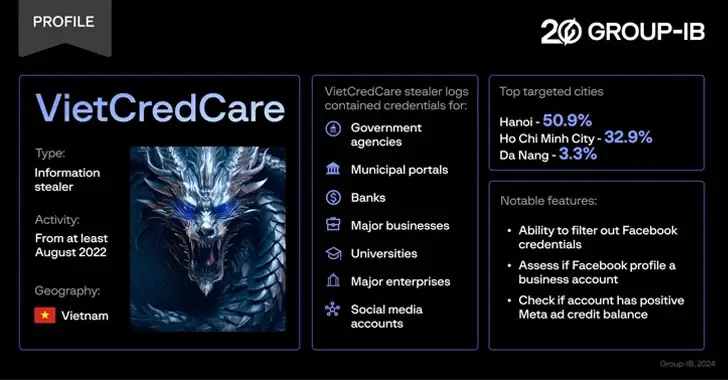
At least since August 2022, VietCredCare, a previously unidentified information stealer, has been targeting Facebook advertisers in Vietnam.
According to a recent report published by Singapore-based Group-IB and distributed to The Hacker News, the malware is “notable for its ability to automatically filter out Facebook session cookies and credentials stolen from compromised devices, and assess whether these accounts manage business profiles.
By focusing on Vietnamese people who manage the Facebook profiles of well-known companies and organizations, the large-scale malware distribution scheme aims to make it easier for corporate Facebook accounts to be taken over.
Threat actors behind the operation then use successfully seized Facebook accounts to post political content or spread phishing and affiliate scams in order to make money.
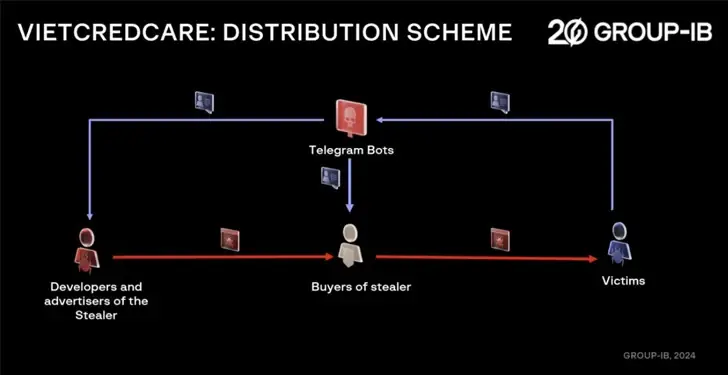
VietCredCare is advertised on Facebook, YouTube, and Telegram and is made available to other aspiring cybercriminals using the stealer-as-sale model. It is thought to be run by people who speak Vietnamese.
Customers can either buy access to a botnet that is being managed by the malware’s creators or download the source code for sale or personal use. To manage the exfiltration and delivery of credentials from an infected device, they are also given a customized Telegram bot.
Links to fake websites on social media posts and instant messaging sites are used to spread the.NET-based malware, which poses as legitimate software like Microsoft Office or Acrobat Reader to trick users into downloading it.
Its ability to extract credentials, cookies, and session IDs from web browsers like Google Chrome, Microsoft Edge, etc., indicating its Vietnamese focus, is one of its main selling points.
In addition to taking steps to avoid detection by turning off the Windows Antimalware Scan Interface ( AMSI) and adding itself to the list of Windows Defender Antivirus ‘ exclusions, it can also find the victim’s IP address, verify whether Facebook is a business profile, and determine whether the account in question is currently managing any ads.
According to Vesta Matveeva, head of the High-Tech Crime Investigation Department for APAC,” VietCredCare’s core functionality to filter out Facebook credentials puts organizations in both the public and private sectors at risk of reputational and financial damages if their sensitive accounts are compromised.”
The stealer malware has stolen credentials from a number of government organizations, universities, e-commerce platforms, banks, and Vietnamese businesses.
In order to target Facebook accounts, the Vietnamese cybercriminal ecosystem gave rise to a long list of stealer malware, including Ducktail and NodeStealer. VietCredCare is the most recent addition to this list.
Having said that, Group-IB informed The Hacker News that there is currently no evidence linking VietCredCare to the other strains.
While there are some similarities between Ducktail and NodeStealer, the latter uses a [command-and-control ] server rather than Telegram, and their choice of victims is different, according to the company.
Threat actors with little to no technical knowledge can enter the cybercrime field thanks to the stealer-as-service business model, which harms more defenseless victims.