It’s a thrilling day today. We declared that PingSafe has now been fully acquired by us. I wanted to use this chance to describe our journey forward because PingSafe is a key component of SentinelOne’s cloud security future. I’ll go into more detail about how and why cloud security is frequently the most difficult aspect of business security and needs serious improvement.  ,
As Change, Cloud
By enabling greater scale, speed, and dependability in the creation and deployment of applications and data pipelines, cloud computing and containers have the power to propel business transformation and innovation.
However, using new technologies can also lead to increased attack surface and security issues. Security and innovation are in conflict, and many businesses are currently unable to strike a balance between the two.
A shift by numerous threat actors to the cloud was one of the most intriguing trends in cyberattacks in 2023. Many of their targets are unable to stop and detect threat activity in their cloud environments, which contributes to this pivot.
Customized cloud attack techniques to enable ransomware deployments were among the high-profile breaches from the previous year. Notably, Roasted 0ktapus ( also known as Scattered Spider ) attacked cloud environments with sophisticated discovery, lateral movement, persistence, and defense evasion.
Threat actors are altering and disabling cloud services and identities in their attacks in addition to targeting cloud infrastructure.
Additionally, cloud breach automation is increasing, which speeds up compromise. Automated scripts have been found even in widely accessible open-source tools like AlienFox ( which SentinelOne Labs reported on here ) and Androxgh0st ( for which the FBI and CISA recently released a TLP: Clear Advisory ). In these two cases, the manipulation of cloud service provider email services as well as persistence and privilege escalation within cloud identity.
A shift toward cloud security is required as a result of these changes in how threat actors approach cloud environments. misconfigurations in the cloud, for instance. There has been a proper focus on identifying, evaluating, and fixing cloud misconfigurations in light of Gartner’s warning that by 2025, 91 % of cloud breaches will result from preventable human error.
Although Well Architected Frameworks from cloud service providers have been invaluable and cloud security practitioners have benefited greatly from Cloud Security Posture Management ( CSPM) capabilities, comparing constantly shifting deployment realities to compliance standards continues to be a noisy process with little prioritization.
Alerts like excessive and changing permissions in Azure AD or AWS IAM may now be compromise artifacts within a larger attack chain because threat actors are now known to be the ones responsible for misconfigurations. Threat actor actions can now be used to infer malicious activity that has already been carried out, necessitating the inclusion of misconfigurations as compromise artifacts.
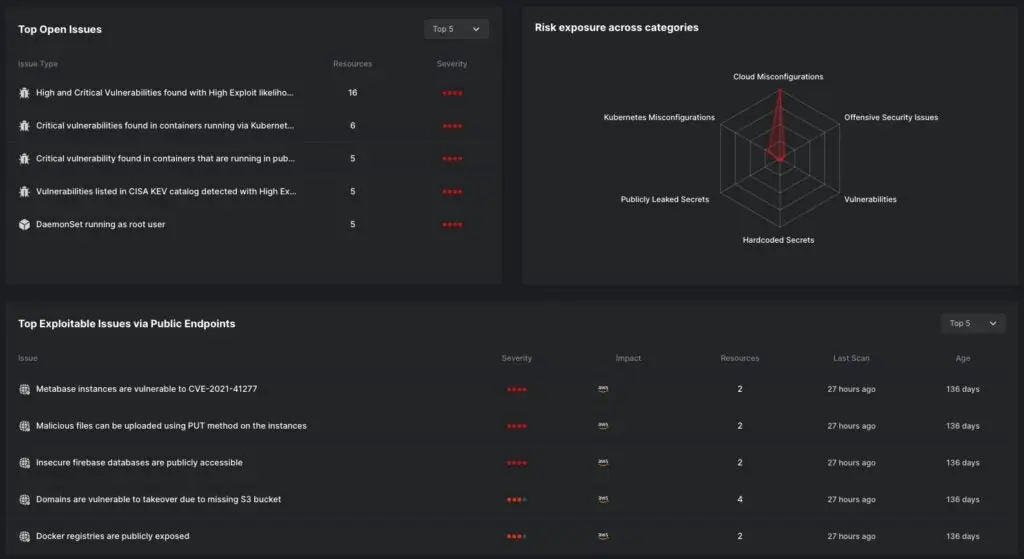
To determine when misconfigurations might be malicious activity, security operations center analysts may now need to collaborate with cloud security and infrastructure teams. We should n’t overlook the fact that the use of open-source components poses growing supply chain risk threats within the build pipeline prior to the deployment of cloud environments into production. Recently, ReversingLabs ‘ team members put together some top-notch reporting on trends in this industry.
When considered collectively, it is evident that the infrastructure and development teams responsible for maintaining the cloud’s security can benefit from improvements to the current cloud security tooling.
The three realities of cloud security for the present and the future
Three realities quickly become apparent as we consider what customers need now and will need in the future. The first reality is that businesses need security and visibility controls for everything in their environments, including cloud infrastructure, identity and endpoints, deployment services, and build pipelines.
In order to make security innovation where it needs to be, security data must be closely correlated across these environments, so it is ideal that these capabilities are offered by a single platform. This is true not only for convenience and the advantages of using fewer vendors.
The second reality is that security cannot be made up entirely of visibility, despite how important it is. The ability to block at machine speed and respond is a necessary component of effective cloud security. This calls for a defense mechanism that combines an agent’s ability to stop and conduct forensics with the speed and breadth of agentless security.
Thirdly, it is crucial to realize that maintaining security must be done sustainably. Noise is neither necessary nor time-consuming. Cloud security insights must be prioritized, actionable, and false-positive free due to a lack of resources and ongoing time constraints. Security professionals also need AI support to speed up their workflows. Our goal is to provide a single platform that is purpose-built to empower users and provide visibility, protection, response, and remediation capabilities through the cloud lifecycle in real time. This is our main goal in developing e-commerce’s modern, all-encompassing approach to cloud security.
In order to achieve this, we are combining our current agent-based Cloud Workload Security ( also known as CWPP ) and Cloud Data Security threat protection products with our new PingSafe acquisition capabilities, which will now be referred to as Cloud Native Security.
They make up our all-inclusive CNAPP when combined.
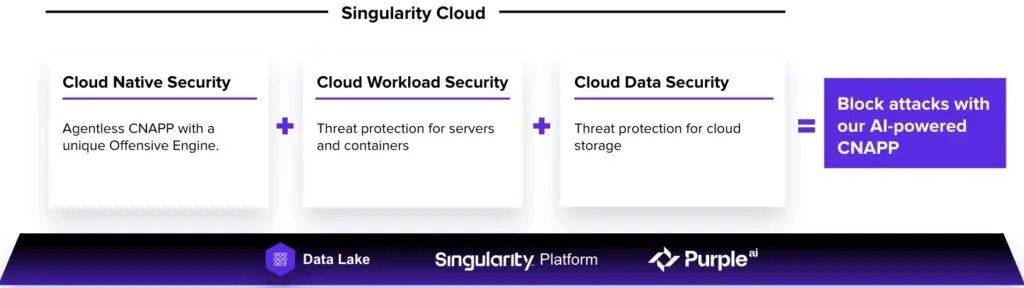
We’ll rely on Gartner for the required definition following a potential new acronym:
It is important to use a framework of the four guiding principles that underpin our comprehensive CNAPP in order to comprehend its results:
Visibility throughout the entire environment
You need visibility before anything can be accomplished. You cannot protect what you cannot see, as the saying goes. Security teams can manage cloud sprawl with SentinelOne’s integrated endpoint and identity, agentless visibility, and quick deployment.
Many attacks begin at the endpoint, escalate privileges through identity-related attacks, and then spread to the cloud. With an asset inventory that includes mapped resource relationships, our customers instantly gain centralized visibility and discovery across multiple clouds.
Security can now assess the state of container images, Infrastructure as Code ( IaC ) templates, Kubernetes clusters, and various cloud services thanks to views into areas typically reserved for development and infrastructure teams. Security teams will be able to find unmanaged instances and report on misconfigurations, secrets, and malware thanks to this.
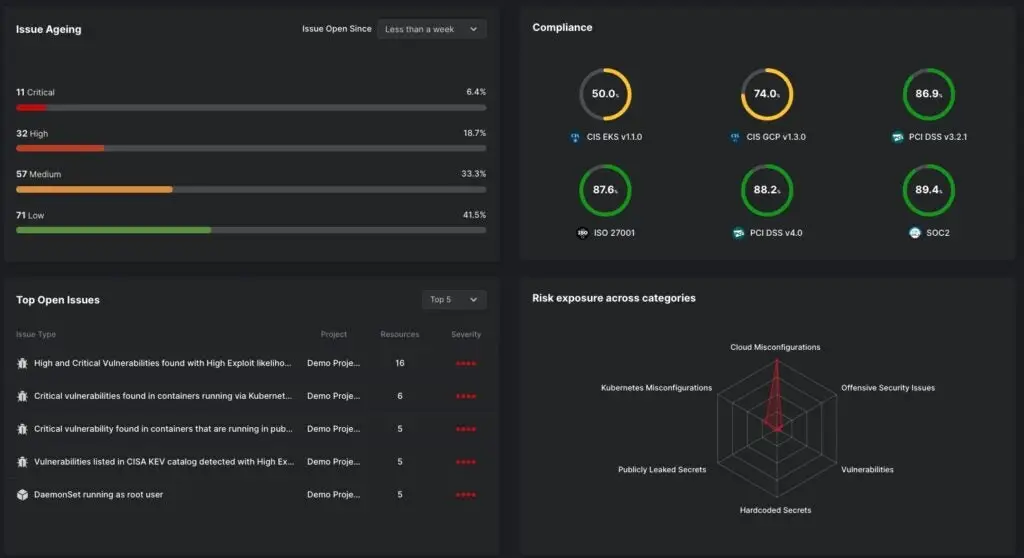
To ensure that security can be incorporated into the build process, in a shift-left style, and across important production environments, visibility through the cloud lifecycle is crucial.
However, SentinelOne’s all-inclusive CNAPP takes things a step further by enabling users to respond left as well as shift left using IaC template scanning and our collaboration with Snyk. This is the capacity of a security team to collaborate with infrastructure and development teams to apply post-incident insights.
To completely reduce the likelihood of re-infection at the root cause, remediation and response should include turning back to the build pipeline.
By defending from an attacker’s perspective, action is what matters.
Unfortunately, noise has become a key component of cloud security tooling. While important, a focus on compliance and best practices prevents many security teams from distinguishing between weaknesses that have the potential to be exploited and those that are misunderstood or vulnerable.
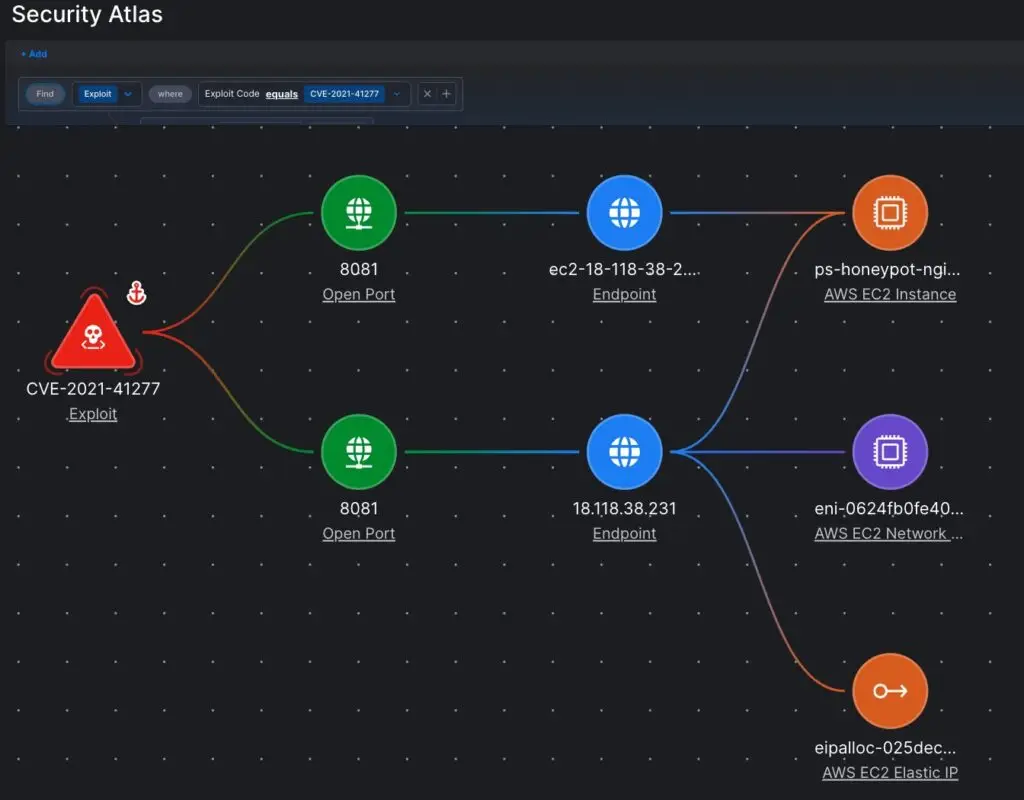
The incorporation of an automated attacker’s perspective in SentinelOne CNAPP is a ground-breaking strategy for piercing this noise. Our offensive security engine validates the viability of your cloud environment by safely simulating attacker methods.
This false-positive, evidence-based reporting of Exploit Paths immediately identifies the most important risks that need immediate attention. What distinguishes a theoretical CVE list of” Where do I begin with all these areas I need to fix” from this one? There is also a significant improvement in risk management, as well as” What needs to be fixed now.”
Changing from detection to protection
Visibility alone is obviously insufficient in a world of sophisticated threats and condensed time frames for breach. SentinelOne can combine our in-depth understanding of cloud threats with strong runtime protection by fusing agent and agentless capabilities. By preventing threats at machine speed, this enables sophisticated cloud detection and response, which includes protection.
SentinelOne identifies and kills malicious processes and quarantines files as they run in response, as opposed to relying on time-consuming human intervention or self-created automated workflows with a limited scope.
This enables security teams to use SentinelOne to carry out corrective actions and enter the incident’s remediation phase more quickly and effectively.
being driven by AI
Today, AI is present everywhere, but it is not perfect. While adding AI and automation to a single platform will produce quicker, better results than layering AI on top of legacy, siloed tooling. Nobody wants 14 consoles with alert queues, 3 query languages, or 68 agents.
When we refer to” ONE agent and ONE platform,” we really do mean it because the Singularity Platform is the AI-infused foundation that supports and unifies all of our security solutions. You will receive a portfolio from many vendors, and we will deliver the platform.
Since our cloud security solutions are based on a single platform, we can track and stop malicious activity in the Singularity Data Lake using our AI security analyst PurpleAI.
What Now Takes Place?
We are moving quickly to incorporate the following capabilities into our platform now that the PingSafe acquisition has been completed:
- Automated misconfiguration detection and compliance with industry standards like NIST, MITRE, CIS, PCI-DSS, and more with cloud security posture management ( CSPM).
- Without the use of an agent, you can find vulnerabilities throughout your entire cloud infrastructure using agentless vulnerability scanning.
- Infrastructure as Code ( IaC ) Scanning: Shift left to look for problems with container configuration files and IAC templates before production.
- Secure containers from code to runtime using Kubernetes Security Posture Management ( KSPM).
- Cloud credential leakage in public repositories can be found and avoided using secret scanning.
- Offensive Security Engine: Prioritize those problems with breach potential assessments, verify actual exploit paths, and simulate attacks using an attacker’s mindset.
As we start the global rollout phases, we anticipate launching Cloud Native Security in the middle of 2024. Customers will be able to use the current PingSafe solution right away.
Contact us or request a free demo to learn more about how Cloud Native Security offers quick visibility, prioritized false-positive free, evidence-based reporting, and actionable insights, or to make sure your critical cloud workloads are protected with machine speed protection with our Cloud Workload Security.











