Following last week’s disruption by law enforcement, the LockBit ransomware gang is once more launching attacks using updated encryptors and ransom notes that link to new servers.
In response to the LockBit ransomware operation, the NCA, FBI, and Europol organized a coordinated disruption known as” Operation Cronos.”
In an embarrassing moment for LockBit, law enforcement turned the ransomware gang’s data leak site into a police press portal as part of this operation.
Source: BleepingComputer
Soon after, LockBit created a new data leak website and wrote to the FBI in a lengthy note claiming that law enforcement had used a PHP bug to breach their servers.
To stop law enforcement from carrying out operation-wide attacks and gaining access to decryptors, they promised to return instead of rebranding.
LockBit encryptors that have been updated for attacks
With new encryptors and an infrastructure set up for data leak and negotiation sites, LockBit appears to be launching attacks once more as of yesterday.
The ransomware gang updated their encryptor’s ransom notes with Tor URLs for the gang’s new infrastructure as first reported by , Zscaler. Later, BleepingComputer discovered updated ransom notes in samples of the encryptors that were uploaded to VirusTotal yesterday [Sample ] and today [Sample ] ( shared by Malware HunterTeam ).
BleepingComputer also confirmed that only victims of new attacks can use the operation’s negotiation servers, which are still operational.
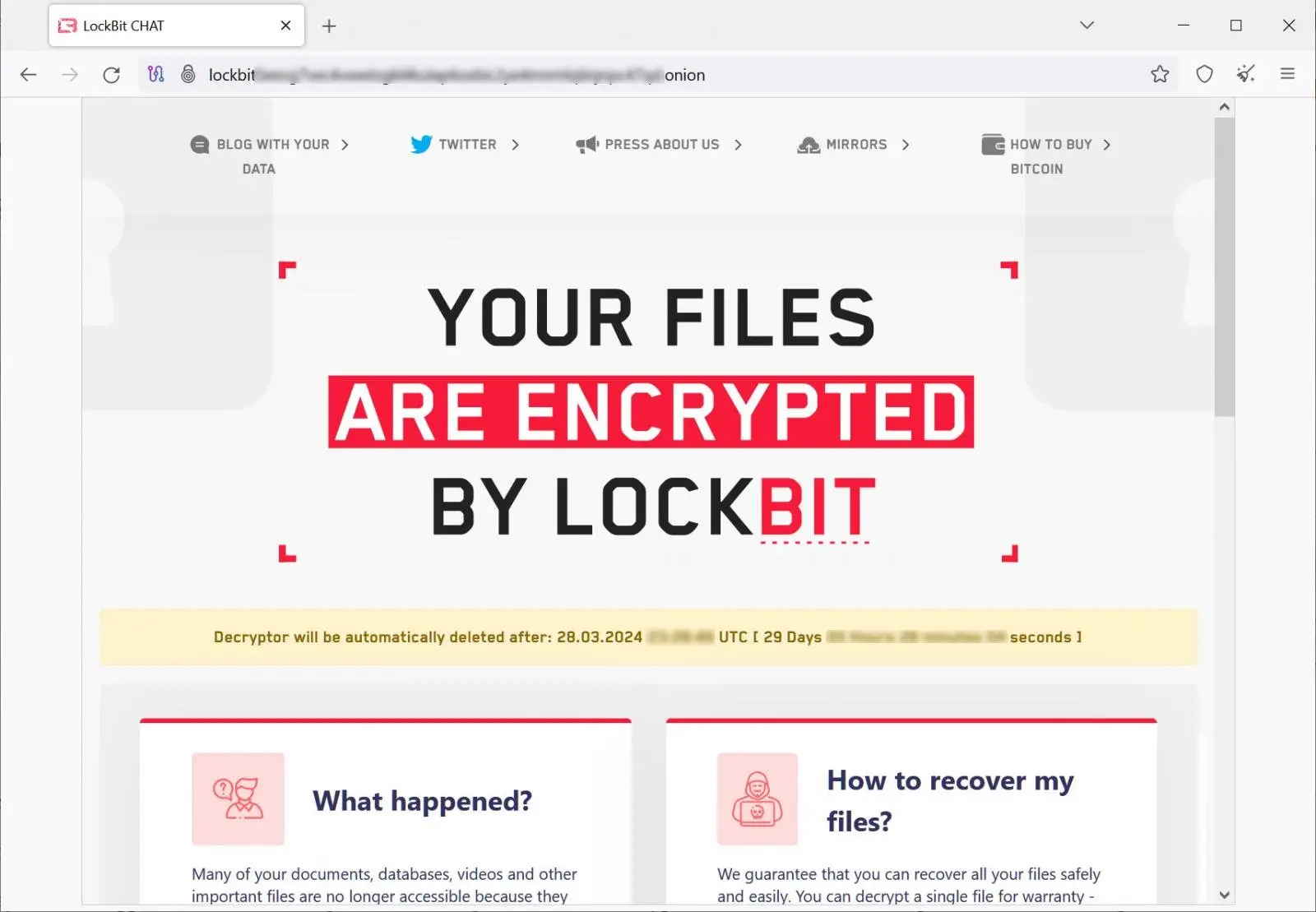
Source: BleepingComputer
Around 180 affiliates were working with the ransomware operation to carry out attacks at the time of LockBit’s takedown.
One has publicly criticized the Ransomware as a Service operation on X, but it’s not known how many are still using it.
However, LockBit claims that they are currently looking to add experienced pentesters to their operation, which will likely result in more attacks in the near future.
It’s unknown whether this is a grand plan for LockBit to gradually fade away and rebrand, as we saw with Conti. However, it’s safer to assume that LockBit will continue to be a threat for the time being.











