The FBI, CISA, and the US Department of Health and Human Services ( HHS) issued a warning about alleged targeted ALPHV/Blackcat ransomware attacks today.
The joint advisory issues a warning that” ALPHV Blackcat affiliates have been observed primarily aimed at the healthcare sector.”
The BlackCat cybercrime gang’s activities since it first surfaced in November 2021 as a suspected rebranding of the DarkSide and BlackMatter ransomware groups are the subject of today’s warning, which comes after an April 2022 FBI flash alert and a second advisory issued in December 2023.
The FBI said the gang has raked in at least$ 300 million in ransoms from over 1, 000 victims up until September 2023 and that over 60 breaches occurred during its first four months of operation ( between November 2021 and March 2022 ).
The three federal agencies issued a joint advisory today warning that” the healthcare sector has been the most frequently victimized” of the nearly 70 leaked victims since mid-December 2023.
According to the ALPHV Blackcat administrator,” this is likely in response to the post encouraging its affiliates to target hospitals after the group and its infrastructure are taken offline in early December 2023.”
Critical infrastructure organizations were advised by the FBI, CISA, and HHS to take necessary mitigation measures to lessen the impact of Blackcat ransomware and data extortion incidents.
Additionally, they’ve urged healthcare organizations to implement cybersecurity measures to combat the most common strategies, methods, and methods used in the Healthcare and Public Health ( PHP ) sector.
BlackCat now has access to ScreenConnect for the first time.
The largest payment exchange platform connecting doctors, pharmacies, healthcare providers, and patients in the United States healthcare system, was linked to a cyberattack on UnitedHealth Group subsidiary Optum, which led to the publication of today’s advisory.
In a statement released to BleepingComputer, UnitedHealth Group VP Tyler Mason claimed that 90 % of the over 70, 000 pharmacies using the affected platform have switched to new electronic claim procedures. However, he did not confirm the BlackCat link.
Since the attack hit its systems, Change Healthcare has been conducting Zoom calls with partners in the healthcare sector, according to sources with knowledge of the investigation.
By forensic experts who were conducting the incident, BleepingComputer learned that the attack was connected to the BlackCat ransomware group and that the threat actors had used the actively exploited critical ScreenConnect auth bypass vulnerability ( CVE- 2024- 1709 ) to breach the network.
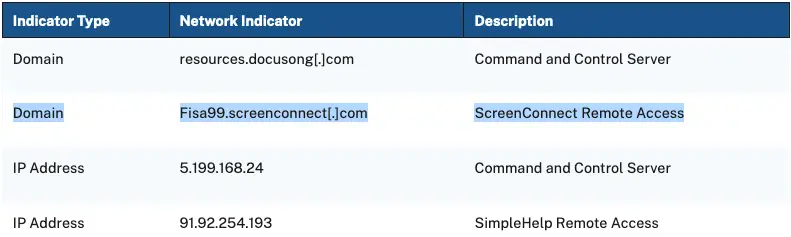
The FBI, CISA, and HHS shared indicators of compromise that support our knowledge that the BlackCat ransomware gang is attempting to remotely access victim networks by targeting vulnerable ScreenConnect servers, despite the fact that today’s advisory was not linked to the Change Healthcare incident.
In December, the FBI shut down its Tor negotiation and leak sites, causing a disruption to the BlackCat gang’s activities. The gang’s servers were also compromised, allowing law enforcement to use the stolen keys to create a decryptor.
Since then, BlackCat has “unseized” their websites and moved to a brand-new, unfinished Tor leak site.
Up to$ 10 million is available for information leading to the identification or location of BlackCat gang leaders, and up to$ 5 million for information on those connected to the group’s ransomware attacks.











