After the Mogilevich extortion group claimed to have breached the company’s servers, Epic Games claimed to have found no proof of a cyberattack or data theft.
Epic Games told BleepingComputer in a statement that” we are investigating but there is no conclusive evidence that these claims are true.”
” Mogilievich has not contacted Epic or provided any evidence of these allegations ‘ truth.”
After seeing a screenshot of the dark web page that promoted the breach, Epic Games attempted to contact the threat actor and immediately began looking into the incident.
The company claimed that they had only received information from a tweet I posted yesterday and that they had never heard back from Mogilevich.
I contacted a Mogilevich extortion group representative yesterday to ask if they would provide proof of the attack after the alleged breach  became widely known on Twitter.
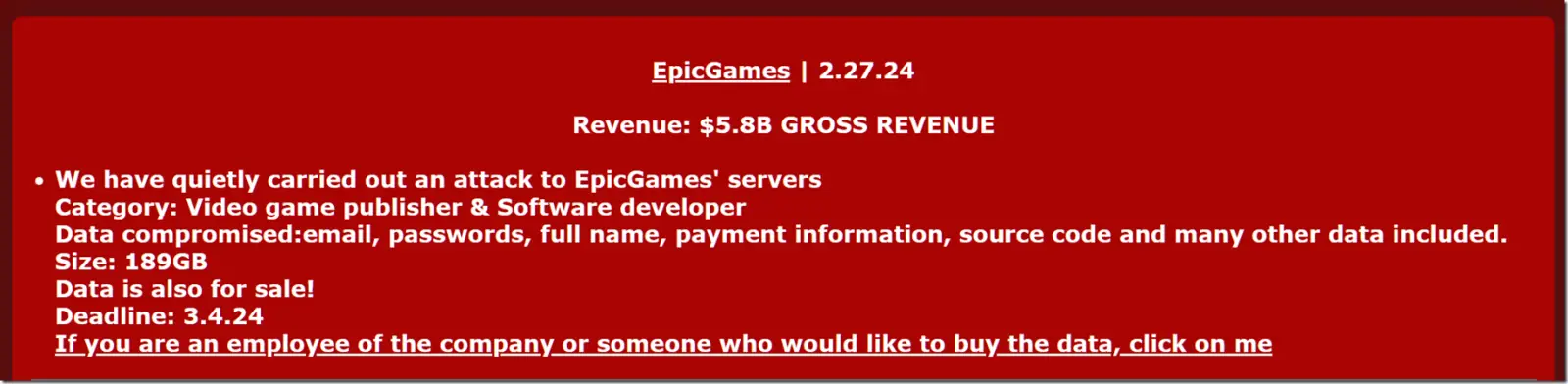
Source: BleepingComputer
The threat actors confirmed to BleepingComputer that they would only sell samples to those who showed “proof of funds,” meaning they could demonstrate that they had the available cryptocurrency assets to make the purchase. They later told BleepingComputer that they were selling the stolen data for$ 15,000.
They asserted that three people who provided proof of funds received samples of the allegedly stolen data.
Mogilevich, who is he?
Mogilevich, a relatively new extortion group, claims to have hacked into numerous organizations, including Infinity USA and the Irish Department of Foreign Affairs.
Mogilevich, however, only sells directly to proven buyers, unlike other extortion groups.
Numerous security researchers BleepingComputer spoke with believe that the threat actors are attempting to defraud customers with fake data due to this lack of proof.
In exchange for a functioning ransomware encryptor and negotiation panel, the threat actors also claim to be a Ransomware-as-a-Service operation. The affiliate and the operators divide the payment when an affiliate attacks and demands a ransom.
No ransomware encryptor samples have been discovered so far, though, that might explain their association with encryption attacks.











