Utilizing a deceptive domain that was made available as part of VMware, a new Linux version of the Bifrost remote access trojan (RAT ) employs a number of novel evasion strategies.
One of the longest-running RAT threats  is Bifrost, which was first discovered twenty years ago. It collects sensitive information from the host before infecting users with malicious email attachments or payload-dropping websites.
Researchers from Palo Alto Networks ‘ Unit 42 report finding a spike in Bitfrost activity recently, which led them to investigate a novel, more secretive variant.
New Bitfrost strategies
Unit 42 researchers ‘ analysis of the most recent Bitfrost samples has revealed a number of intriguing additions that increase the malware’s evasion and operational capabilities.
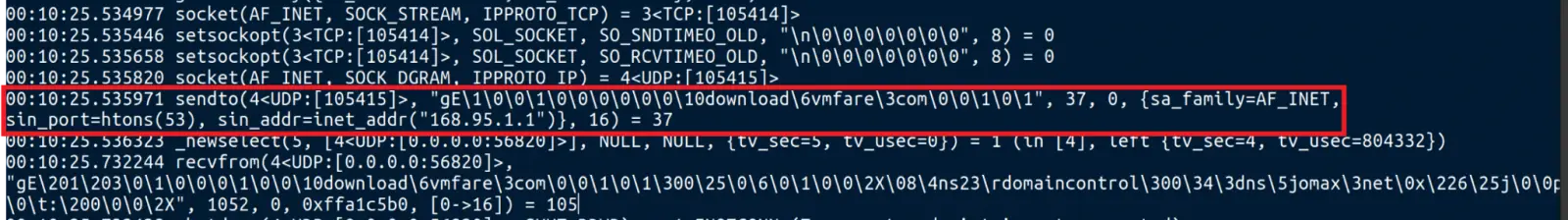
First, the “download” command and control ( C2 ) server that the malware connects to uses it. vmfare [. ] The” com” domain, which appears to be comparable to a legitimate VMware domain, makes it difficult to spot when inspected.
Contacting a Taiwan-based public DNS resolver makes tracing and blocking more difficult.
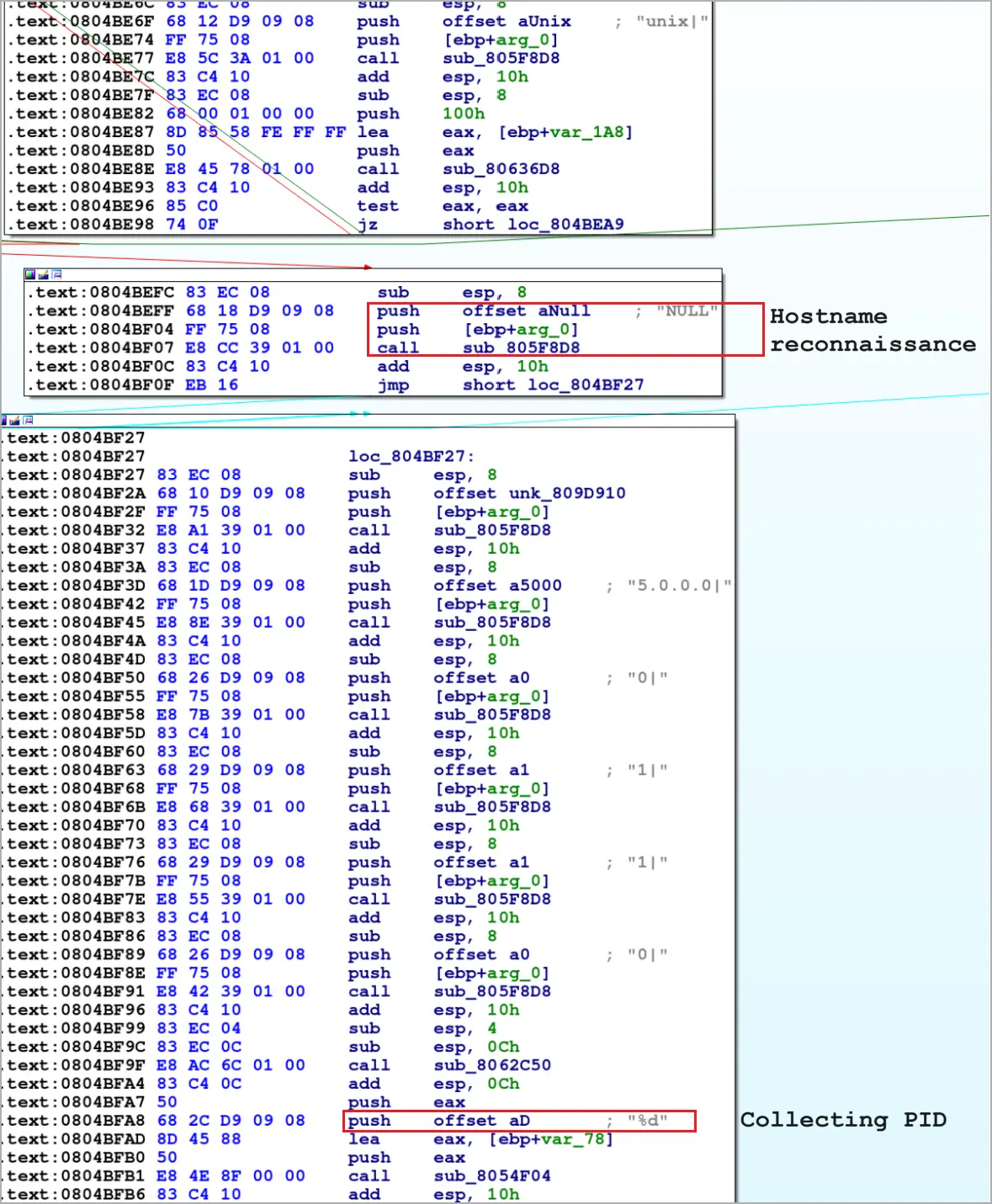
Making its analysis more difficult, the malware’s binary is compiled in stripped form without any debugging data or symbol tables.
The victim’s hostname, IP address, and process IDs are collected by Bitfrost, which then sends it to the C2 via a newly created TCP socket using RC4 encryption to secure it before transmission.
An ARM version of Bitfrost, which has the same functionality as the x86 samples analyzed in Unit 42’s report, is another intriguing finding.
The development of those builds demonstrates that attackers intend to expand their scope of attack to ARM-based architectures, which are increasingly prevalent in various environments.
The findings made by the Unit 42 team call for increased vigilance even though Bitfrost may not rank highly as a highly sophisticated threat or one of the most widely distributed pieces of malware.
It is obvious that the RAT’s creators want to make it a more secretive threat that can target a wider range of system architectures.











