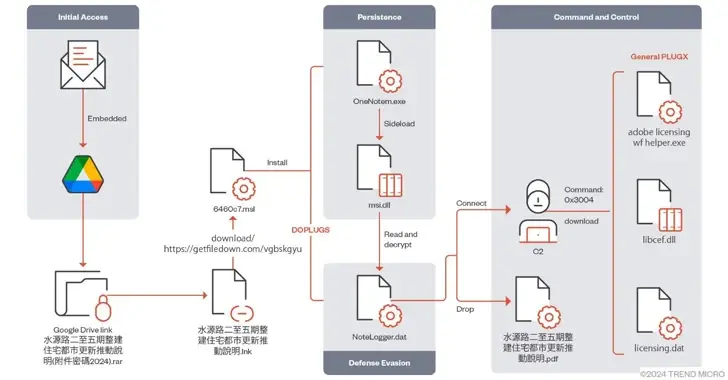
Using a variant of the PlugX ( also known as Korplug) backdoor called DOPLUGS, the China-linked threat actor Mustang Panda has attacked several Asian nations.
According to Trend Micro researchers Sunny Lu and Pierre Lee, the customized version of PlugX malware differs from the general version, which includes a finished backdoor command module and is only used for downloading the latter.
DOPLUGS have primarily targeted Taiwan, Vietnam, Hong Kong, India, Japan, Malaysia, Mongolia, and even China.
The Mustang Panda also goes by the names BASIN, Bronze President, Camaro Dragon, Earth Preta, HoneyMyte, RedDelt, and Red Lich, as well as Stately Taurus, TA416 and TEMP. PlugX is one of the Panda’s main tools. Hex. Although it was first discovered in 2017, it has been known to be active since at least 2012.
The trade of the threat actor involves running carefully crafted spear-phishing campaigns that are intended to deliver a variety of unique malware. Additionally, it has a history of using its own unique PlugX variants, including RedDelta, Thor, Hodur, and DOPLUGS ( which are part of the SmugX campaign ) since 2018.
In order to side-load a dynamic-link library ( DLL), which in turn decrypts and executes PlugX, compromise chains secretly unpack an authentic, signed executable that is vulnerable to DLL side loading while also serving as the recipient’s decoy document. This is known as phishing messages.
To connect to a server controlled by Mustang Panda, the PlugX malware then retrieves the Cobalt Strike Beacon or Poison Ivy remote access Trojan (RAT ).
Lab52 discovered a Mustang Panda campaign in December 2023 that used DOPLUGS to target Taiwanese political, diplomatic, and governmental organizations.
According to Lab52, the malicious DLL is written in the Nim programming language. In contrast to earlier versions that used Windows Cryptsp, this new variant decrypts PlugX using its own implementation of the RC4 algorithm. dll library.
A downloader with four backdoor commands called DOPLUGS, which Secureworks first identified in September 2022, is designed to download the PlugX malware’s general type.
According to Trend Micro, DOPLUGS samples were also found to be integrated with the KillSomeOne plugin, which is used to distribute malware, gather data, and steal documents from USB drives.
In addition to supporting the ability to run commands and download next-stage malware from an actor-controlled server, this variant includes an extra launcher component that executes the legitimate executable to perform DLL-sideloading.
It’s important to note that Avira discovered a customized PlugX variant in January 2020 as part of attacks on Hong Kong and Vietnam that included the KillSomeOne module and was intended for USB distribution.
According to the researchers, this demonstrates how Earth Preta has been improving its tools over time, constantly adding new features and functionalities. ” Especially in Europe and Asia, the group is still very active.”