Concerns about the flaws in significant SaaS platforms were raised by the Midnight Blizzard and Cloudflare-Atasian cybersecurity incidents. These incidents serve as an example of the dangers associated with SaaS breaches; it is crucial but difficult to protect the security of sensitive data and apps. The complex security challenges facing IT systems are illustrated by common threat vectors like sophisticated spear-phishing, misconfigurations, and vulnerabilities in third-party app integrations.
Password spraying against a test environment served as the initial attack vector for Midnight Blizzard. Threat actors for Cloudflare- Atlassian used compromised OAuth tokens from a previous SaaS identity security provider breach at Okta to launch the attack.
What ExactlyOccurred?
Breach of the Microsoft Midnight Blizzard
The Russian” Midnight Blizzard” hackers—also known as Nobelium, APT29, or Cozy Bear—and the SVR, the Kremlin’s foreign intelligence service unit, targeted Microsoft.
Threat actors in the Microsoft breach include:
- used a password spray technique on old test accounts and legacy accounts without multi-factor authentication ( MFA ) enabled. Based on the number of failures, Microsoft claims that the threat actors” [used ] few attempts to avoid detection and account blocks.”
- hijacked a legacy test OAuth app after using the compromised legacy account as the point of entry. High-level permissions were granted for this legacy OAuth app to access Microsoft’s corporate setting.
- exploiting the permissions of the legacy OAuth app to create malicious apps. Threat actors could keep using the applications even if they lost access to the account that was initially compromised because they controlled the legacy OAuth app.
- granted themselves admin Exchange permissions and credentials.
- granted control over a new user by escalating privileges from OAuth.
- Using their newly created user account, they consented to malicious OAuth applications.
- By giving the legacy application complete access to M365 Exchange Online mailboxes, it further escalated its access. With this permission, Midnight Blizzard was able to access corporate emails and attachments as well as senior staff members’ M365 email accounts.
Atlassian Breach’s Cloudflare
A nation-state attack also compromised Cloudflare’s Atlassian systems on Thanksgiving Day, November 23, 2023.
- The use of compromised credentials that had not been changed after a previous breach at Okta in October 2023 allowed for this breach, which began on November 15, 20, to occur.
- Attackers were able to view 120 code repositories in Cloudflare’s Atlassian instance by accessing the internal wiki and bug database.
- Potentially exfiltrated were 76 source code repositories for important operational technologies.
- On November 23, Cloudflare discovered the threat actor after he connected an Atlassian admin group to a Smartsheet service account.
Can third-party apps be monitored by your security team? 60 % of teams are unable to
Consider your SaaS security to be excellent. 79 % of the 600 global security professionals polled by Appomni shared this sentiment despite having to deal with cybersecurity incidents. Explore the AppOmni 2023 Report’s insights.
Threat actors are targeting SaaS more frequently.
These espionage and intelligence gathering-related attacks on SaaS service providers are part of a larger pattern of nation-state actors. Prior to the 2021 SolarWinds attack, Midnight Blizzard was involved in significant cyber operations.
These incidents highlight the significance of keeping an eye on your SaaS environments at all times and the ongoing danger that sophisticated cyberattackers pose to operational tech stack and critical infrastructure. They also draw attention to important SaaS identity management vulnerabilities and the need for strict third-party app risk management procedures.
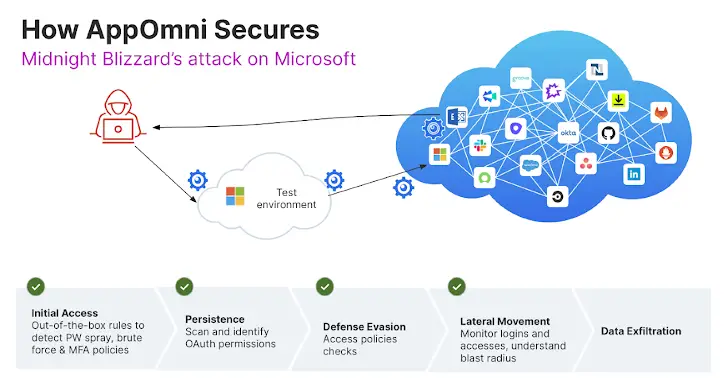
The following kill chain is used by attackers to breach SaaS providers using common strategies, techniques, and procedures ( TTPs ):
- Password spray and hijacking OAuth are used as initial access.
- Persistence: Creates additional OAuth while posing as admin.
- Defense evasion: No MFA, highly privileged OAuth
- Broader compromise of connected apps in lateral movement
- Extract sensitive and privileged data from apps using data exfiltration.
The SaaS Kill Chain: Broken
Continuous monitoring, granular policy enforcement, and proactive lifecycle management over your SaaS environments are all effective ways to stop the kill chain early. AppOmni, a SaaS Security Posture Management ( SSPM) platform, can assist in identifying and alerting on:
- Initial Access: Unenforced MFA policies, brute force attacks, and password spraying are all examples of out-of-the-box methods to spot credential compromise.
- Persistence: Check for OAuth permissions, find any hijacking, and find out.
- Defense Evasion: Access policy checks, permission changes, and the creation of new identity providers ( IdPs ).
- Lateral Movement: Keep an eye on logins and privileged access, spot toxic combinations, and comprehend an account’s blast radius.
Note: Beverly Nevalga of AppOmni is the author of this expertly contributed article.