Hackers are launching extensive attacks on WordPress websites to infect other sites ‘ browsers with scripts that force them to crack passwords.  ,
Sucuri, a website security firm known for tracking a threat actor known for hacking websites to inject crypto wallet drainer scripts, first discovered the campaign.
When someone connects their wallet to a malicious script, it is known as a crypto wallet drainer.
The scripts use misleading language to persuade users to link their wallets to these compromised websites when they visit them. The scripts then steal all of the contained assets, though.
Threat actors creating fake Web3 sites with wallet drainers has become a common practice over the past year thanks to these scripts. Then, to promote the websites and steal visitor’s cryptocurrency, they then hack X accounts, make YouTube videos, or take out Google and X advertisements.
According to Sucuri researchers, the threat actors were attempting to inject the AngelDrainer wallet drainer  into a number of waves from different URLs, with the last one being “dynamiclink [. ] lol/cachingjs/turboturbo. js.
The threat actor switched from using visitors ‘ browsers to spoof other WordPress websites in late February. using “dynamic- linx” a malicious script from a recently registered domain com/chx. js’.
constructing a brute force army
The threat actor is using compromised WordPress sites to load scripts that make visitors ‘ browsers use bruteforce attacks on other websites, according to a new report from Sucuri.
A threat actor uses a variety of passwords to crack the correct one as they attempt to log into an account. The threat actor can spoof information, inject malicious scripts, or encrypt files on the site using the credentials.
The threat actors compromise a WordPress site to inject malicious code into the HTML templates as part of this hacking campaign. The scripts are loaded into the browsers of visitors to the website from https ://dynamic-linx. ]com/chx .js.
The threat actors ‘ server at https ://dynamic-linx will be silently contacted by these scripts. To be able to perform a password bruteforcing task, visit [com/get Task .php].
One hundred passwords to try and an ID for the website URL, an account name, a number denoting the current batch of passwords to pass through are all contained in a JSON file that contains the requirements for the bruteforce attack.
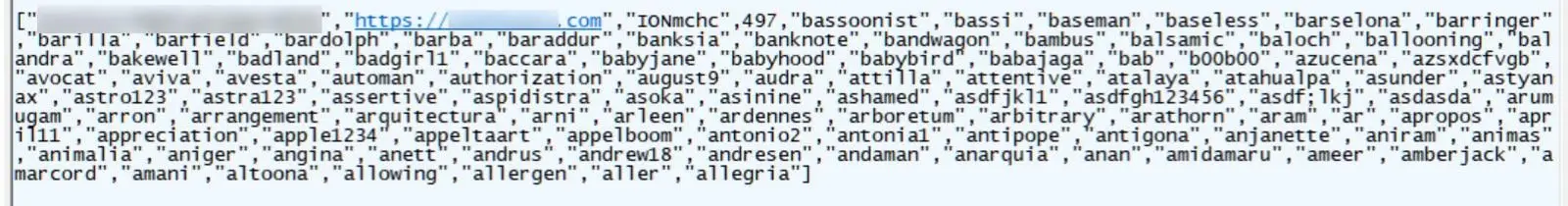
Source: BleepingComputer
The visitor’s browser will use the WordPress site’s XMLRPC interface to quietly upload a file using the account names and passwords stored in the JSON data once the task has been received.
The script will notify the threat actor’s server that a site password was discovered if the password is accurate. The hacker can then access the website and retrieve the uploaded file, which contains the base64-encoded username and password combination.
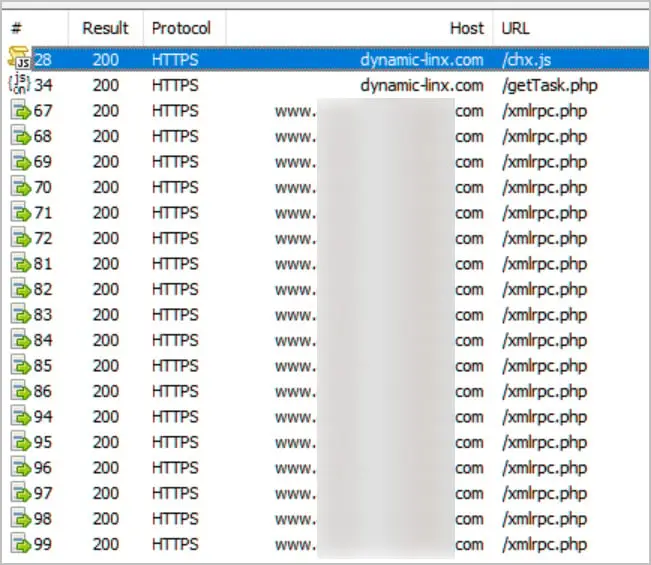
Source: BleepingComputer
The malicious script will cause the web browser to re-connect to the attacker’s server and retrieve a new task as soon as the page is open.
There are currently over 1,700 websites hacked using these scripts or their loaders, which will provide a sizable pool of users who will unwittingly be drafted into this distributed brute force army, according to the HTML source code search engine, PublicHTML.
The website of Ecuador’s Association of Private Banks was compromised during this campaign, according to CronUp researcher Germán Fernández. This served as a watering hole for unsuspecting visitors.
Why did the threat actors switch from using crypto wallet drainers to use brute force against other websites? Sucuri believes that the goal is to create a larger portfolio of websites, such as crypto-draining attacks, from which to launch additional attacks on a larger scale.
According to Sucuri researcher Denis Sinegubko,” they most likely realized that at their scale of infection ( 1000 compromised sites ) the crypto drainers are not very profitable yet.”
Additionally, they attract a lot of attention, and their domain names are frequently blocked. Therefore, it seems reasonable to replace the payload with something more shady so that they can also increase their portfolio of compromised websites for upcoming wave of infections that they will be able to monetize in some way or another.











