A previously undocumented Unified Extensible Firmware Interface ( UEFI ) bootkit feature has been discovered to be a part of the Glupteba botnet, giving the malware an additional layer of sophistication and stealth.
Lior Rochberger and Dan Yashnik, researchers from Palo Alto Networks Unit 42, said in a Monday analysis that” this bootkit can intervene and control the [operating system ] boot process, enabling Glupteba to hide itself and create an extremely difficult to detect and remove.”
A fully functional information stealer and backdoor, Glupteba can support illegal cryptocurrency mining and install proxies on infected hosts. Additionally, it is well known for using the Bitcoin blockchain as a backup command-and-control ( C2 ) system, making it resistant to attempts to take it down.
It can perform ad fraud, deliver additional payloads, use siphon credentials and credit card data, and even take advantage of routers to get remote administrative access and credentials.
The modular malware has evolved into a sophisticated threat over the past ten years, using complex multi-stage infection chains to avoid detection by security measures.
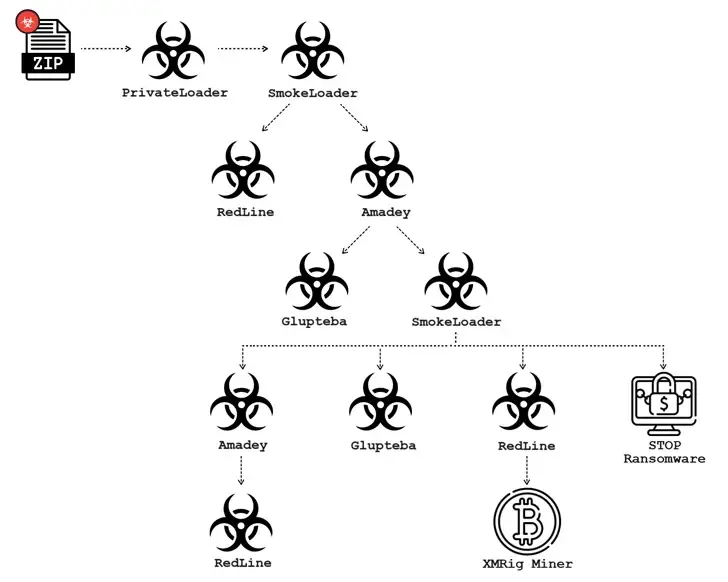
The cybersecurity company has noticed a campaign in November 2023 that involves using pay-per-install ( PPI ) services like Ruzki to distribute Glupteba. Sekoia connected Ruzki to activity clusters using PrivateLoader to spread next-stage malware in September 2022.
This manifests itself in large-scale phishing attacks where PrivateLoader is delivered as installation files for cracked software, which loads SmokeLine, launches RedLine Stealer, and eventually drops Glupteba.
According to the researchers,” threat actors frequently disperse Glupteba as part of a complicated infection chain spreading multiple malware families simultaneously.” ” This infection chain frequently begins with a Smoke or PrivateLoader infection, which loads Glupteba before loading other malware families.”
Glupteba includes a modified version of the open-source project EfiGuard, which has the capability of disabling Driver Signature Enforcement ( DSE ) at boot time, as evidence that the malware is being actively maintained.
It’s important to note that earlier iterations of the malware were discovered to “install a kernel driver the bot uses, and make other changes that weaken the security posture of an infected host.”
Greece, Nepal, Bangladesh, Brazil, Korea, Algeria, Ukraine, Slovakia, Turkey, Italy, and Sweden have all been mentioned as being affected by Glupteba’s resurfaced campaign in 2023.
According to the researchers,” Glupteba malware continues to stand out as a notable illustration of the complexity and adaptability displayed by contemporary cybercriminals.”
The ability of this malware to innovate and evade detection is highlighted by the discovery of an undocumented UEFI bypass technique within Glupteba. The PPI ecosystem also emphasizes the cooperation and monetization tactics used by cybercriminals in their campaigns against widespread infections because it plays a part in the distribution of Glupteba.