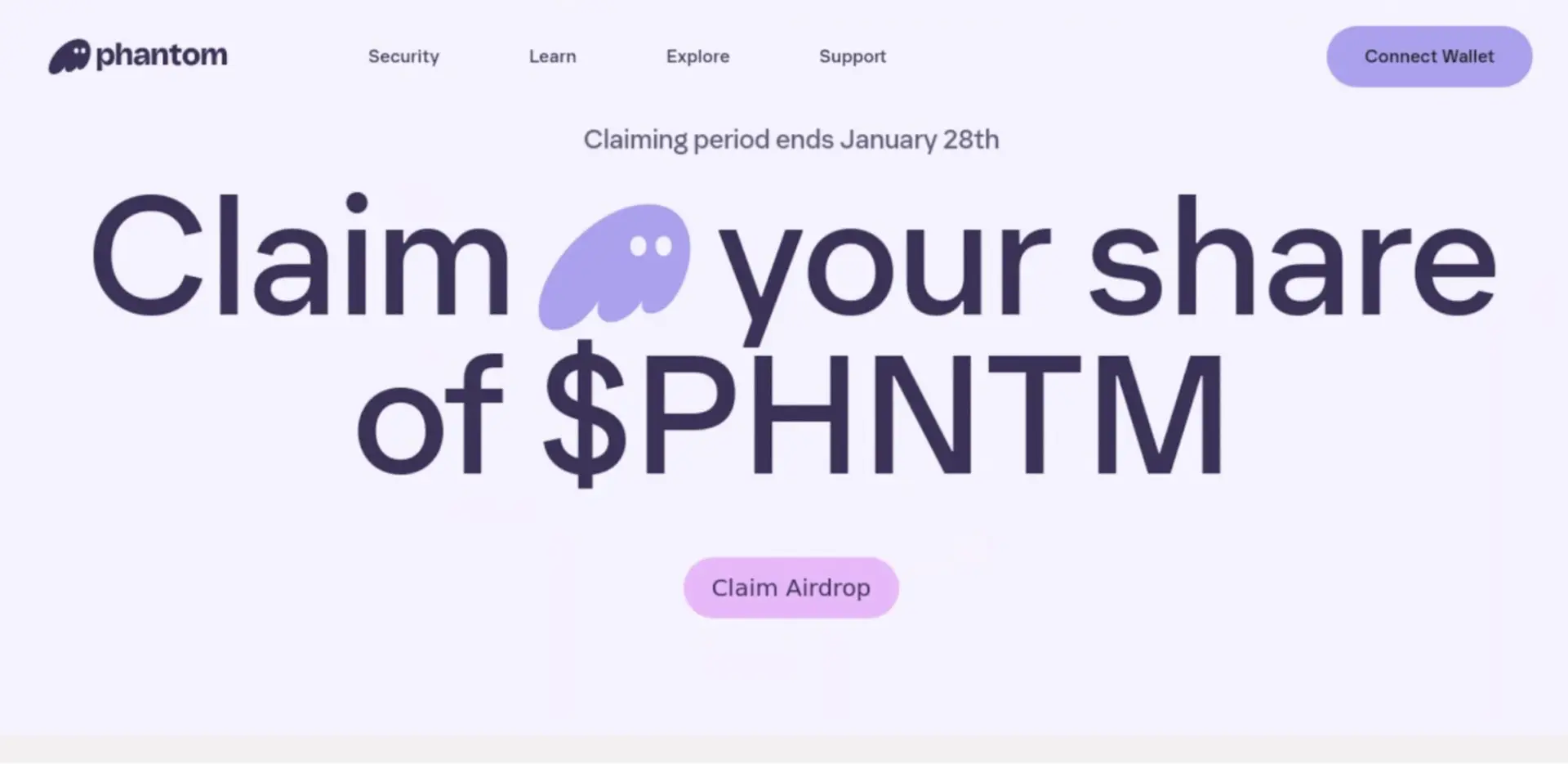
To receive an “airdrop,” which is the distribution of tokens or coins to other wallet addresses as a reward or promotion, victims are persuaded to connect their wallets. Then, in order to complete the transfer, they are asked to sign a” transaction.” The victim uses their private key to authenticate themselves on the blockchain network, making this the most important step for crypto thieves. The user can then continue the crypto draining process to transfer the victim’s wallet contents to their own if they successfully complete this step.
According to Mandiant, 42 distinct wallet addresses were used to receive stolen money in recent CLINKSINK campaigns, including the one connected to the company’s recent takeover of its Twitter/X account. The CLINKSINK malware is used by a number of different DaaS products, and it is currently unknown whether any of them are connected to the specific Mandiant-related incident.
Crypto Drainers Are Increasing in Number
Since 2023, cryptocurrency drainers have gained popularity, and many of them are now promoted on underground markets and Telegram channels. Using CLINKSINK, Mandiant identified Chick Drainer and Rainbow Drainor as two DaaS products. However, it’s also possible that the CLINKSINK source code leaked and was used by a number of other threat actors.
The Multi-chain Drainer from Rugging and Angel Drainor are two additional DaaS products that are being widely and openly marketed.
A Daas called Angel Drainer debuted around August 2023 and provided tools and services that were concurrently advertised on Telegram by well-known threat actors like GhostSec. The operators also demand affiliates to make an initial deposit of between$ 5000 and$ 10000 in addition to receiving a 20 % cut.
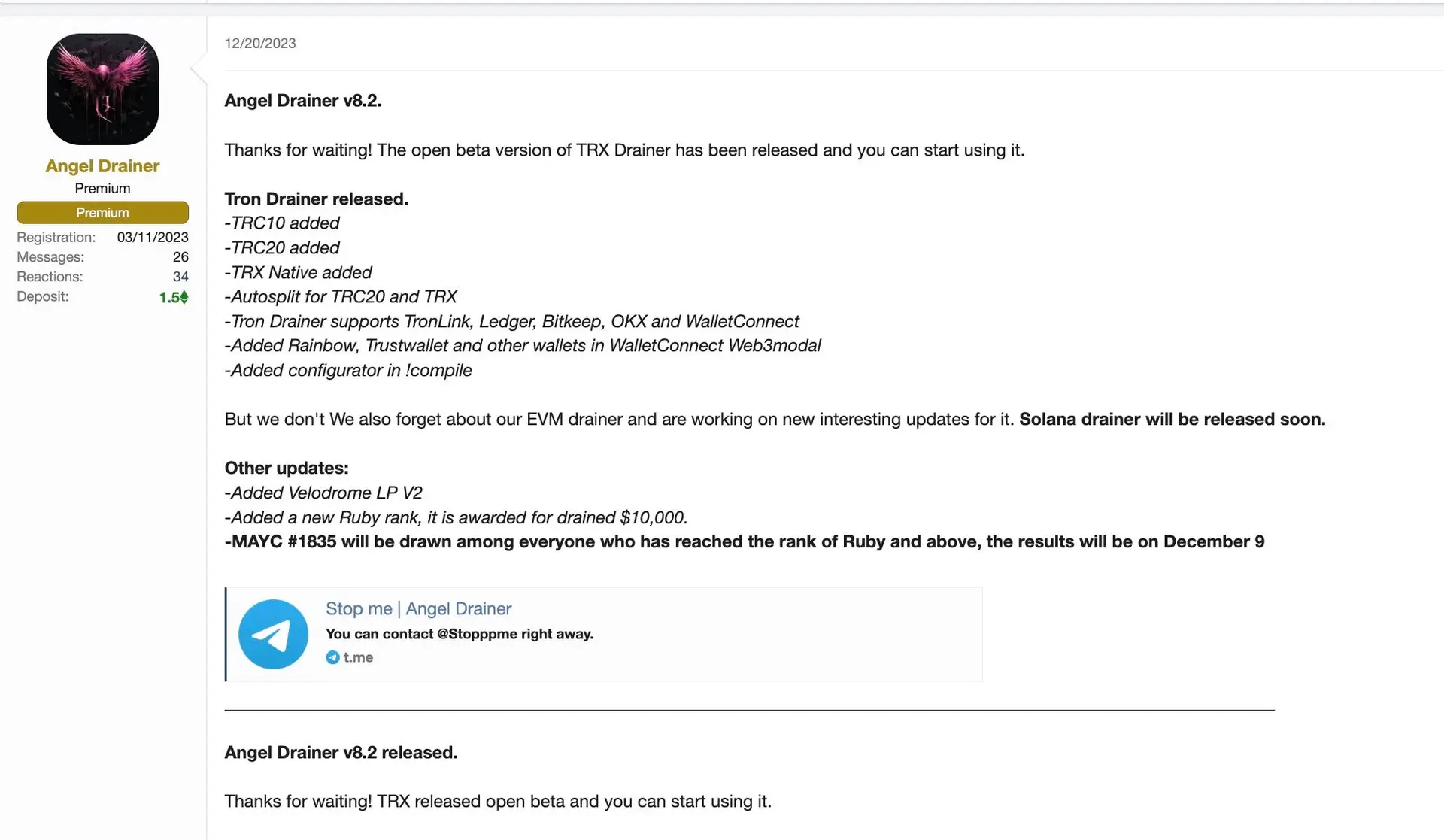
Another product that claims to support 20 different crypto platforms is Rugging’s Multi- chain Drainer. The operators try to entice affiliates by charging them a low fee, which is between 5 and 10 % of their affiliate earnings.
Avoiding Drainer Attacks
Although the main goal of crypto drainers is to steal cryptocurrency assets from people, businesses and organizations should be on the lookout because their social media accounts could end up in the attack chain. Companies that deal with cryptocurrency assets may also put employees or business units at risk.
It is crucial to make sure that 2FA or MFA is enabled for all social media accounts in order to counter the threat of attacks from crypto drainers. Users of cryptocurrencies are advised to use the same level of caution and watch out for attempts at social engineering when using NFTs, “airdrops,” and other crypto advertisements. Users should think about switching to hardware-based wallets for added security.
Conclusion
Similar to Ransomware- as a Service ( Raas ) before it in terms of skill, low risk, and high reward, Drainer offers those with malicious intent an easy entry point into the crimeware ecosystem. And, as with Raas ‘ previous offerings, we wo n’t be surprised to see competition among DaaS operators lead to a race to the lowest price, tempting even more into malicious activity.
Credentials and access to social media accounts should be given the same security considerations as other business services because it is now possible to harm a business much more severely than just deface it or deny it service. Contact us or ask for a free demo to find out more about how SentinelOne can help safeguard your business.











