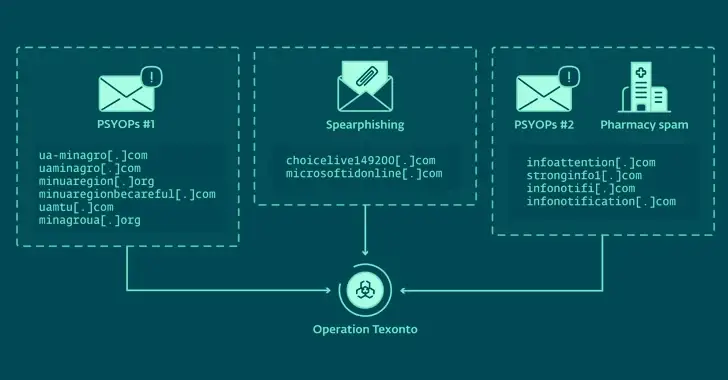
A new influence operation that uses spam emails to spread war-related misinformation has been discovered by cybersecurity researchers and is aimed at Ukraine.
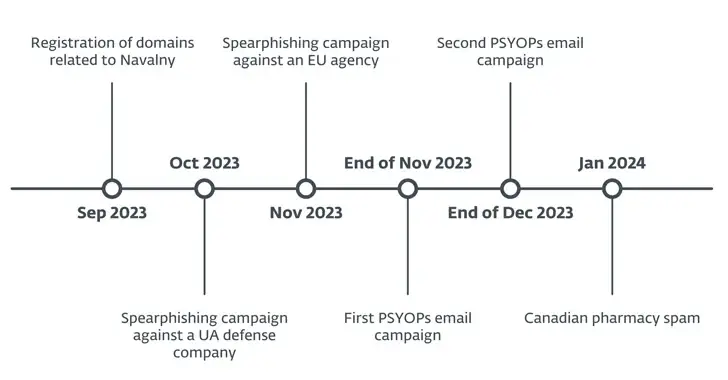
The Slovak cybersecurity company ESET, which also identified a spear-phishing campaign in October 2023 and another European Union agency in November 20, with the goal of obtaining Microsoft login credentials using fictitious landing pages, has linked the activity to Russia-aligned threat actors.
Although some aspects of Operation Texonto, particularly the spear-phishing attacks, overlap with COLDRIVER, which has a history of obtaining credentials through phony sign-in pages, the entire campaign, as it has been codenamed, has not been attributed to any particular threat actor.
In November and December 2023, there were two waves of the disinformation campaign, with email messages containing PDF attachments and information about food shortages, drug shortage, and heating interruptions.
At least a few hundred Ukrainian recipients, including the government, energy companies, and individuals, were the target of the November wave. The process for making the target list is currently unknown.
In a report shared with The Hacker News, ESET noted that the email’s content is about drug shortages and the PDF is misusing the Ministry of Health of Ukraine logo, despite the fact that it was sent from an email address that purports to be the ministry of agricultural policy and food of the Ukraine.
” The attackers may have made a mistake, or at the very least, it shows they did n’t care about every little thing.”
Due to the fact that all of the messages are in Ukrainian, the second disinformation email campaign, which started on December 25, 2023, is notable for broadening its target audience beyond Ukraine to include Ukrainian speakers in other European countries.
While wishing recipients a joyous holiday season, these messages also took on darker tones, suggesting that they amputate one of their arms or legs in order to avoid being deployed in the military. The email reads,” A few minutes of suffering, but then a happy life.”
Infonotification [. ] was one of the domains that ESET claimed was used to distribute phishing emails in December 2023. Beginning on January 7, 2024, com also started sending hundreds of spam messages that pointed potential customers to a fictitious Canadian pharmacy website.
Although the exact reason why this email server was used to spread a pharmacy scam is unknown, it is believed that the threat actors decided to monetize their infrastructure in order to make money after learning that defenders had found their domains.
According to the company,” Operation Texonto demonstrates yet another application of technology to try to sway the war.”
The development follows Meta’s removal of three networks from China, Myanmar, and Ukraine that engaged in coordinated inauthentic behavior ( CIB ) across its platforms in its quarterly Adversarial Threat Report.
Despite the fact that none of the networks were Russian, engagement has decreased by 94 % and posting volumes by Russian state-controlled media have fallen by 55 % since pre-war levels, according to social media analytics firm Graphika.
Since the start of the war,” Russian state media outlets have increased their focus on non-political infotainment content and self-promotional narratives about Russia,” according to the report. After several Western nations blocked the outlets in 2022,” this could reflect a wider off-platform effort to cater to domestic Russian audiences.”