Windows Defender Exploit Guard
Since our last article on EMET’s future and how it relates to Windows 10 in November 2016 ( see Moving Beyond Emmet ), we have gotten a ton of incredibly helpful feedback from fans and users of the platform about when it will finally come to an end. We are excited to announce significant new exploit protection and threat mitigation improvements for the Windows 10 Fall Creators Update based on that feedback!
Our journey to integrate all of EMET’s security advantages directly into Windows will be completed by the release of Windows Defender Exploit Guard ( WDEG). Customer support calls, conversations with EMET stakeholders and security enthusiasts, and the two insights that surfaced most frequently in our survey data had a significant impact on this effort.
Our customers have stated that they want two things more than anything else: a user-friendly UI for setting mitigation settings, and the ability to protect their older Windows 10 apps.
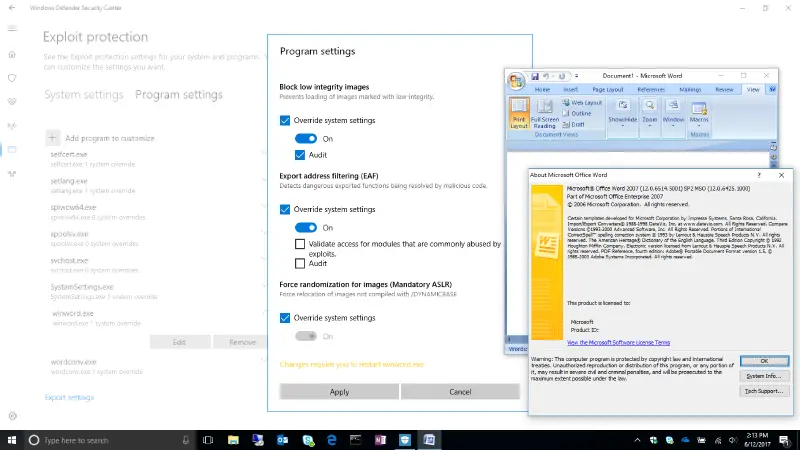
As a result, the Windows Defender Security Center ( WDSC ) can now audit, configure, and manage Windows system and application exploit mitigations. These settings can be used without the need to install Windows Defender Antivirus or any other additional software, and every Windows 10 computer running the Fall Creators Update will have WDEG installed. Following these straightforward instructions, Windows Insiders can begin using WDEG today:
- Search for Windows Defender Security Center using the Start menu or by right-clicking the WDSC icon in the taskbar notification area.
- Click App &, browser control, from the Windows Defender Security Center.
- To access the Exploit protection settings, scroll to the bottom of the resulting screen.
In order to achieve parity between Windows 10 mitigation support and all of the mitigation features offered by EMET, we added the same legacy app protections to WDSC in addition to the new user-friendly interface.
We understand that many businesses rely on legacy apps to run their operations, many of which may never be recompiled with CFG, even though we strongly advise using Control Flow Guard ( CFG ) to offer the strongest protections available.
By setting control flow protections for legacy apps that are similar to those provided by EMET but built-in directly to Windows 10 as part of WDEG, these users can now use Exploit Guard to help secure such apps on modern systems. The following are some of these antiquated app control flow protections:
- Export Address Filtering ( EAF )
- IAF ( Import Address Filtering )
- Validate the CallerCheck API Invocation.
- Execution simulation (SimExec)
- Stack Integrity ( StackPivot )Validation
Our customers frequently requested auditing support as well. We have added audit mode support for both EMET legacy app mitigations and already-existing native Windows mitigation options in order to make it simple to deploy and use mitigation tools without having to deal with application compatibility side effects.
We are aware that many EMET customers altered the policy to meet their unique business needs, despite the fact that it came with a set of suggested configuration settings.
We’ve added a new PowerShell module that transforms EMET XML settings files into Windows 10 mitigation policies for WDEG to make the transition to Windows Defender Exploit Guard easier. The section Understanding Windows 10 in relation to the Enhanced Mitigation Experience Toolkit contains more details about this PowerShell module as well as how EMET features relate to security features in Windows 10.
Last but not least, Windows Defender Exploit Guard includes much more than just the EMET-integrated features. In a subsequent blog post, we’ll talk about host intrusion prevention features and other WDEG elements.
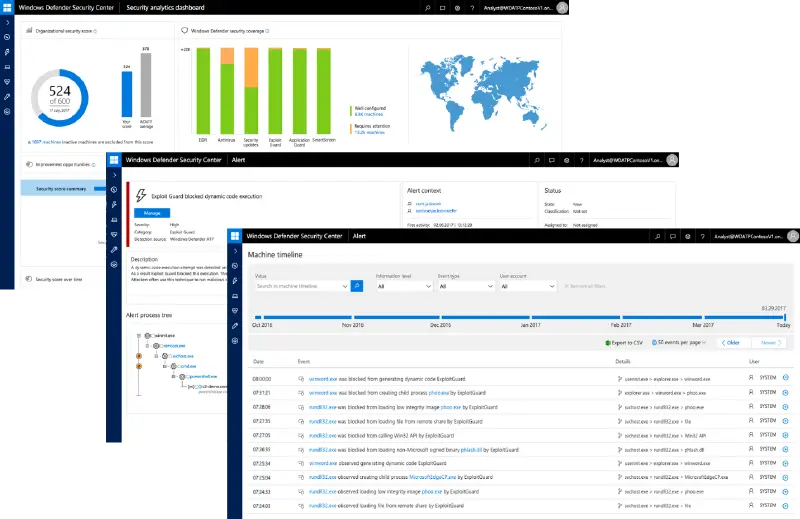
In terms of upcoming features, WDEG will soon be fully integrated with Windows Defender ATP ( WDATP ) to offer a single-pane-of-glass view of the entire Windows security stack. WDATP will record violations of pre-programmed mitigations and use them as additional cues for more sophisticated exploit detection.
Please refer to our Microsoft Docs documentation on Windows 10 Threat Mitigations for more information on the threat mitigations for Windows 10.
OS Security, Nate Nunez
Reducing hardware vulnerabilitiesIvanti Zero-Day Exploits: CISA Issues Emergency Directive to Federal Agencies
Members of the Coast Guard reunite with the Pooch they saved
Akira Ransomware Exploiting Cisco ASA/FTD Vulnerability, CISAWarning