The cybersecurity challenges we face are becoming more apparent to small to medium businesses, the general public, and large businesses that have developed security capabilities over time as breaches make the headlines almost weekly. SMBs frequently find themselves without access to security tooling that is both simple for them to use and affordable, despite the fact that this is increasing awareness among smaller businesses of the need to improve their security posture.
The development of threat intelligence, which is required to comprehend and identify the threats being faced, as well as the tools used to provide protection, must be prioritized when thinking about the requirements of SMBs. With more than 20 years of experience, NTTSH has developed capabilities and products that use threat intelligence to protect customers as well as research and curation of that intelligence. NTTSH is moving to democratize cybersecurity and give smaller businesses the protection they need after years of concentrating on larger enterprises.
Center for Global Threat Intelligence
All of NTTSH’s efforts are underpinned by the capabilities of its Center for Global Threat Intelligence (GTIC). The efforts of the GTIC go beyond those of a pure research organization by taking threat research and combining it with NTTSH proprietary detective technology to produce applied threat intelligence.
The GTIC’s goal is to safeguard clients by offering cutting-edge security intelligence and threat research, making it possible for NTTSH to guard against online threats. GTIC uses proprietary intelligence capabilities and NTT’s position as the operator of one of the top 5 tier 1 Internet backbones to offer an unmatched view of Internet telemetry to understand and gain insight into the various threat actors, exploit tools and malware- and the tactics, techniques, and procedures used by attackers. GTIC maintains connections with other major players in this industry, such as the Cyber Threat Alliance, Microsoft, CISA, and the National Cyber Forensics and Training Alliance (NCFTA ), in addition to curating its own threat intelligence research.
The annual Global Threat Intelligence Report ( GTIR ) from NTTSH offers a glimpse into the work being done by GTIC, summarizing the major security landscape challenges facing organizations of all sizes and offering useful insights to aid organizations in better adjusting to the changing threat landscape. Key industry verticals were given special attention in the Q3 update of the 2023 GTIR, which sheds light on the dangers they face.
Sector-specific threat
In a world where many providers, especially smaller ones, are unaware of cybersecurity and lack the resources to deploy and maintain the kinds of controls enjoyed by large enterprises, the healthcare sector is facing an unusual set of challenges in addition to the high value of the information owned by healthcare providers. Still proving to be particularly problematic is ransomware. The USA, Australia, and the UK account for nearly 80 % of healthcare ransomware breaches, which are proving to be particularly concentrated in a few geographic areas.
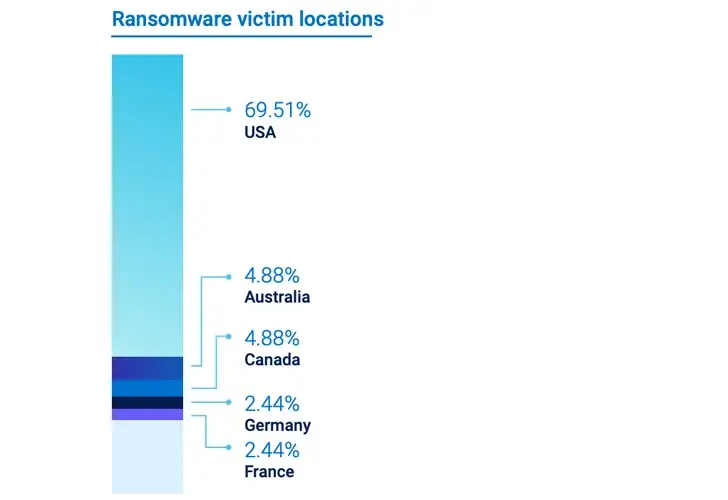 |
| Locations of ransomware victims in the healthcare industry are shown in Figure 1. |
Similar geographic trends can be seen in the telecommunications industry, where USA, UK, and Australia account for about 52 % of ransomware attacks and 83 % of those attacks occur in education.
Lockbit 3.0 continues to be the most active ransomware threat actor across all focus sectors. However, some ransomware actors are concentrating on particular industries, such as education, which is the focus of the Bl00dy ransomeware gang.
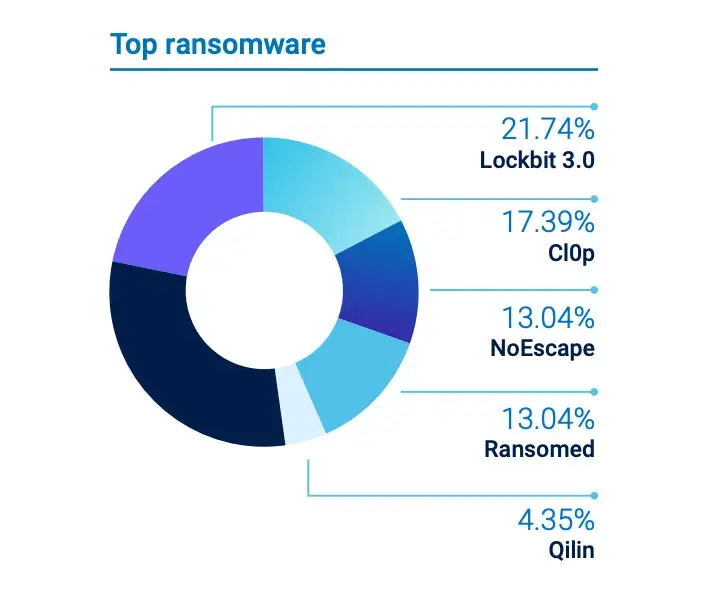 |
| Top telecommunications industry ransomware actors are shown in Figure2. |
SaaS Security Issues
The way that the rapidly accelerating adoption of SaaS is posing its own set of challenges has recently been a focus for GTIC. Small and large businesses are both rapidly integrating SaaS into their day-to-day operations, and it is anticipated that annual growth will remain close to 20 % through 2027. It is crucial to remember that, according to Gartner, 99 % of cloud security breaches are anticipated to be the fault of the customer.
Larger businesses have been familiar with the shared responsibility model for cloud services for some time. However, smaller organizations are still adjusting to this model. This means that in terms of SaaS, SMBs are still adjusting to the fact that they still have control over their data and, more importantly, manage their accounts and identities, even though the cloud provider is in charge of the application. Threat actors are therefore concentrating on identity compromise strategies, particularly phishing and credential stuffing.
overcoming the difficulties of hybrid IT
SMBs used to be able to protect the technology assets on their premises with antivirus software and firewalls, but as they increasingly rely on cloud-based services, the majority have moved into the hybrid IT space. Although the majority of cloud services offer good security controls, SMBs encounter a number of difficulties when utilizing the security features that are offered.
The number of security alerting sources increases as the attack surface of even smaller businesses grows. Threat actors frequently do n’t limit their activities to a single area of your technology estate, so that’s not the only problem. By compromising one or more endpoints ( like laptops ), for example, they may begin in one area before moving laterally, such as to compromise a SaaS application, using the data they collect ( such as credentials ). SMBs lack the funds for this kind of investment, whereas large businesses have spent the last ten years or more creating specialized SecOps teams and complex security toolchains.
Using XDR to democratize security operations
A single tool that can analyze all of an organization’s telemetry, use threat intelligence, and then offer a straightforward interface that serves as ohm, pane of glass for managing alerting, carrying out investigations and responding to threats is what SMBs need to be able to do. In this situation, XDR offers an affordable solution that combines the essential elements of a conventional SecOps toolchain into one cloud-hosted application. By concentrating the development of its Samurai XDR product on the requirements and budgets of SMBs while still providing the functionality that large enterprises have grown accustomed to, NTTSH has focused its attention in this second crucial area. Samurai XDR makes GTIC’s work accessible and actionable even for organizations without dedicated SecOps resources, despite the fact that its research offers the intelligence required to comprehend and identify the threats facing contemporary organizations. It’s important to keep in mind that while threat intelligence is necessary for threat detection, every organization also needs tools to use it.
a quick trip through XDR Samurai
Samurai XDR was created from the beginning to be user-friendly and, most importantly, accessible to all IT staff members, not just security analysts. The alerts dashboard in Samurai XDR serves as the foundation for all workflows. Security alerts that have been prioritized based on severity and confidence are displayed in this area by the system.
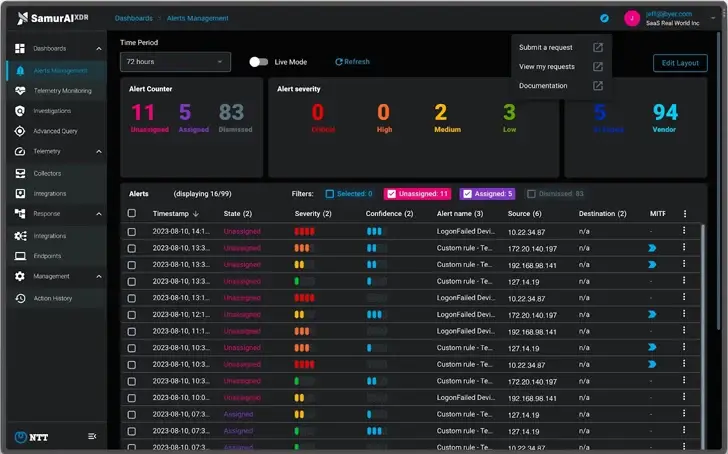 |
| Samurai XDR Alerts Dashboard, Figure3. |
With a focus on offering an easy-to-use interface that can be used by the majority of IT staff, not just by specialized security analysts, the alerts dashboard aggregates notifications from all of the organizations ‘ technologies into one prioritized view.
The Investigations view offers a similarly straightforward and user-friendly interface for managing the lifecycle of an investigation into potential security incidents once the user has determined that an alert warrants further investigation.
Events and alerts are saved in the data lake of the Samurai XDR after processing them. Users can query and analyze all of the events recorded in Samurai XDR, dating back up to a full year, using the data lake. This enables Samurai XDR users to conduct in-depth analyses of historical events for any indications of threats that may have been present for longer periods of time. This allows for the interrogation of a full year’s historical data for purposes like threat hunting. The Advanced Query feature on Samurai XDR, which enables users to search the data lake graphically and using Microsoft’s KQL, makes it possible to query the events in the lake.
Integrations
Integrations give Samurai XDR the ability to receive telemetry ( such as logs ) from your IT infrastructure and applications. In order to mimic the hybrid IT environment that has become standard for even the majority of SMBs today, NTTSH has concentrated on combining the appropriate set of capabilities to ingest telemetry from both on-premises infrastructure and cloud services. Examples of integrations that are currently offered include:
- Azure Management Plan, Microsoft 365, Google Workspace, and other cloud services are all on the way.
- Microsoft Defender for Endpoint, VMware Carbon Black, and Crowdstrike Falcon Insight are used for endpoint detection and response.
- Cisco Secure Firewall ( ASA and Firepower Threat Defense ), Fortinet Fortigate, and Palo Alto Networks NGFW are examples of next-generation firewalls.
Meraki, Bitdefender, Sophos, Zoom, MalwareBytes, OneLogin, OKTA, Zscaler, AWS, and many more integrations will all be added by NTTSH over the upcoming months.
easing the process
Making the Samurai XDR simple to use and affordable has been a major focus for NTTSH in the development of the product. Simple “point and click” workflows, for instance, support the configuration of integrations. All that is required for infrastructure that sends logs via syslog is to point the log source to Samurai XDR’s secure re-clerator, which will then identify the type of log-sending device. Naturally, cloud integrations operate in a similar manner. Samurai XDR minimizes the number of steps and directs users to knowledge-base articles through interactive steps.
Samurai XDR also employs a straightforward pricing structure that is solely based on the customer’s endpoint count, eliminating the need to attempt to estimate the amount of telemetry that will be consumed by the platform. For smaller customers, there is a Starter Pack for up to 25 endpoints that costs$ 750 per year and standard pricing for 50 or more ends per month is only$ 3.33.
Samurai XDR is being offered to all new customers for a free 30-day trial by NTTSH, allowing even the smallest SMBs to test out all of its features without making any commitments. This makes it simple for them to develop an advanced SecOps capability.











