A new tool called” MrAgent” has been developed by the RansomHouse ransomware operation, and it automates the deployment of its data encrypter across numerous VMware ESXi hypervisors.
In December 2021, RansomHouse, a ransomware as-a-service ( RaaS ) operation, debuted. It employs double extortion strategies. The operation created a specific victim extortion page on the dark web in May 2022.
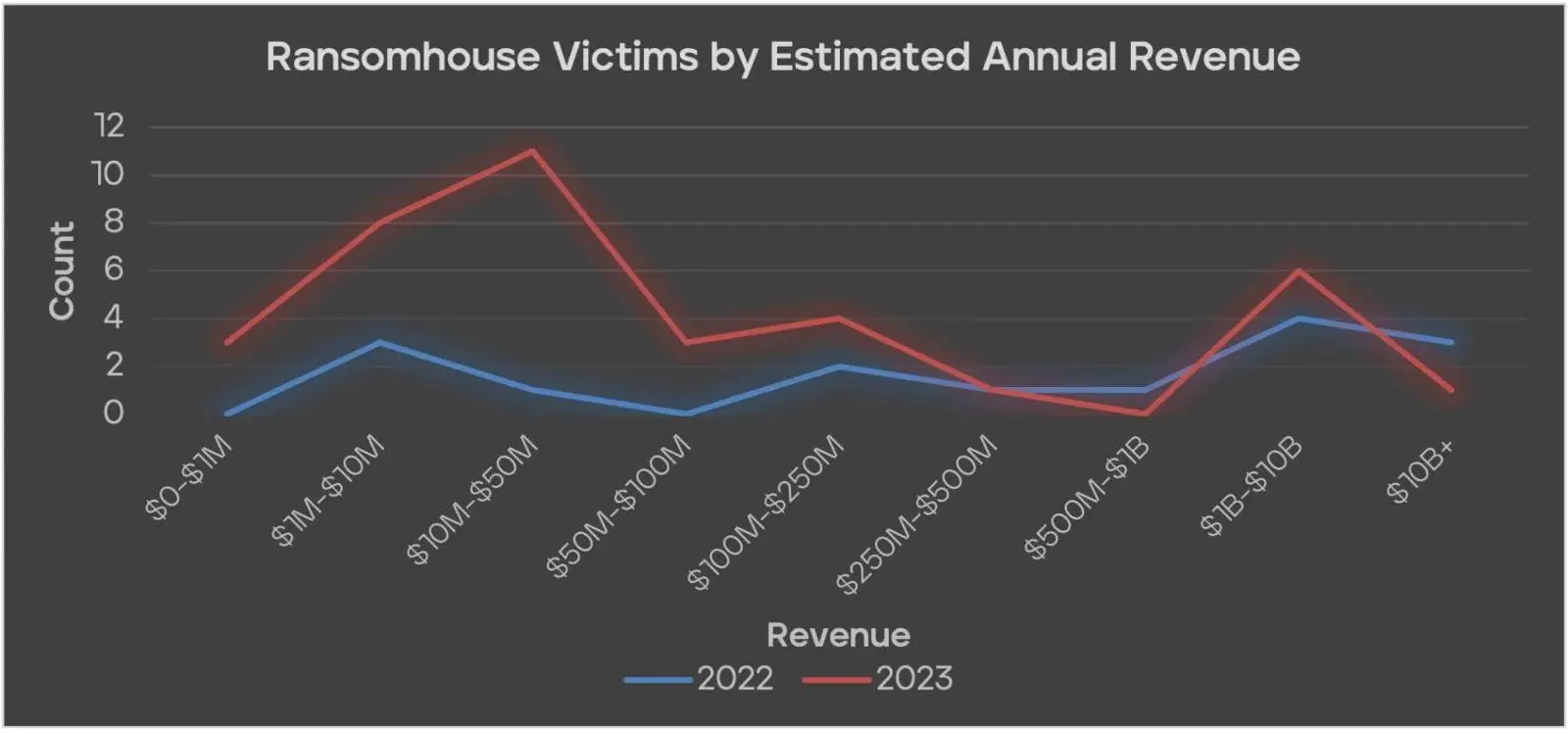
Trellix claims that the , RansomHouse gang, targeted large-scale organizations throughout last year, despite the fact that it was not as active as more notorious groups like LockBit, ALPHV/Blackcat, Play, or Clop.
ESXi vs. Mr. Agent
Because ESXi servers are deployed and used by virtual computers, which frequently contain valuable data that can be used in subsequent extortion processes, ransomware groups target them.
Additionally, ESXi servers frequently host important business applications and services, such as databases and email servers, increasing the ransomware attack’s operational disruption.
A new binary that appears to be designed specifically to thwart gang attacks on ESXi systems has been discovered by Trellix analysts. It is being used in RansomHouse attacks.
The main goal of MrAgent is to identify the host system, disable the firewall, and simultaneously automate the deployment of ransomware across various hypervisors, endangering all managed virtual machines (VMs).
Custom configurations for deploying ransomware directly from the command-and-control ( C2 ) server are supported by the tool.
These configurations include changing the welcome message shown on the hypervisor’s monitor ( to show a ransom notice ), configuring the encrypter command and its arguments, and scheduling an encryption event.
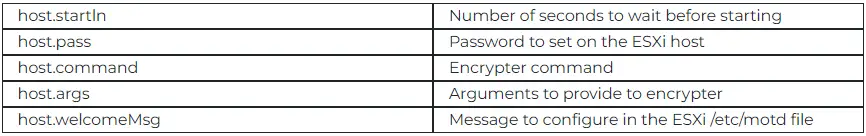
To remove files, end active SSH sessions to avoid interference during the encryption process, and send back information about the running VMs, MrAgent can also run local commands on the hypervisor that the C2 has received.
MrAgent reduces the likelihood of administrator detection and intervention by turning off the firewall and possibly dropping non-root SSH sessions, while simultaneously increasing the attack’s impact by simultaneously targeting all reachableVMs.
According to Trellix, it has discovered a Windows version of MrAgent that still offers the same core features but includes OS-specific modifications like the ability to use PowerShell for specific tasks.
When the target uses both Windows and Linux systems, using the , MrAgent tool across various platforms demonstrates RansomHouse’s desire to broaden its applicability and increase the effectiveness of its campaigns.
According to the report by Trellix,” the attempts to ( further ) automate the steps that are typically carried out manually demonstrate the attacking affiliate’s interest and willingness to target large networks.”
To protect against such threats, defenders must put in place thorough and robust security measures, such as regular software updates, robust access controls, network monitoring, and logging.











