You may have noticed that “unified” has quickly become the buzzword that everyone is using to describe their portfolio if you’ve recently listened to software vendors in the identity space. This is fantastic, too! Amazing advantages come from unified identity!
However, there’s always a but, right? Not every “unified” “identity,”” security,” or “platform” is created equal. While some vendors offer a glorified 2FA service that is only unified in the minds of their marketers, others refer to the combination of workforce IDaaS and customerID.
Your surroundings are important!
So put the vendors ‘ claims aside for a moment and consider the security landscape of your company and identity. Take into account this new definition: “unified” refers to a complete identity solution that can combine your identity challenges.
For instance, you are in charge of a large hospital’s identity infrastructure. There are many external users, as well as frontline workers, administrative staff, and audit/compliance requirements. Your LOB application does not perform identity because you are using Active Directory. Strong joiner-leaner-mover handling, AD hardening, and enterprise-grade reporting are all components of this hospital’s unified identity, which also includes strong access management for patients and frontline staff. Anything less keeps their internal identity landscape fragmented and falls short of the unified promise.
A small software development studio is another illustration. To safeguard the development pipeline and prevent them from becoming the primary target of a supply chain attack, they require additional robust controls on Privileged Access Management ( PAM ). However, in order to complete the numerous automated tasks that machine entities and their owners perform, they also require Identity Governance and Administration ( IGA ). A solution that separates PAM and IGA is not unified.
What exactly does a united identity mean?
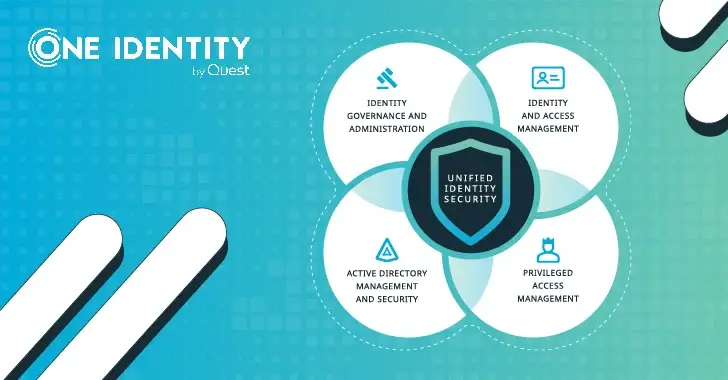
Why then is the term “unified identity” such a popular one? There are some excellent justifications for it, though. The identity space was historically very fragmented, and until relatively recently, many experts did not even consider it to be a single market. The three main sub-markets were Identity Governance and Administration ( IGA ), Access Management ( AM ), and Private Accusations ( PAM ), with numerous nearby areas like AD bridging and endpoint privilege management.
Extreme fragmentation—a large organization typically has 45 different security tools—is the main force behind unified identity. A One Identity survey reveals that half of organizations use more than 25 different systems to manage access rights, adding to the trend of identity sprawl, in which organizations are acquiring more and more identity silos internally. This is simply untenable, and it is impossible to keep up with the constant addition of new tools as threats arise. Organizations are therefore looking to reduce complexity, consolidate vendors, and reduce the number of suppliers they work with. A Unified Identity Platform has advantages such as improved cybersecurity posture, increased security resilience, improved simplicity, and increased agility.
Top line cost is another factor; bundles, volume discounts, and ELAs are all straightforward cost-cutting strategies. A single tech stack helps close the skills gap, relieving the burden of hiring and training. This results in significant headcount savings and may reduce the need for highly trained senior staff, increasing the value of security with fewer resources or, to put it another way, working smarter rather than harder.
One of the biggest challenges in the identity landscape is integration. The smooth integration of security tools is a requirement, but this is rarely the case. Interoperability is very difficult to achieve because the industry is not interested in common standards. Identity solutions can function in tandem with some effort ( i .e., customization, support hours, and overhead ), but it takes a lot of work to build an entire ecosystem of identity tools that function flawlessly. The benefits of a unified identity platform in this situation are clear to see. The platform components are supported as a single unit by the vendor, and the tools are pre-tested and validated to work together, typically without any customization needed.
The final advantage is faster time to value, which is a quality that any MBA graduate should possess. As experts painstakingly formalize business processes and implement them in code or configuration, identity and access management ( IAM ) projects are known for taking a long time to implement. This is a very difficult task for large organizations because the IAM setup must reflect every feature ( and quirk ) that the company has amassed over time, sometimes over many years. Business leaders’ patience is exhausted by the complexity of implementations, which eventually lead to failure. It’s time to value things in IAM, to put it briefly. Additionally, a unified identity solution eliminates at least one aspect of the multi-vendor approach’s complexity.
Let’s discuss a drawback after these advantages: vendor lock-in. Unified identity sounds fantastic, but placing the house’s bet on just one vendor is risky. What if you already have some satisfactory solutions in place? It’s critical to keep in mind that not all unified identity vendors are the same. Some vendors provide modular identity platforms, allowing you to combine your needs and keep your preferences. Customers can begin the unification at any time ( for instance, with PAM ) without having to embrace and implement all areas at once thanks to this strategy. Look for this adaptable strategy when choosing vendors.