A crucial October patched vulnerability for vCenter Server remote code execution has been confirmed by VMware to be active.
Administrators of VMware vSphere environments can manage eX and ESXi servers and virtual machines (VMs) with the aid of the management platform dCenter Server.
In an update to the original advisory this week, the company stated that “VMware has confirmed that exploitation of CVE- 2023-34048 has occurred in the wild.”
The vulnerability, which Trend Micro vulnerability researcher Grigory Dorodnov reported, is brought on by an out-of-bounds write weakness in the implementation of the DCE/RPC protocol by vCenter.
Attackers can use it remotely in low-level attacks with high levels of confidentiality, integrity, and availability impact that do n’t call for user interaction or authentication.  , VMware has also released security patches for a variety of end-of-life products without active support due to its critical nature.
For easy access to corporate networks, network access brokers like to purchase VMware servers and nbsp and then sell them to ransomware gangs on cybercrime forums. Many ransomware organizations, including  , Royal, Black Basta, and LockBit, are now well-known for directly targeting victims ‘ VMware ESXi servers in order to steal and encrypt their files and demand astronomical sums of money.
More than 2, 000 VMware Center servers are currently online, potentially vulnerable to attacks and exposing corporate networks to breach risks due to their vSphere management role, according to Shodan data.
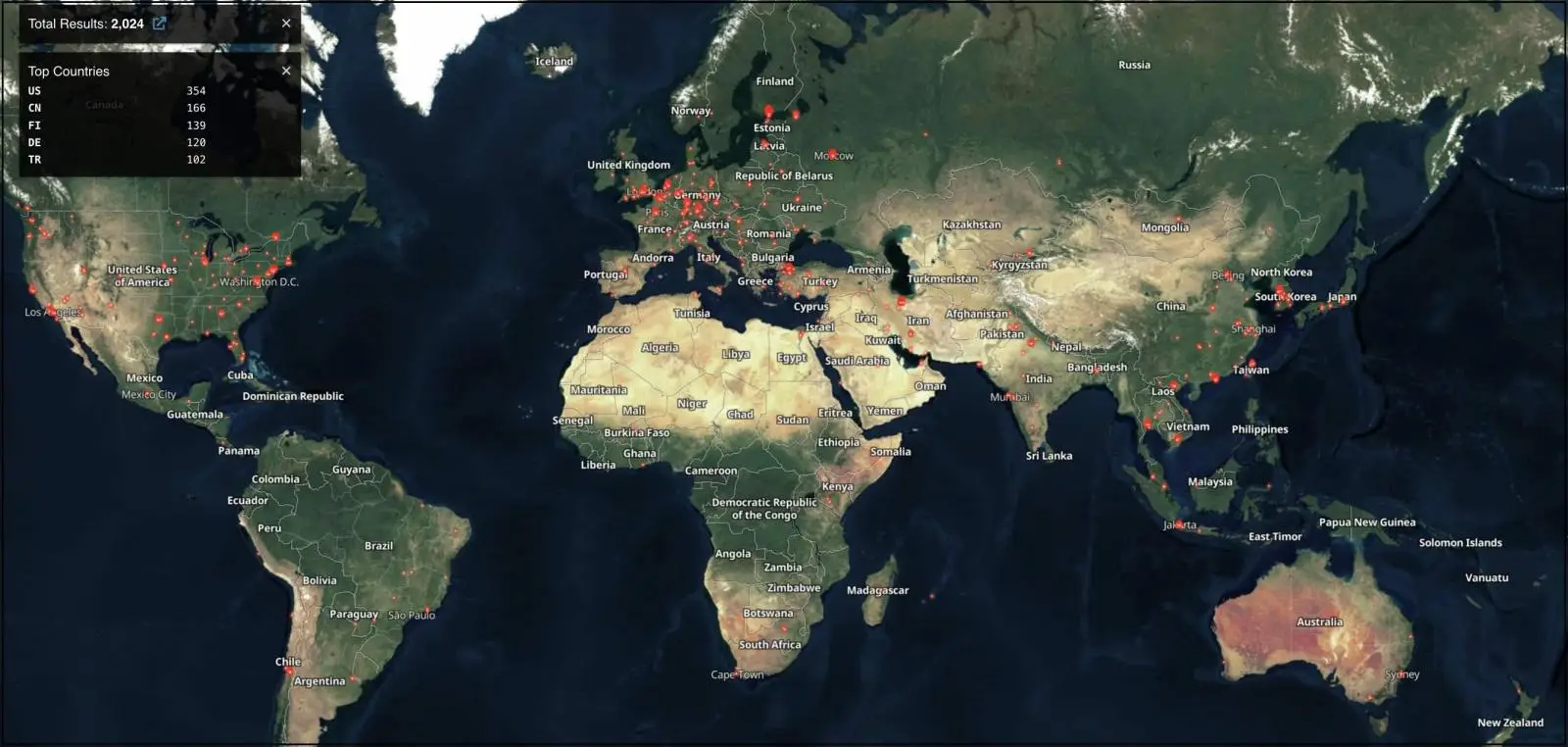
VMware has advised administrators who are unable to patch their servers to strictly restrict network perimeter access to vSphere management components because there is no workaround.
As part of an overall effective security posture, VMware strongly advises strict network perimeter access control to all management components and interfaces in vSphere and related components, such as storage and network components.
2012, 2014, and 2020 are the specific network ports that could be exploited in attacks aimed at this vulnerability.
Multiple severe vCenter Server security flaws that could have resulted in code execution and authentication bypass risks were also fixed by VMware in June.
The company warned customers of another actively exploited critical Aria Operations for Networks flaw and fixed an ESXi zero-day used by Chinese state hackers in data theft attacks that same week.
Since the beginning of the year, IT administrators and security teams have had to deal with alerts of numerous security flaws that are currently being exploited, such as zero-day vulnerabilities that affect Ivanti Connect Secure, Ivani EPMM, and Citrix Netscaler servers.











